AWS IoT from Mbed OS device
Now Arm releases official example here: https://github.com/ARMmbed/mbed-os-example-for-aws This page is not well maintained, kept just for an archive. Please use the official example.
This page introduces an example program connecting to AWS IoT from a Mbed device with MQTT over TLS.
Project Page is here: https://os.mbed.com/users/coisme/code/Mbed-to-AWS-IoT/
Program is tested on these platforms:
- FRDM-K64F (K64F)
- STM32L4 Discovery kit IoT node (DISCO_L475VG_IOT01A)
- GR-PEACH (RZ_A1H)
Prepare AWS IoT
Go to the IoT Core.
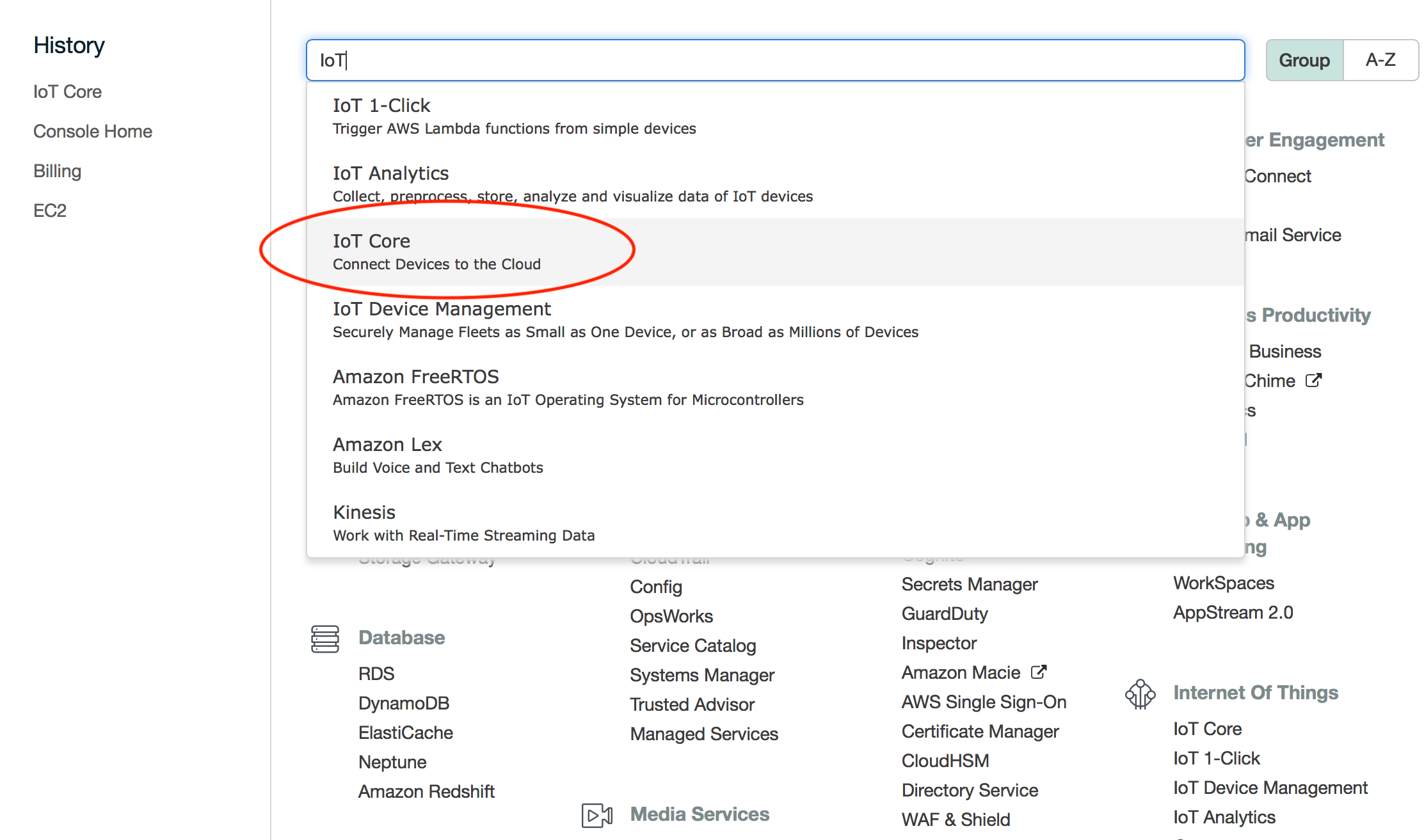
Create Policy
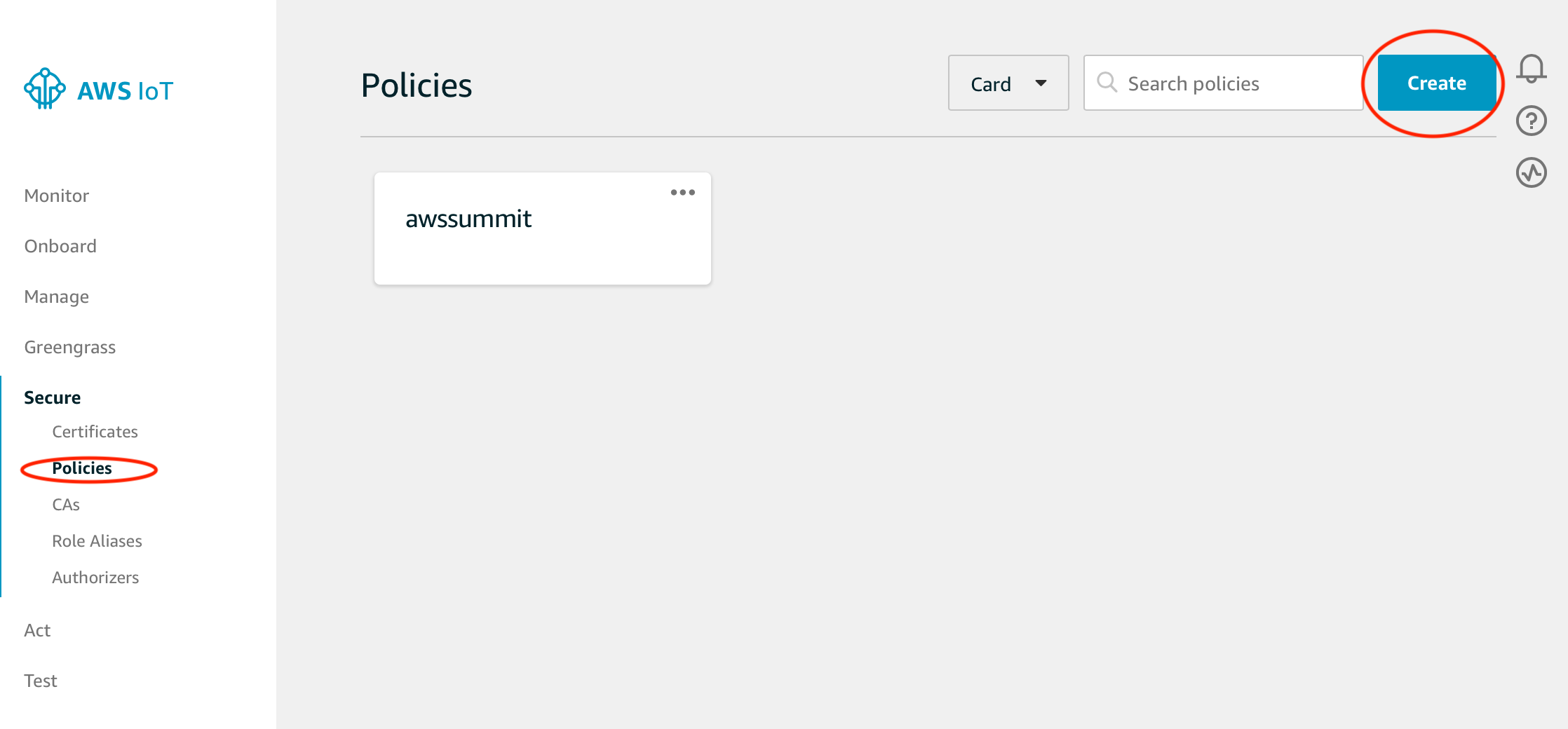
First, create a policy. From the left side menu, select Secure > Policies. Then, click Create button.
