SX1276 Shield based Applications
Dependencies: X_NUCLEO_IKS01A1 LoRaWAN-lib SX1276Lib mbed
LoRaWAN-SX1276-Application Demo uses SX1276MB1LAS mbed component shield on a nucleo board platform to demonstrate a Class-A LoRaWAN device in the 915MHz ISM band for North American region. It uses the LoRaWAN-lib and SX1276Lib libraries.
Comissioning.h (LoRaWAN Network Configuration)
The end-device can be activated in one of the two ways:
Over the Air (OTA) activation can be enabled as shown in the figure below.
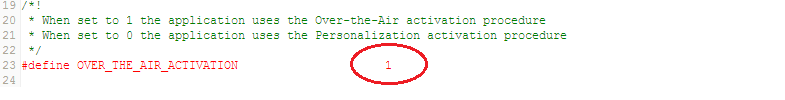
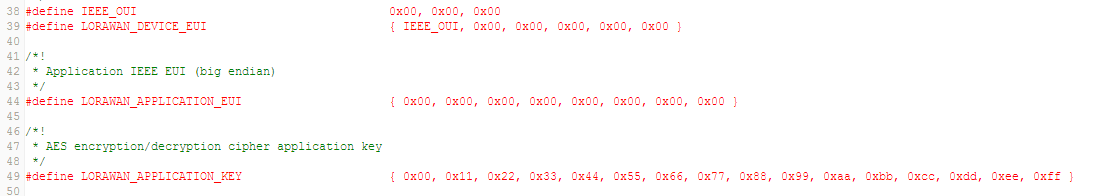
The end-device must be configured with the following parameters:
LORAWAN_DEVICE_EUI(8 Bytes) : Fist 3 Bytes is the Organizationally Unique Identifier (OUI) followed by 5 bytes of unique ID. If not defined by user, then the firmware automatically assigns one to the end-deviceLORAWAN_APPLICATION_EUI(8 Bytes)LORAWAN_APPLICATION_KEY(or DEVKEY) (16 Bytes)
Activation by Personalization (ABP) can be enabled as shown in the figure below.
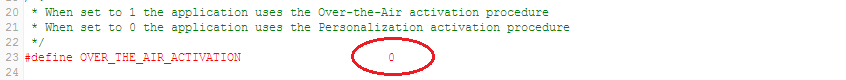
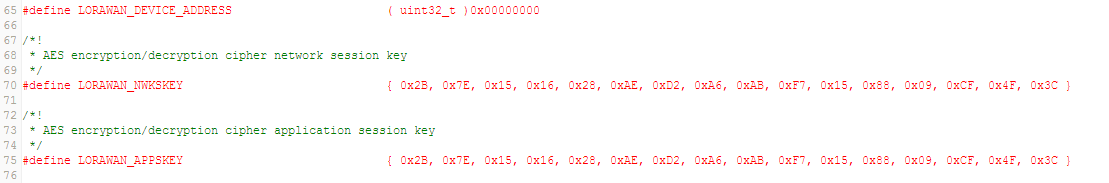
The end-device must be configured with the following parameters:
LORAWAN_DEVICE_ADDRESS(4 Bytes) : If not defined by user, then the firmware automatically assigns one to the end-deviceLORAWAN_NWKSKEY(16 Bytes)LORAWAN_APPSKEY(16 Bytes)
Config.h (LoRaWAN Communication Parameters)
- Mode of Operation : Hybrid
If the end-device needs to be configured to operate over 8-channels, then
Hybrid Modeneeds to be enabled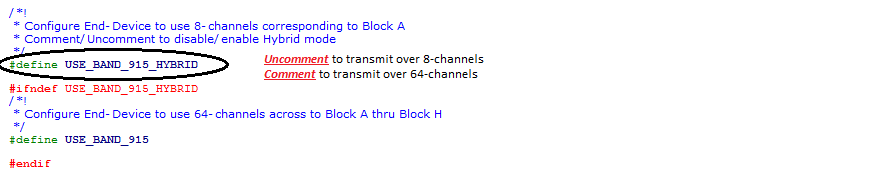
- Mode of Operation : Frequency Hop
If the end-device needs to be configured to operate over 64-channels, then
Hybrid Modeneeds to be disabled
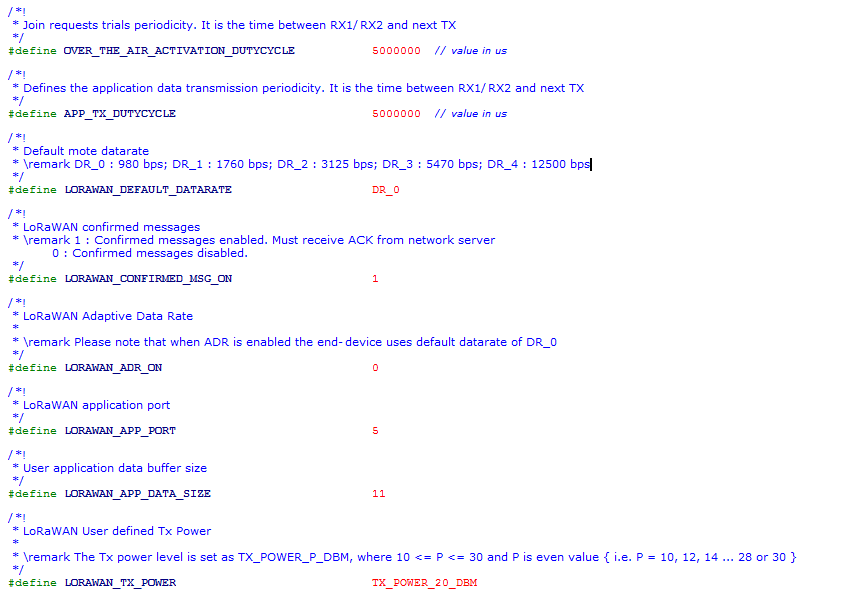
- Delay between successive JOIN REQUESTs :
The delay between successive Join Requests (until the end-device joins the network) can be configured using the parameter
OVER_THE_AIR_ACTIVATION_DUTYCYCLE
- Inter-Frame Delay :
One can change the delay between each frame transmission using
APP_TX_DUTYCYCLEIt is advisable thatAPP_TX_DUTYCYCLEis greater than or equal to 3sec.
- Data Rate :
The data rate can be configured as per LoRaWAN specification using the paramter
LORAWAN_DEFAULT_DATARATE. The range of values are DR_0, DR_1, DR_2, DR_3 and DR_4
- Confirmed/Unconfirmed Messages :
The uplink message or payload can be chosen to be confirmed or unconfirmed using the parameter
