SX1276 Shield based Applications
Dependencies: X_NUCLEO_IKS01A1 LoRaWAN-lib SX1276Lib mbed
LoRaWAN-SX1276-Application Demo uses SX1276MB1LAS mbed component shield on a nucleo board platform to demonstrate a Class-A LoRaWAN device in the 915MHz ISM band for North American region. It uses the LoRaWAN-lib and SX1276Lib libraries.
Comissioning.h (LoRaWAN Network Configuration)
The end-device can be activated in one of the two ways:
Over the Air (OTA) activation can be enabled as shown in the figure below.
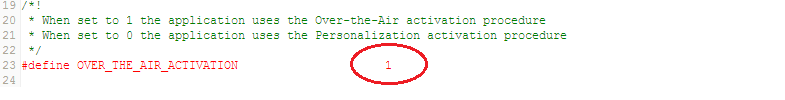
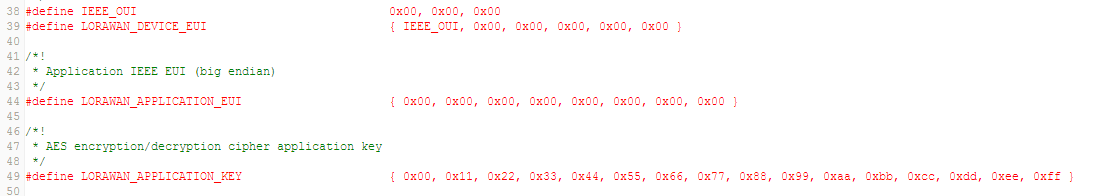
The end-device must be configured with the following parameters:
LORAWAN_DEVICE_EUI(8 Bytes) : Fist 3 Bytes is the Organizationally Unique Identifier (OUI) followed by 5 bytes of unique ID. If not defined by user, then the firmware automatically assigns one to the end-deviceLORAWAN_APPLICATION_EUI(8 Bytes)LORAWAN_APPLICATION_KEY(or DEVKEY) (16 Bytes)
Activation by Personalization (ABP) can be enabled as shown in the figure below.
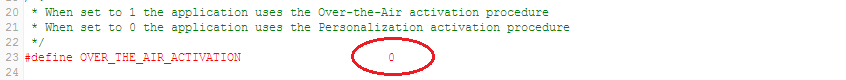
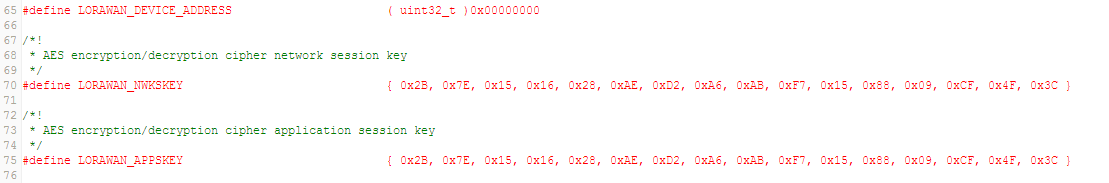
The end-device must be configured with the following parameters:
LORAWAN_DEVICE_ADDRESS(4 Bytes) : If not defined by user, then the firmware automatically assigns one to the end-deviceLORAWAN_NWKSKEY(16 Bytes)LORAWAN_APPSKEY(16 Bytes)
Config.h (LoRaWAN Communication Parameters)
- Mode of Operation : Hybrid
If the end-device needs to be configured to operate over 8-channels, then
Hybrid Modeneeds to be enabled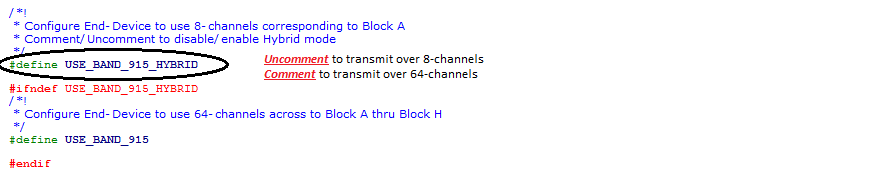
- Mode of Operation : Frequency Hop
If the end-device needs to be configured to operate over 64-channels, then
Hybrid Modeneeds to be disabled
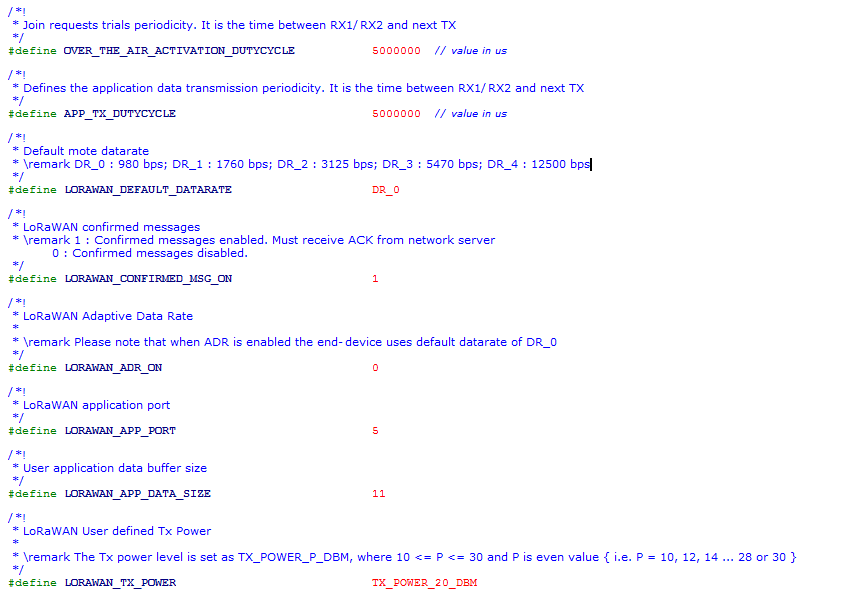
- Delay between successive JOIN REQUESTs :