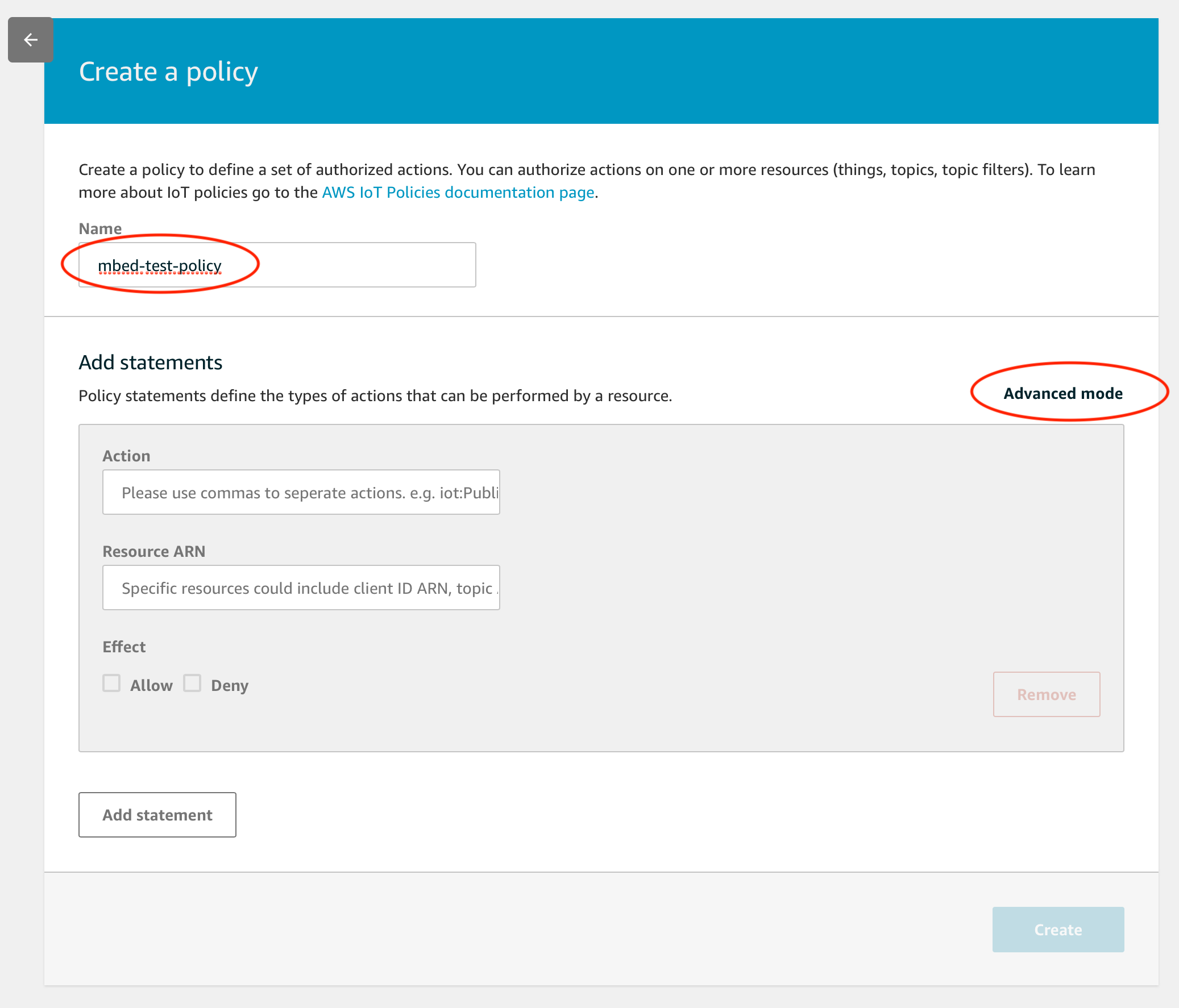
Input Name anything you like. Then Click Advanced Mode.
Replace the text field with the texts below. Then click the Create button.