LORAWAN_CONFIRMED_MSG_ON. When set to 1, the transmitted messages need to be confirmed with anACKby the network server in the subsequent RX window. When set to 0, noACKis requested.
- ADR ON/OFF :
The ADR can be enabled or disabled using the parameter
LORAWAN_ADR_ON. When set to 1, ADR is enabled and disabled when set to 0.
- Application Port :
The application port can be set using parameter
LORAWAN_APP_PORT. A few examples are associated to specific Application Port, and are defined in Config.h
- Payload Length :
The lenght of the payload (in bytes) to be transmitted can be configured using
LORAWAN_APP_DATA_SIZE
- Transmit Power :
The transmit power can be configured using
LORAWAN_TX_POWER(LoRaMAC verifies if the set power is compliant with the LoRaWAN spec and FCC guidelines)
The baud-rate for serial terminal display is 115200
Diff: system/crypto/cmac.cpp
- Revision:
- 0:42863a11464a
diff -r 000000000000 -r 42863a11464a system/crypto/cmac.cpp
--- /dev/null Thu Jan 01 00:00:00 1970 +0000
+++ b/system/crypto/cmac.cpp Fri Aug 26 19:36:35 2016 +0000
@@ -0,0 +1,153 @@
+/**************************************************************************
+Copyright (C) 2009 Lander Casado, Philippas Tsigas
+
+All rights reserved.
+
+Permission is hereby granted, free of charge, to any person obtaining
+a copy of this software and associated documentation files
+(the "Software"), to deal with the Software without restriction, including
+without limitation the rights to use, copy, modify, merge, publish,
+distribute, sublicense, and/or sell copies of the Software, and to
+permit persons to whom the Software is furnished to do so, subject to
+the following conditions:
+
+Redistributions of source code must retain the above copyright notice,
+this list of conditions and the following disclaimers. Redistributions in
+binary form must reproduce the above copyright notice, this list of
+conditions and the following disclaimers in the documentation and/or
+other materials provided with the distribution.
+
+In no event shall the authors or copyright holders be liable for any special,
+incidental, indirect or consequential damages of any kind, or any damages
+whatsoever resulting from loss of use, data or profits, whether or not
+advised of the possibility of damage, and on any theory of liability,
+arising out of or in connection with the use or performance of this software.
