Application example using LoRaWAN-lib MAC layer implementation
Dependencies: mbed LoRaWAN-lib SX1272Lib
LoRaWAN-demo is a ClassA device example project using LoRaWAN-lib and SX1272Lib libraries.
This demo application sends a frame every 4 to 6 seconds (randomly) and displays its current status using a serial port as display(VT100).
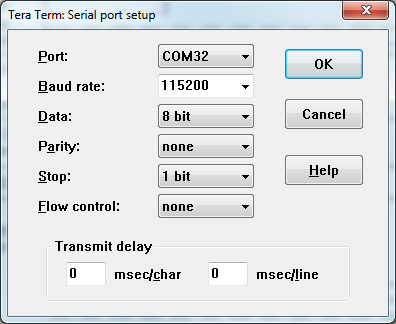
The serial port settings are as shown in below image. To access the serial port settings please click on "Setup" menu and then "Serial port..."
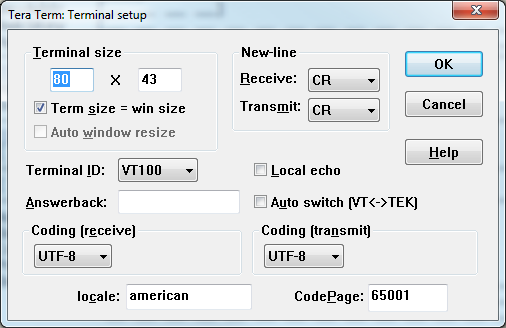
The terminal window should be setup as shown in below image. To access the terminal window settings please click on "Setup" menu and then "Terminal..."
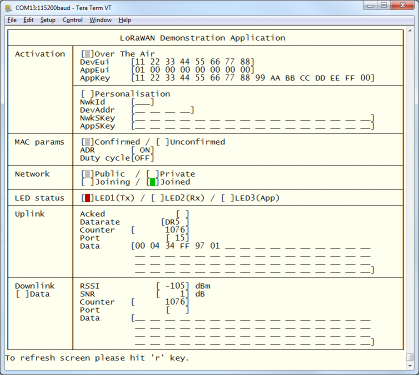
The image below shows the VT100 application status.
The application gives the possibility to either activate the device using
- Over The Air Activation (OTAA)
- Personalization activation (PA)
The activation mode can be adjusted in Comissioning.h by changing the following parameter:
/*! * When set to 1 the application uses the Over-the-Air activation procedure * When set to 0 the application uses the Personalization activation procedure */ #define OVER_THE_AIR_ACTIVATION 1
The application gives the possibility to select which kind of network we are connecting to.
- Public Network (true)
- Private Network (false)
The netork type can be changed as follows:
/*! * Indicates if the end-device is to be connected to a private or public network */ #define LORAWAN_PUBLIC_NETWORK true
OTAA
When OTAA is selected the user must porvide a device EUI, an application EUI and an application key.
These can be adjusted by changing the following parameters:
/*!
* Mote device IEEE EUI (big endian)
*/
#define LORAWAN_DEVICE_EUI { 0x11, 0x22, 0x33, 0x44, 0x55, 0x66, 0x77, 0x88 }
/*!
* Application IEEE EUI (big endian)
*/
#define LORAWAN_APPLICATION_EUI { 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00 }
/*!
* AES encryption/decryption cipher application key
*/
#define LORAWAN_APPLICATION_KEY { 0x2B, 0x7E, 0x15, 0x16, 0x28, 0xAE, 0xD2, 0xA6, 0xAB, 0xF7, 0x15, 0x88, 0x09, 0xCF, 0x4F, 0x3C }
PA
When PA is selected the user must porvide a network ID, a device address, a network session key and an application session key.
These can be adjusted by changing the following parameters:
/*!
* Current network ID
*/
#define LORAWAN_NETWORK_ID ( uint32_t )0
/*!
* Device address on the network (big endian)
*/
#define LORAWAN_DEVICE_ADDRESS ( uint32_t )0x12345678
/*!
* AES encryption/decryption cipher network session key
*/
#define LORAWAN_NWKSKEY { 0x2B, 0x7E, 0x15, 0x16, 0x28, 0xAE, 0xD2, 0xA6, 0xAB, 0xF7, 0x15, 0x88, 0x09, 0xCF, 0x4F, 0x3C }
/*!