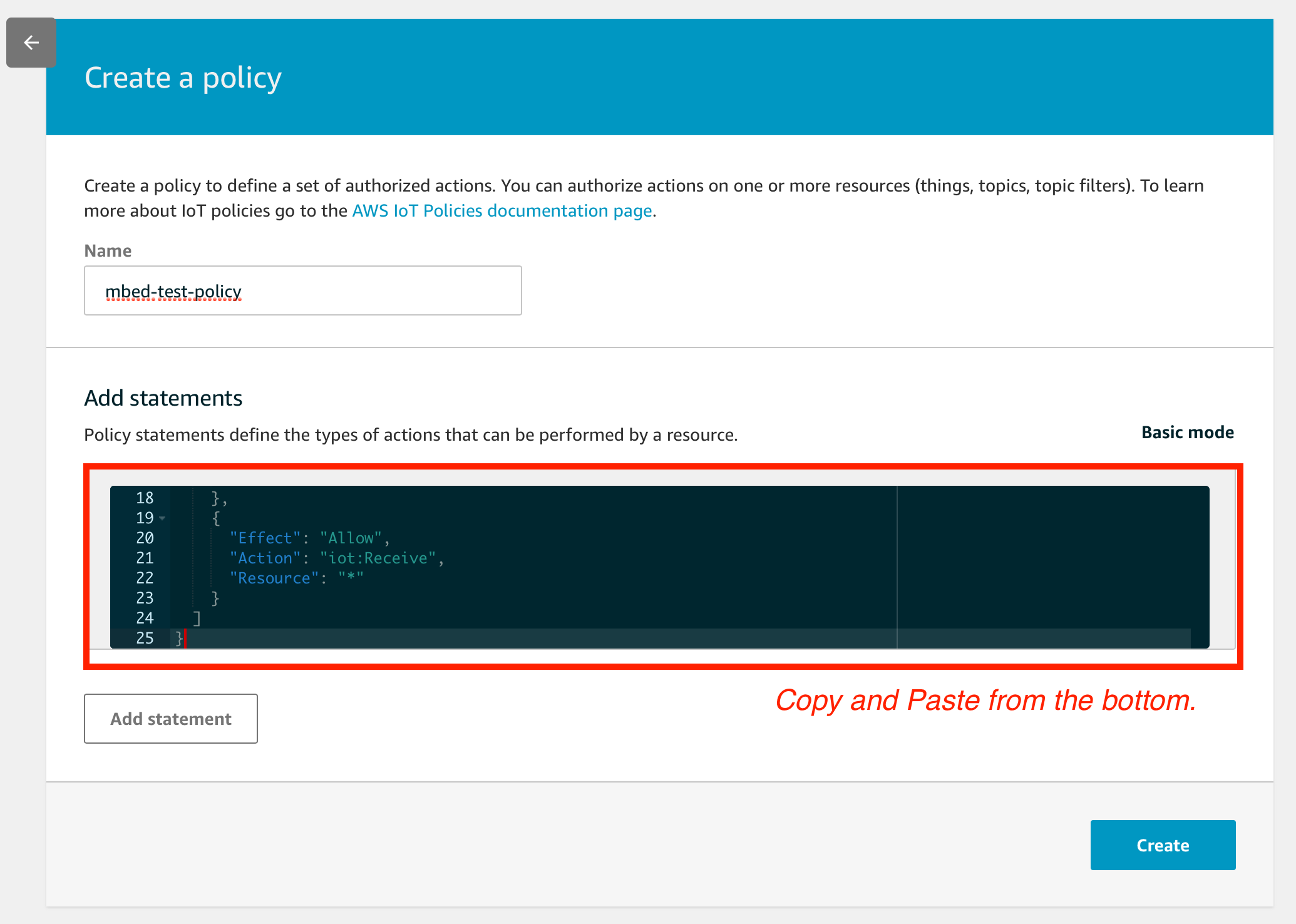
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "iot:Connect",
"Resource": "*"
},
{
"Effect": "Allow",
"Action": "iot:Publish",
"Resource": "*"
},
{
"Effect": "Allow",
"Action": "iot:Subscribe",
"Resource": "*"
},
{
"Effect": "Allow",
"Action": "iot:Receive",
"Resource": "*"
}
]
}
Add an IoT device