The delay between successive Join Requests (until the end-device joins the network) can be configured using the parameter
OVER_THE_AIR_ACTIVATION_DUTYCYCLE
- Inter-Frame Delay :
One can change the delay between each frame transmission using
APP_TX_DUTYCYCLEIt is advisable thatAPP_TX_DUTYCYCLEis greater than or equal to 3sec.
- Data Rate :
The data rate can be configured as per LoRaWAN specification using the paramter
LORAWAN_DEFAULT_DATARATE. The range of values are DR_0, DR_1, DR_2, DR_3 and DR_4
- Confirmed/Unconfirmed Messages :
The uplink message or payload can be chosen to be confirmed or unconfirmed using the parameter
LORAWAN_CONFIRMED_MSG_ON. When set to 1, the transmitted messages need to be confirmed with anACKby the network server in the subsequent RX window. When set to 0, noACKis requested.
- ADR ON/OFF :
The ADR can be enabled or disabled using the parameter
LORAWAN_ADR_ON. When set to 1, ADR is enabled and disabled when set to 0.
- Application Port :
The application port can be set using parameter
LORAWAN_APP_PORT. A few examples are associated to specific Application Port, and are defined in Config.h
- Payload Length :
The lenght of the payload (in bytes) to be transmitted can be configured using
LORAWAN_APP_DATA_SIZE
- Transmit Power :
The transmit power can be configured using
LORAWAN_TX_POWER(LoRaMAC verifies if the set power is compliant with the LoRaWAN spec and FCC guidelines)
The baud-rate for serial terminal display is 115200
system/crypto/aes.cpp@6:c5f2da0de0b0, 2018-07-18 (annotated)
- Committer:
- ubhat
- Date:
- Wed Jul 18 22:26:26 2018 +0000
- Revision:
- 6:c5f2da0de0b0
- Parent:
- 0:42863a11464a
Add Channel Block option in Config.h; Fix board specific DevEUI allocation
Who changed what in which revision?