* AES encryption/decryption cipher application session key
*/
#define LORAWAN_APPSKEY { 0x2B, 0x7E, 0x15, 0x16, 0x28, 0xAE, 0xD2, 0xA6, 0xAB, 0xF7, 0x15, 0x88, 0x09, 0xCF, 0x4F, 0x3C }
On top of main.c the user has the possibility to tweak some application settings such as:
- Join requests transmission frequency
- Frames transmission frequency
- Application default datarate
- Confirmed or Unconfirmed frames transmission
- ADR (Adaptive Datarate) ON/OFF
- Application port to be used by the transmitted frames
The join requests transmission frequency can be adjusted by changing the follwoing parameter:
/*! * Join requests trials duty cycle. */ #define OVER_THE_AIR_ACTIVATION_DUTYCYCLE 10000000 // 10 [s] value in us
The frame transmission frequency can be adjusted by changing the follwoing parameters:
/*! * Defines the application data transmission duty cycle. 5s, value in [us]. */ #define APP_TX_DUTYCYCLE 5000000 /*! * Defines a random delay for application data transmission duty cycle. 1s, * value in [us]. */ #define APP_TX_DUTYCYCLE_RND 1000000
The frame transmission scheduling is then executed as follows:
if( ScheduleNextTx == true )
{
ScheduleNextTx = false;
// Schedule next packet transmission
TxDutyCycleTime = APP_TX_DUTYCYCLE + randr( -APP_TX_DUTYCYCLE_RND, APP_TX_DUTYCYCLE_RND );
TimerSetValue( &TxNextPacketTimer, TxDutyCycleTime );
TimerStart( &TxNextPacketTimer );
}
The application default datarate can be adjusted by changing the following parameter:
Quote:
When ADR is off this setting is the fixed datarate that will be used by the application.
When ADR is on this setting is the initial datarate used by the application.
/*! * Default mote datarate */ #define LORAWAN_DEFAULT_DATARATE DR_0
The transmitted frame contents will depend on LORAWAN_CONFIRMED_MSG_ON value.
/*! * LoRaWAN confirmed messages */ #define LORAWAN_CONFIRMED_MSG_ON true
- If LORAWAN_CONFIRMED_MSG_ON equals false then the application payload is one byte corresponding to the AppLed state.
- If LORAWAN_CONFIRMED_MSG_ON equals true then the application payload is six bytes corresponding to the AppLed state, Downlink counter (unsigned 16 bits), received RSSI (signed 16 bits) and received SNR (signed 8 bits).
/*!
* \brief Prepares the payload of the frame
*/
static void PrepareTxFrame( uint8_t port )
{
switch( port )
{
case 15:
{
AppData[0] = AppLedStateOn;
if( IsTxConfirmed == true )
{
AppData[1] = LoRaMacDownlinkStatus.DownlinkCounter >> 8;
AppData[2] = LoRaMacDownlinkStatus.DownlinkCounter;
AppData[3] = LoRaMacDownlinkStatus.Rssi >> 8;
AppData[4] = LoRaMacDownlinkStatus.Rssi;
AppData[5] = LoRaMacDownlinkStatus.Snr;
}
}
break;
case 224:
...
}
The ADR enabling/disabling can be adjusted by changing the following parameter:
/*! * LoRaWAN Adaptive Data Rate * * \remark Please note that when ADR is enabled the end-device should be static */ #define LORAWAN_ADR_ON 1
The application port can be adjusted by changing the following parameter:
/*! * LoRaWAN application port */ #define LORAWAN_APP_PORT 15
system/crypto/aes.h
- Committer:
- mluis
- Date:
- 2016-01-07
- Revision:
- 0:45496a70a8a5
File content as of revision 0:45496a70a8a5:
/*
---------------------------------------------------------------------------
Copyright (c) 1998-2008, Brian Gladman, Worcester, UK. All rights reserved.
LICENSE TERMS
The redistribution and use of this software (with or without changes)
is allowed without the payment of fees or royalties provided that:
1. source code distributions include the above copyright notice, this
list of conditions and the following disclaimer;
2. binary distributions include the above copyright notice, this list
of conditions and the following disclaimer in their documentation;
3. the name of the copyright holder is not used to endorse products
built using this software without specific written permission.
DISCLAIMER
This software is provided 'as is' with no explicit or implied warranties
in respect of its properties, including, but not limited to, correctness
and/or fitness for purpose.