Next, adds an IoT device, called a thing. From the left menu, click Manage > Things. Then click Create button at the right top corner.
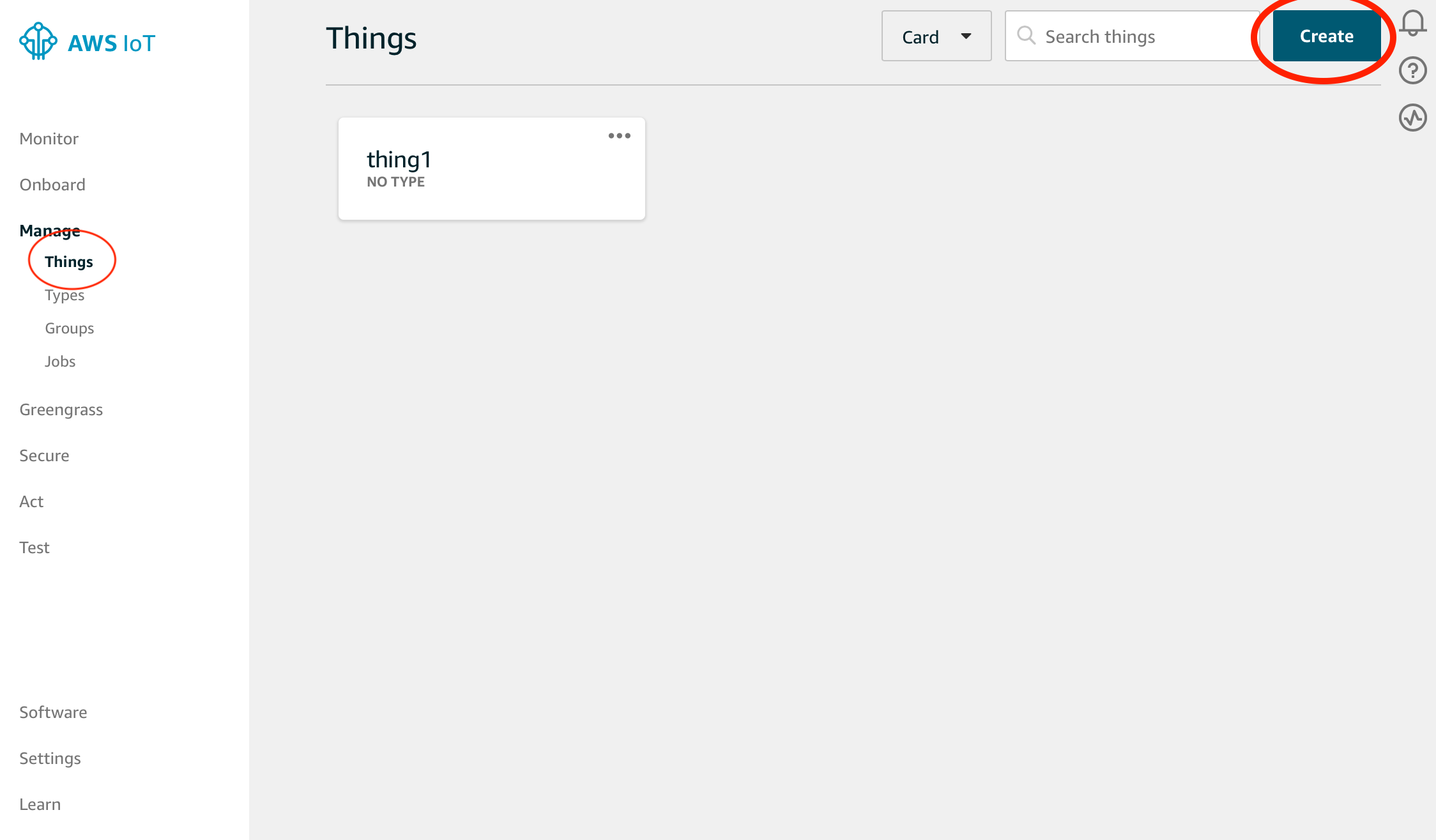
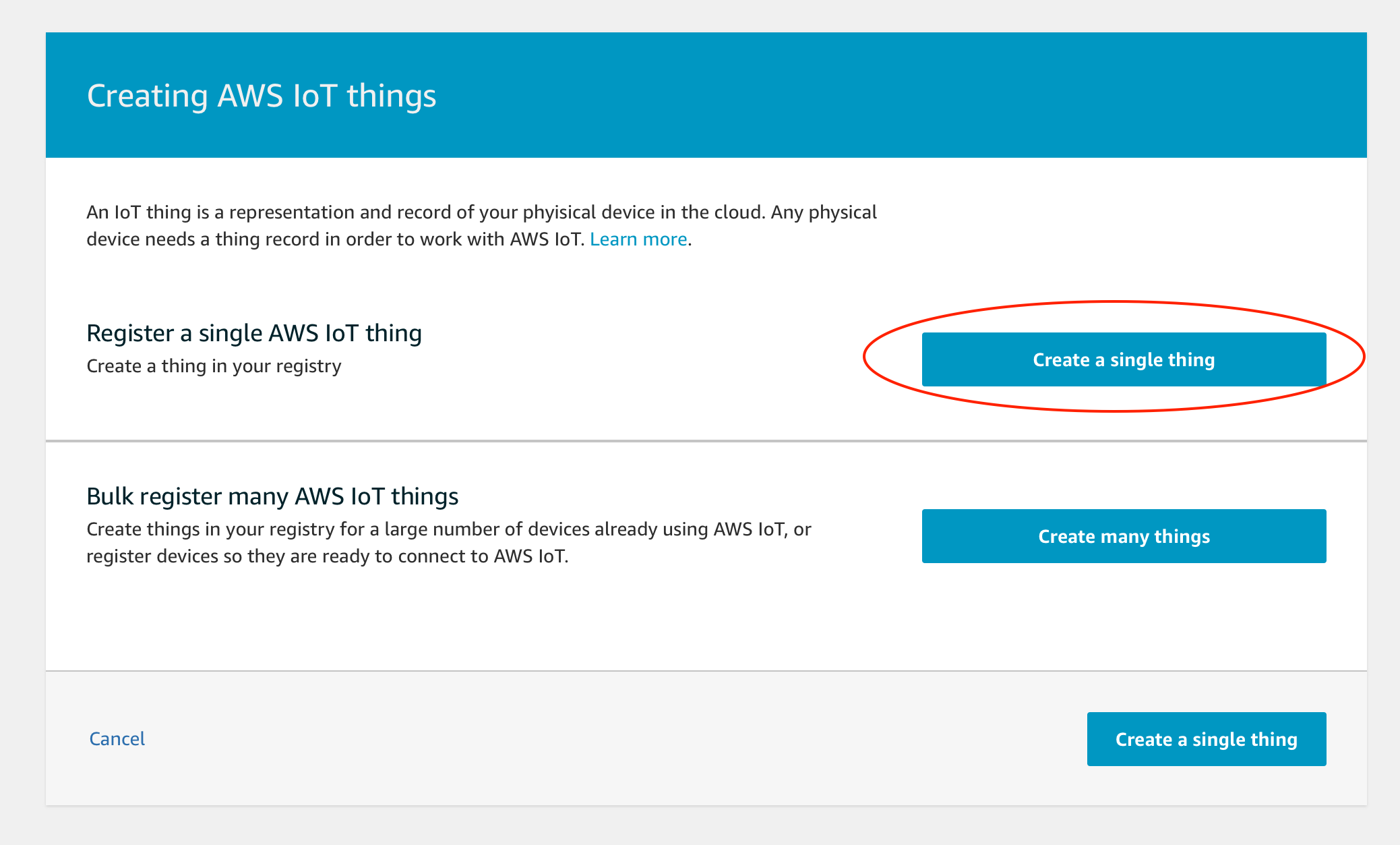
Click Create a single thing button.
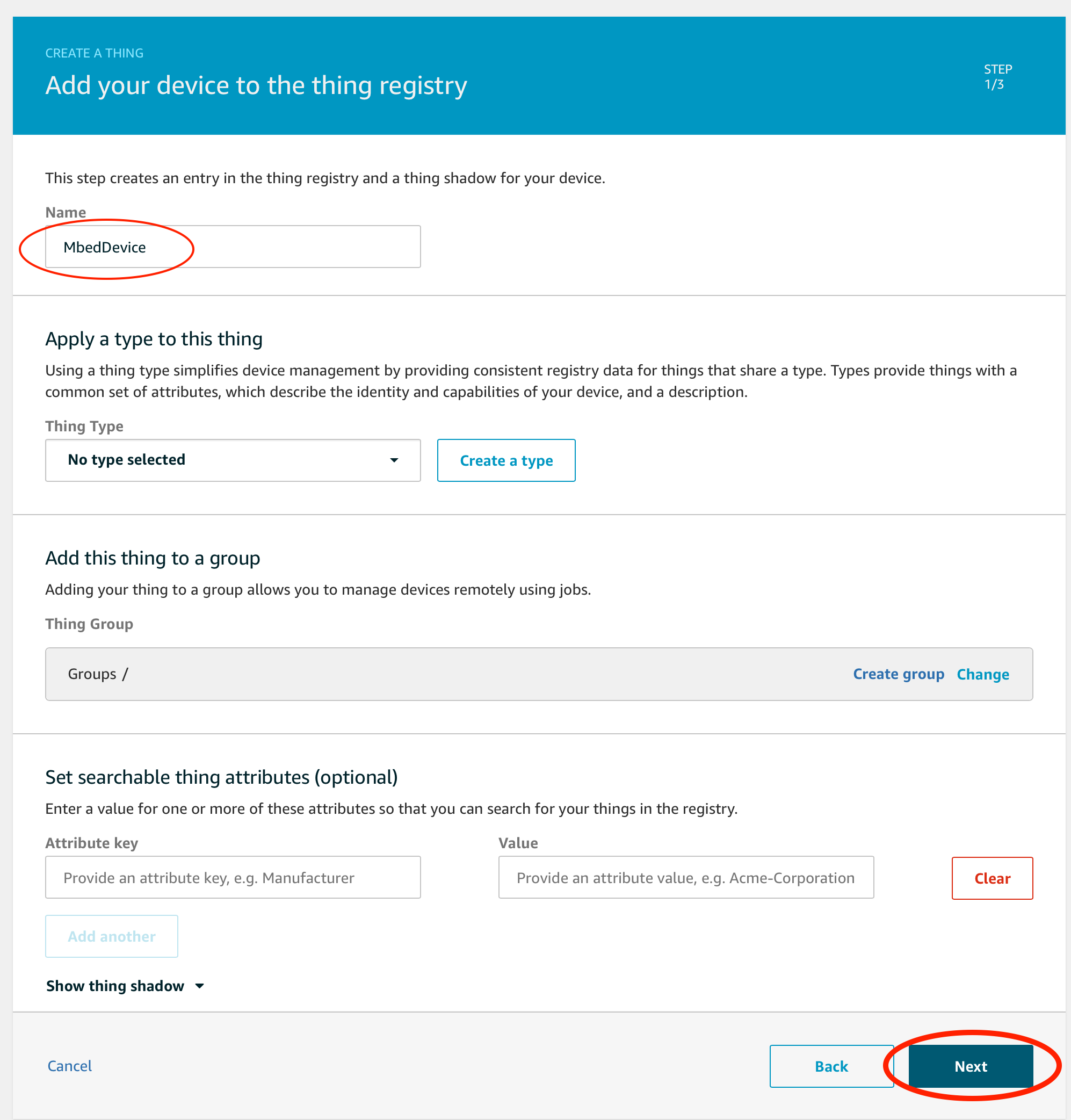
Input Name anything you like. Then click Next button at the right bottom corner.