+
+THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS
+OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
+FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
+CONTRIBUTORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
+LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING
+FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
+DEALINGS WITH THE SOFTWARE
+
+*****************************************************************************/
+//#include <sys/param.h>
+//#include <sys/systm.h>
+#include <stdint.h>
+#include "aes.h"
+#include "cmac.h"
+#include "utilities.h"
+
+#define LSHIFT(v, r) do { \
+ int32_t i; \
+ for (i = 0; i < 15; i++) \
+ (r)[i] = (v)[i] << 1 | (v)[i + 1] >> 7; \
+ (r)[15] = (v)[15] << 1; \
+ } while (0)
+
+#define XOR(v, r) do { \
+ int32_t i; \
+ for (i = 0; i < 16; i++) \
+ { \
+ (r)[i] = (r)[i] ^ (v)[i]; \
+ } \
+ } while (0) \
+
+
+void AES_CMAC_Init(AES_CMAC_CTX *ctx)
+{
+ memset1(ctx->X, 0, sizeof ctx->X);
+ ctx->M_n = 0;
+ memset1(ctx->rijndael.ksch, '\0', 240);
+}
+
+void AES_CMAC_SetKey(AES_CMAC_CTX *ctx, const uint8_t key[AES_CMAC_KEY_LENGTH])
+{
+ //rijndael_set_key_enc_only(&ctx->rijndael, key, 128);
+ aes_set_key( key, AES_CMAC_KEY_LENGTH, &ctx->rijndael);
+}
+
+void AES_CMAC_Update(AES_CMAC_CTX *ctx, const uint8_t *data, uint32_t len)
+{
+ uint32_t mlen;
+ uint8_t in[16];
+
+ if (ctx->M_n > 0) {
+ mlen = MIN(16 - ctx->M_n, len);
+ memcpy1(ctx->M_last + ctx->M_n, data, mlen);
+ ctx->M_n += mlen;
+ if (ctx->M_n < 16 || len == mlen)
+ return;
+ XOR(ctx->M_last, ctx->X);
+ //rijndael_encrypt(&ctx->rijndael, ctx->X, ctx->X);
+ aes_encrypt( ctx->X, ctx->X, &ctx->rijndael);
+ data += mlen;
+ len -= mlen;
+ }
+ while (len > 16) { /* not last block */
+
+ XOR(data, ctx->X);
+ //rijndael_encrypt(&ctx->rijndael, ctx->X, ctx->X);
+
+ memcpy1(in, &ctx->X[0], 16); //Bestela ez du ondo iten
+ aes_encrypt( in, in, &ctx->rijndael);
+ memcpy1(&ctx->X[0], in, 16);
+
+ data += 16;
+ len -= 16;
+ }
+ /* potential last block, save it */
+ memcpy1(ctx->M_last, data, len);
+ ctx->M_n = len;
+}
+
+void AES_CMAC_Final(uint8_t digest[AES_CMAC_DIGEST_LENGTH], AES_CMAC_CTX *ctx)
+{
+ uint8_t K[16];
+ uint8_t in[16];
+ /* generate subkey K1 */
+ memset1(K, '\0', 16);
+
+ //rijndael_encrypt(&ctx->rijndael, K, K);
+
+ aes_encrypt( K, K, &ctx->rijndael);
+
+ if (K[0] & 0x80) {
+ LSHIFT(K, K);
+ K[15] ^= 0x87;
+ } else
+ LSHIFT(K, K);
+
+
+ if (ctx->M_n == 16) {
+ /* last block was a complete block */
+ XOR(K, ctx->M_last);
+
+ } else {
+ /* generate subkey K2 */
+ if (K[0] & 0x80) {
+ LSHIFT(K, K);
+ K[15] ^= 0x87;
+ } else
+ LSHIFT(K, K);
+
+ /* padding(M_last) */
+ ctx->M_last[ctx->M_n] = 0x80;
+ while (++ctx->M_n < 16)
+ ctx->M_last[ctx->M_n] = 0;
+
+ XOR(K, ctx->M_last);
+
+
+ }
+ XOR(ctx->M_last, ctx->X);
+
+ //rijndael_encrypt(&ctx->rijndael, ctx->X, digest);
+
+ memcpy1(in, &ctx->X[0], 16); //Bestela ez du ondo iten
+ aes_encrypt(in, digest, &ctx->rijndael);
+ memset1(K, 0, sizeof K);
+
+}
+