---------------------------------------------------------------------------
Issue 09/09/2006
This is an AES implementation that uses only 8-bit byte operations on the
cipher state.
*/
#ifndef AES_H
#define AES_H
#if 1
# define AES_ENC_PREKEYED /* AES encryption with a precomputed key schedule */
#endif
#if 0
# define AES_DEC_PREKEYED /* AES decryption with a precomputed key schedule */
#endif
#if 0
# define AES_ENC_128_OTFK /* AES encryption with 'on the fly' 128 bit keying */
#endif
#if 0
# define AES_DEC_128_OTFK /* AES decryption with 'on the fly' 128 bit keying */
#endif
#if 0
# define AES_ENC_256_OTFK /* AES encryption with 'on the fly' 256 bit keying */
#endif
#if 0
# define AES_DEC_256_OTFK /* AES decryption with 'on the fly' 256 bit keying */
#endif
#define N_ROW 4
#define N_COL 4
#define N_BLOCK (N_ROW * N_COL)
#define N_MAX_ROUNDS 14
typedef uint8_t return_type;
/* Warning: The key length for 256 bit keys overflows a byte
(see comment below)
*/
typedef uint8_t length_type;
typedef struct
{ uint8_t ksch[(N_MAX_ROUNDS + 1) * N_BLOCK];
uint8_t rnd;
} aes_context;
/* The following calls are for a precomputed key schedule
NOTE: If the length_type used for the key length is an
unsigned 8-bit character, a key length of 256 bits must
be entered as a length in bytes (valid inputs are hence
128, 192, 16, 24 and 32).
*/
#if defined( AES_ENC_PREKEYED ) || defined( AES_DEC_PREKEYED )
return_type aes_set_key( const uint8_t key[],
length_type keylen,
aes_context ctx[1] );
#endif
#if defined( AES_ENC_PREKEYED )
return_type aes_encrypt( const uint8_t in[N_BLOCK],
uint8_t out[N_BLOCK],
const aes_context ctx[1] );
return_type aes_cbc_encrypt( const uint8_t *in,
uint8_t *out,
int32_t n_block,
uint8_t iv[N_BLOCK],
const aes_context ctx[1] );
#endif
#if defined( AES_DEC_PREKEYED )
return_type aes_decrypt( const uint8_t in[N_BLOCK],
uint8_t out[N_BLOCK],
const aes_context ctx[1] );
return_type aes_cbc_decrypt( const uint8_t *in,
uint8_t *out,
int32_t n_block,
uint8_t iv[N_BLOCK],
const aes_context ctx[1] );
#endif
/* The following calls are for 'on the fly' keying. In this case the
encryption and decryption keys are different.
The encryption subroutines take a key in an array of bytes in
key[L] where L is 16, 24 or 32 bytes for key lengths of 128,
192, and 256 bits respectively. They then encrypts the input
data, in[] with this key and put the reult in the output array
out[]. In addition, the second key array, o_key[L], is used
to output the key that is needed by the decryption subroutine
to reverse the encryption operation. The two key arrays can
be the same array but in this case the original key will be
overwritten.
In the same way, the decryption subroutines output keys that
can be used to reverse their effect when used for encryption.
Only 128 and 256 bit keys are supported in these 'on the fly'
modes.
*/
#if defined( AES_ENC_128_OTFK )
void aes_encrypt_128( const uint8_t in[N_BLOCK],
uint8_t out[N_BLOCK],
const uint8_t key[N_BLOCK],
uint8_t o_key[N_BLOCK] );
#endif
#if defined( AES_DEC_128_OTFK )
void aes_decrypt_128( const uint8_t in[N_BLOCK],
uint8_t out[N_BLOCK],
const uint8_t key[N_BLOCK],
uint8_t o_key[N_BLOCK] );
#endif
#if defined( AES_ENC_256_OTFK )
void aes_encrypt_256( const uint8_t in[N_BLOCK],
uint8_t out[N_BLOCK],
const uint8_t key[2 * N_BLOCK],
uint8_t o_key[2 * N_BLOCK] );
#endif
#if defined( AES_DEC_256_OTFK )
void aes_decrypt_256( const uint8_t in[N_BLOCK],
uint8_t out[N_BLOCK],
const uint8_t key[2 * N_BLOCK],
uint8_t o_key[2 * N_BLOCK] );
#endif
#endif
 SX1272MB2xAS / SX1272MB2DAS
SX1272MB2xAS / SX1272MB2DAS