Click Create certificate button.
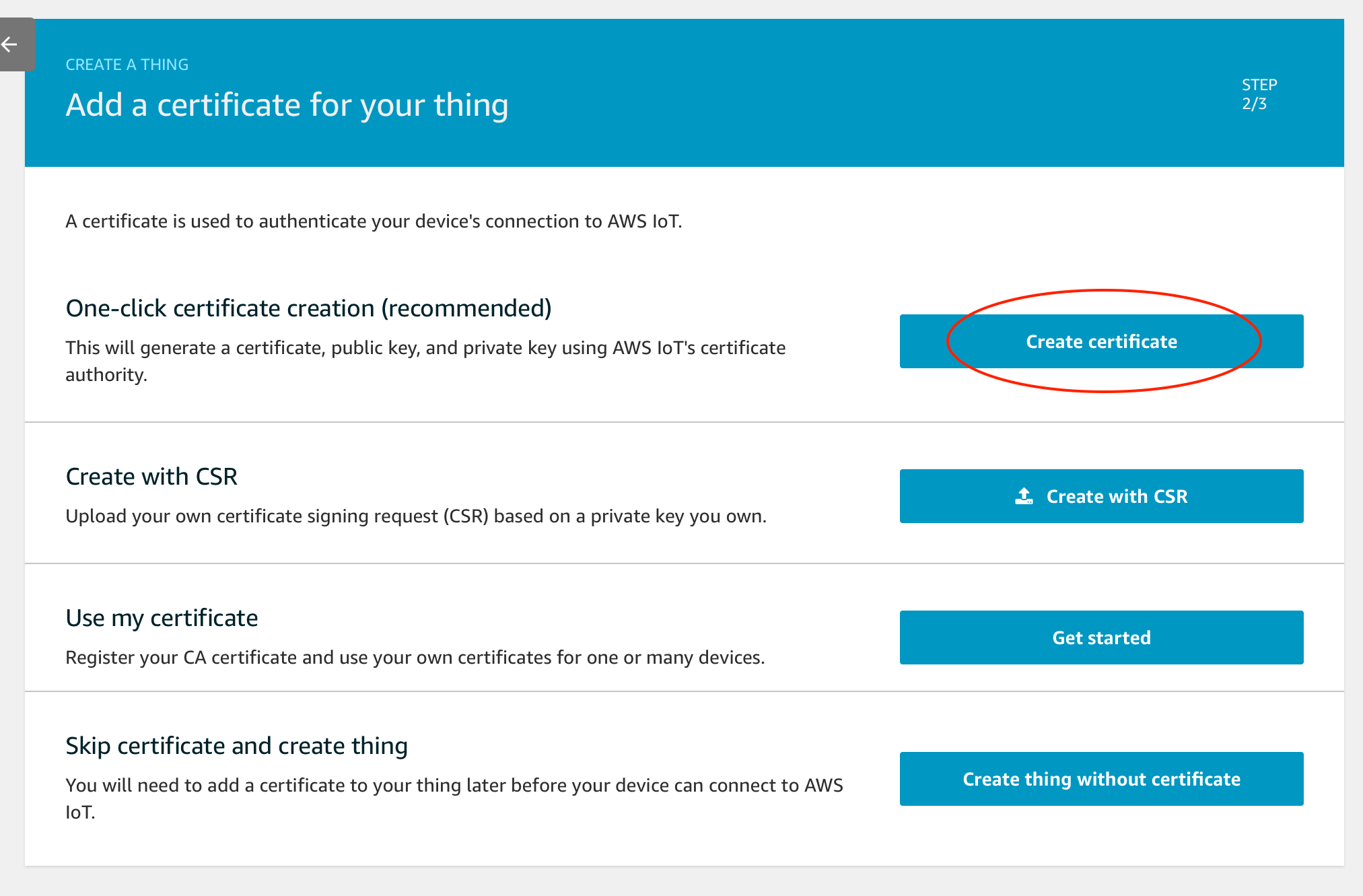
Certificates are created.
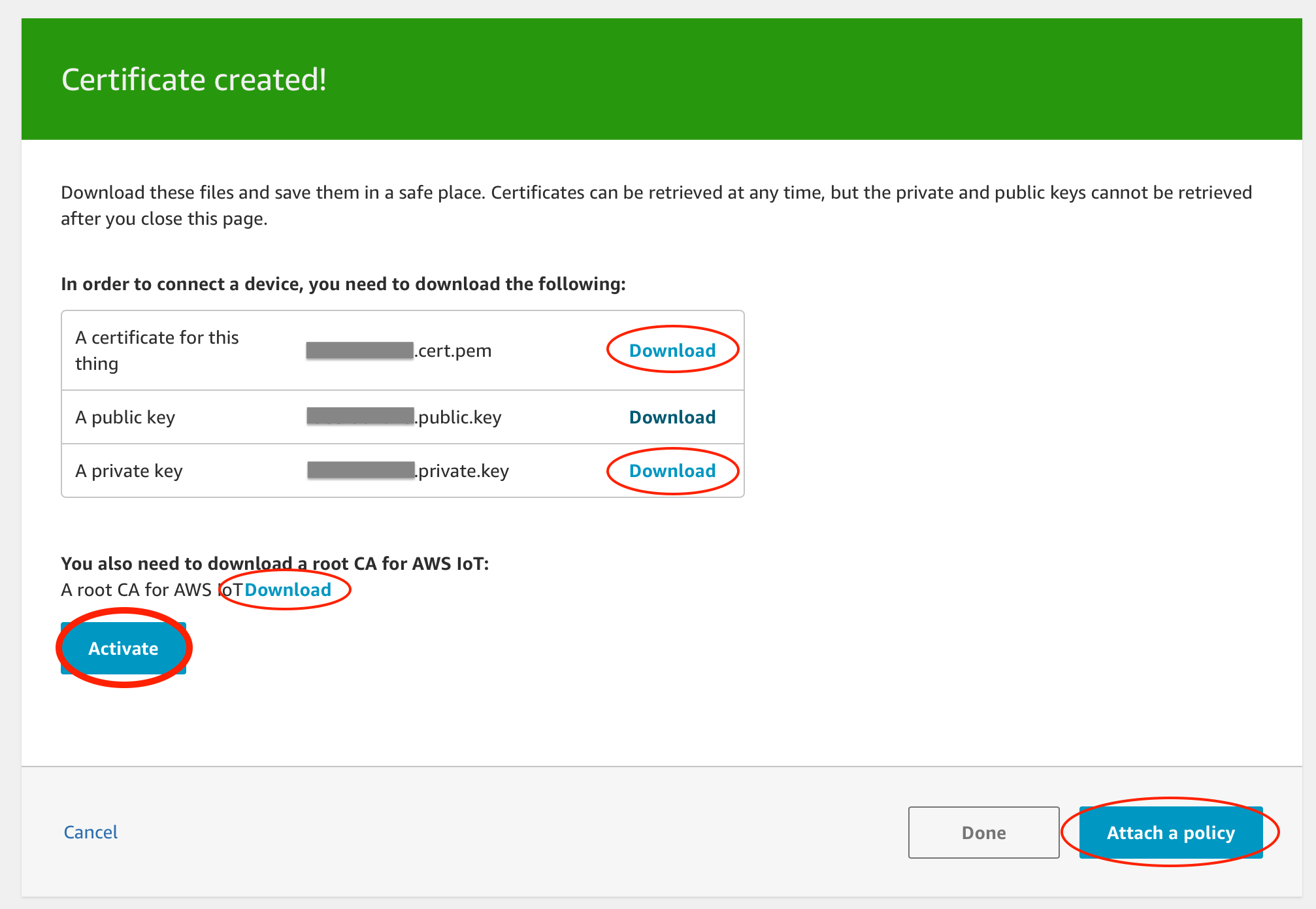
Download these 3 files:
- A certificate for this thing (*.cert.pem)
- A private key (*.private.key)
- Root CA for AWS IoT (Save as rootCA.pem) - Choose RSA 2048 bit key: Amazon Root CA 1
Save them in your local machine. Don't share the private key file (*.private.key) with anyone. In addition, don't forget to click Activate button to enable this certificate. Then, click Attach a policy button.
Choose the policy which made in the previous section and click Register Thing button.
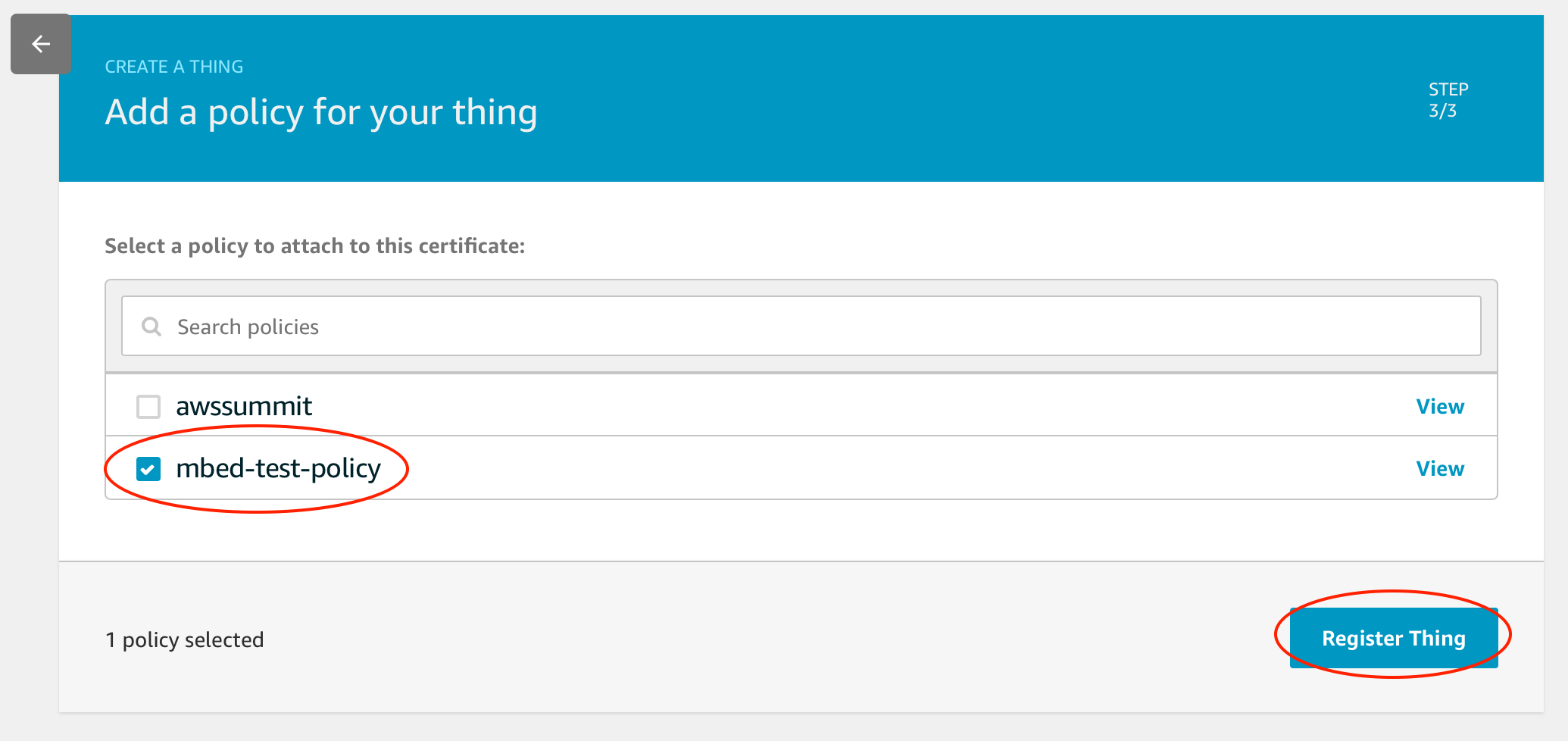
That's it!
Build Project
Let's build the example project.
Import
First, you need to import the example project into your workspace. Visit the page below and click Import into Compiler. Then the program will be imported into your online compiler.
https://os.mbed.com/users/coisme/code/Mbed-to-AWS-IoT/

Modify Parameters
Parameters needs to be set are in MQTT_server_setting.h.
MQTT_server_setting.h
#ifndef __MQTT_SERVER_SETTING_H__ #define __MQTT_SERVER_SETTING_H__ const char MQTT_SERVER_HOST_NAME[] = "<< REPLACE_HERE >>"; const char MQTT_CLIENT_ID[] = "<< REPLACE_HERE >>"; const char MQTT_USERNAME[] = "<< REPLACE_HERE >>"; const char MQTT_PASSWORD[] = "<< REPLACE_HERE >>"; const char MQTT_TOPIC_PUB[] = "<< REPLACE_HERE >>"; const char MQTT_TOPIC_SUB[] = "<< REPLACE_HERE >>"; const int MQTT_SERVER_PORT = 8883; /* * Root CA certificate here in PEM format. * "-----BEGIN CERTIFICATE-----\n" * ... * "-----END CERTIFICATE-----\n"; */ const char SSL_CA_PEM[] = NULL; /* * (optional) Client certificate here in PEM format. * Set NULL if you don't use. * "-----BEGIN CERTIFICATE-----\n" * ... * "-----END CERTIFICATE-----\n"; */ const char* SSL_CLIENT_CERT_PEM = NULL; /* * (optional) Client private key here in PEM format. * Set NULL if you don't use. * "-----BEGIN RSA PRIVATE KEY-----\n" * ... * "-----END RSA PRIVATE KEY-----\n"; */ const char* SSL_CLIENT_PRIVATE_KEY_PEM = NULL; #endif /* __MQTT_SERVER_SETTING_H__ */
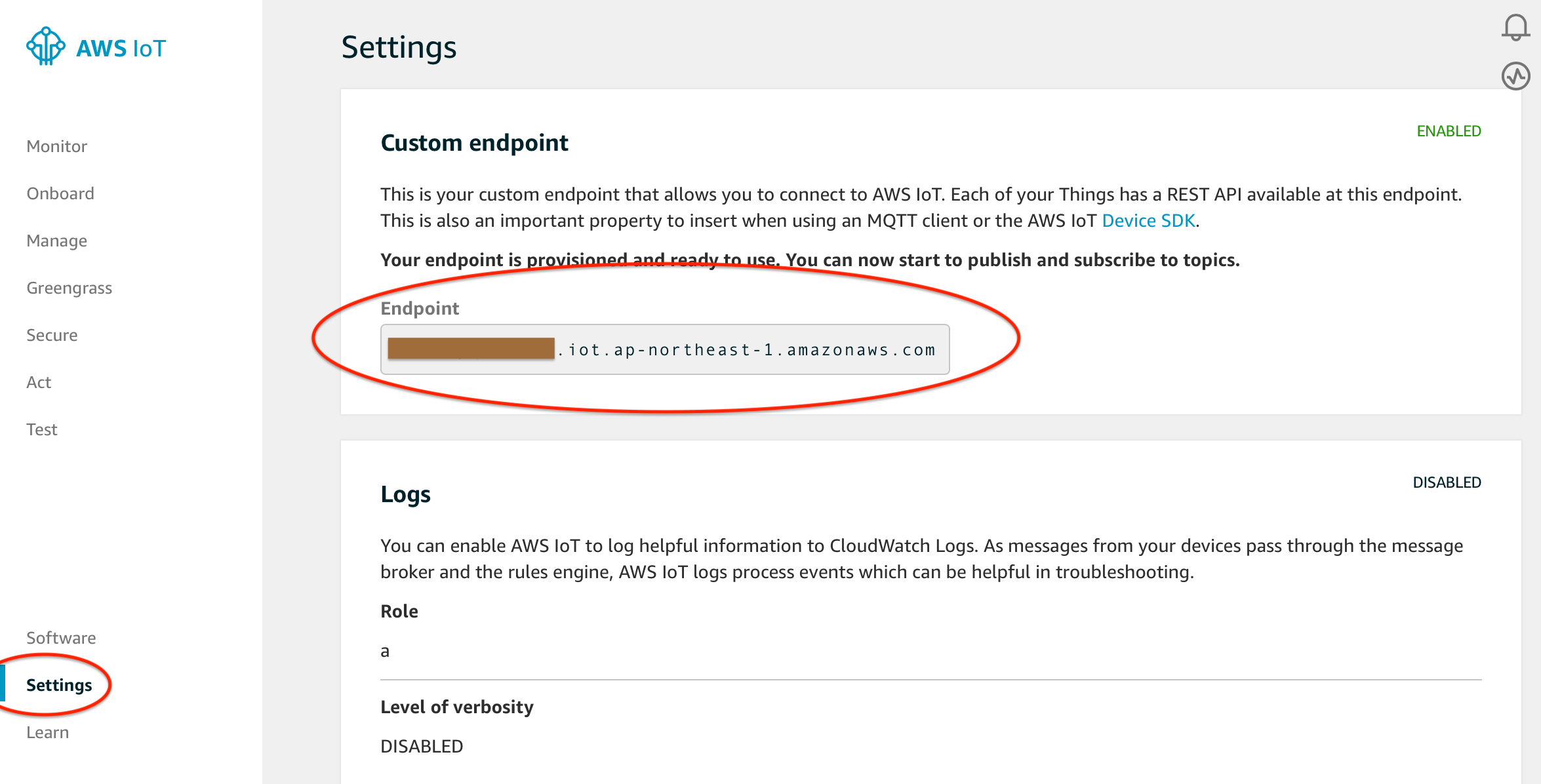
Endpoint
Replace the content of MQTT_SERVER_HOST_NAME with the Endpoint taken from AWS IoT. You can find your endpoint from Settings in the left menu.
Root CA
Replace the content of SSL_CA_PEM with the content in rootCA.pem downloaded above. You need to add " at the head of each line and \n" at the end of each line. Your SSL_CA_PEM become look like this:
const char SSL_CA_PEM[] = "-----BEGIN CERTIFICATE-----\n" "MIIE0zCCA7ugAwIBAgIQGNrRniZ96LtKIVjNzGs7SjANBgkqhkiG9w0BAQUFADCB\n" "yjELMAkGA1UEBhMCVVMxFzAVBgNVBAoTDlZlcmlTaWduLCBJbmMuMR8wHQYDVQQL\n" "ExZWZXJpU2lnbiBUcnVzdCBOZXR3b3JrMTowOAYDVQQLEzEoYykgMjAwNiBWZXJp\n" "U2lnbiwgSW5jLiAtIEZvciBhdXRob3JpemVkIHVzZSBvbmx5MUUwQwYDVQQDEzxW\n" "ZXJpU2lnbiBDbGFzcyAzIFB1YmxpYyBQcmltYXJ5IENlcnRpZmljYXRpb24gQXV0\n" "aG9yaXR5IC0gRzUwHhcNMDYxMTA4MDAwMDAwWhcNMzYwNzE2MjM1OTU5WjCByjEL\n" "MAkGA1UEBhMCVVMxFzAVBgNVBAoTDlZlcmlTaWduLCBJbmMuMR8wHQYDVQQLExZW\n" "ZXJpU2lnbiBUcnVzdCBOZXR3b3JrMTowOAYDVQQLEzEoYykgMjAwNiBWZXJpU2ln\n" "biwgSW5jLiAtIEZvciBhdXRob3JpemVkIHVzZSBvbmx5MUUwQwYDVQQDEzxWZXJp\n" "U2lnbiBDbGFzcyAzIFB1YmxpYyBQcmltYXJ5IENlcnRpZmljYXRpb24gQXV0aG9y\n" "aXR5IC0gRzUwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCvJAgIKXo1\n" "nmAMqudLO07cfLw8RRy7K+D+KQL5VwijZIUVJ/XxrcgxiV0i6CqqpkKzj/i5Vbex\n" "t0uz/o9+B1fs70PbZmIVYc9gDaTY3vjgw2IIPVQT60nKWVSFJuUrjxuf6/WhkcIz\n" "SdhDY2pSS9KP6HBRTdGJaXvHcPaz3BJ023tdS1bTlr8Vd6Gw9KIl8q8ckmcY5fQG\n" "BO+QueQA5N06tRn/Arr0PO7gi+s3i+z016zy9vA9r911kTMZHRxAy3QkGSGT2RT+\n" "rCpSx4/VBEnkjWNHiDxpg8v+R70rfk/Fla4OndTRQ8Bnc+MUCH7lP59zuDMKz10/\n" "NIeWiu5T6CUVAgMBAAGjgbIwga8wDwYDVR0TAQH/BAUwAwEB/zAOBgNVHQ8BAf8E\n" "BAMCAQYwbQYIKwYBBQUHAQwEYTBfoV2gWzBZMFcwVRYJaW1hZ2UvZ2lmMCEwHzAH\n" "BgUrDgMCGgQUj+XTGoasjY5rw8+AatRIGCx7GS4wJRYjaHR0cDovL2xvZ28udmVy\n" "aXNpZ24uY29tL3ZzbG9nby5naWYwHQYDVR0OBBYEFH/TZafC3ey78DAJ80M5+gKv\n" "MzEzMA0GCSqGSIb3DQEBBQUAA4IBAQCTJEowX2LP2BqYLz3q3JktvXf2pXkiOOzE\n" "p6B4Eq1iDkVwZMXnl2YtmAl+X6/WzChl8gGqCBpH3vn5fJJaCGkgDdk+bW48DW7Y\n" "5gaRQBi5+MHt39tBquCWIMnNZBU4gcmU7qKEKQsTb47bDN0lAtukixlE0kF6BWlK\n" "WE9gyn6CagsCqiUXObXbf+eEZSqVir2G3l6BFoMtEMze/aiCKm0oHw0LxOXnGiYZ\n" "4fQRbxC1lfznQgUy286dUV4otp6F01vvpX1FQHKOtw5rDgb7MzVIcbidJ4vEZV8N\n" "hnacRHr2lVz2XTIIM6RUthg/aFzyQkqFOFSDX9HoLPKsEdao7WNq\n" "-----END CERTIFICATE-----\n";
Client Certificate
Replace the content of SSL_CLIENT_CERT_PEM with the content in *.cert.pem download above. You need to add " at the head of each line and \n" at the end of each line. The content in the file should start with -----BEGIN CERTIFICATE----- and end with -----END CERTIFICATE-----.
Client Private Key
Replace the content of SSL_CLIENT_PRIVATE_KEY_PEM with the content in *.private.pem download above. You need to add " at the head of each line and \n" at the end of each line. The content in the file should start with -----BEGIN RSA PRIVATE KEY----- and end with -----END RSA PRIVATE KEY-----.
Do not share the private key information with anyone.
Client ID, Username, and Password
AWS IoT Core doesn't care about the contents of MQTT_CLIENT_ID, MQTT_USERNAME, and MQTT_PASSWORD. You can set any string follows MQTT naming convention.
Topic Name
You can set a topic name for publish and subscribe. MQTT_TOPIC_PUB is for publishing and MQTT_TOPIC_SUB is for subscribing. You can set any name follows MQTT naming convention.
Wi-Fi setting (for Wi-Fi boards)
If you use a Wi-Fi, set the security mode and SSID and Passoword in mbed_app.json.
"nsapi.default-wifi-security": "WPA_WPA2",
"nsapi.default-wifi-ssid": "\"SSID\"",
"nsapi.default-wifi-password": "\"PASSWORD\""
Build .bin
After settings are finished, click Compile button. You'll get Mbed-to-AWS-IoT_K64F.bin (If you changed project name or target board, the file name may be different.)
Launch Application
Copy the .bin file to your target board. To launch the application, push the reset button on your board.
16 comments on AWS IoT from Mbed OS device:
Please log in to post comments.

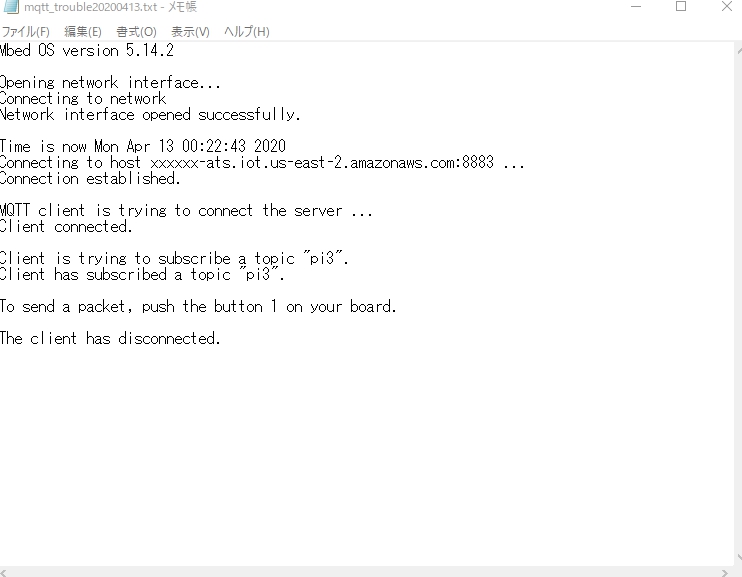

Hi Can I use the same to DISCO_L475VG_IOT01A IoT NODE board which is having a • Wi-Fi ® module Inventek ISM43362-M3G-L44.
I am asking because i am getting a compilation ERROR for the , please help if you know the alternative. I have posted a question https://os.mbed.com/questions/81674/MQTT-STM32L475-IoT-Node-Compilation-ERRO/