| User | Revision | Line number | New contents of line |
|---|---|---|---|
| ubhat | 0:42863a11464a | 1 | /* |
| ubhat | 0:42863a11464a | 2 | --------------------------------------------------------------------------- |
| ubhat | 0:42863a11464a | 3 | Copyright (c) 1998-2008, Brian Gladman, Worcester, UK. All rights reserved. |
| ubhat | 0:42863a11464a | 4 | |
| ubhat | 0:42863a11464a | 5 | LICENSE TERMS |
| ubhat | 0:42863a11464a | 6 | |
| ubhat | 0:42863a11464a | 7 | The redistribution and use of this software (with or without changes) |
| ubhat | 0:42863a11464a | 8 | is allowed without the payment of fees or royalties provided that: |
| ubhat | 0:42863a11464a | 9 | |
| ubhat | 0:42863a11464a | 10 | 1. source code distributions include the above copyright notice, this |
| ubhat | 0:42863a11464a | 11 | list of conditions and the following disclaimer; |
| ubhat | 0:42863a11464a | 12 | |
| ubhat | 0:42863a11464a | 13 | 2. binary distributions include the above copyright notice, this list |
| ubhat | 0:42863a11464a | 14 | of conditions and the following disclaimer in their documentation; |
| ubhat | 0:42863a11464a | 15 | |
| ubhat | 0:42863a11464a | 16 | 3. the name of the copyright holder is not used to endorse products |
| ubhat | 0:42863a11464a | 17 | built using this software without specific written permission. |
| ubhat | 0:42863a11464a | 18 | |
| ubhat | 0:42863a11464a | 19 | DISCLAIMER |
| ubhat | 0:42863a11464a | 20 | |
| ubhat | 0:42863a11464a | 21 | This software is provided 'as is' with no explicit or implied warranties |
| ubhat | 0:42863a11464a | 22 | in respect of its properties, including, but not limited to, correctness |
| ubhat | 0:42863a11464a | 23 | and/or fitness for purpose. |
| ubhat | 0:42863a11464a | 24 | --------------------------------------------------------------------------- |
| ubhat | 0:42863a11464a | 25 | Issue 09/09/2006 |
| ubhat | 0:42863a11464a | 26 | |
| ubhat | 0:42863a11464a | 27 | This is an AES implementation that uses only 8-bit byte operations on the |
| ubhat | 0:42863a11464a | 28 | cipher state (there are options to use 32-bit types if available). |
| ubhat | 0:42863a11464a | 29 | |
| ubhat | 0:42863a11464a | 30 | The combination of mix columns and byte substitution used here is based on |
| ubhat | 0:42863a11464a | 31 | that developed by Karl Malbrain. His contribution is acknowledged. |
| ubhat | 0:42863a11464a | 32 | */ |
| ubhat | 0:42863a11464a | 33 | |
| ubhat | 0:42863a11464a | 34 | /* define if you have a fast memcpy function on your system */ |
| ubhat | 0:42863a11464a | 35 | #if 0 |
| ubhat | 0:42863a11464a | 36 | # define HAVE_MEMCPY |
| ubhat | 0:42863a11464a | 37 | # include <string.h> |
| ubhat | 0:42863a11464a | 38 | # if defined( _MSC_VER ) |
| ubhat | 0:42863a11464a | 39 | # include <intrin.h> |
| ubhat | 0:42863a11464a | 40 | # pragma intrinsic( memcpy ) |
| ubhat | 0:42863a11464a | 41 | # endif |
| ubhat | 0:42863a11464a | 42 | #endif |
| ubhat | 0:42863a11464a | 43 | |
| ubhat | 0:42863a11464a | 44 | |
| ubhat | 0:42863a11464a | 45 | #include <stdlib.h> |
| ubhat | 0:42863a11464a | 46 | #include <stdint.h> |
| ubhat | 0:42863a11464a | 47 | |
| ubhat | 0:42863a11464a | 48 | /* define if you have fast 32-bit types on your system */ |
| ubhat | 0:42863a11464a | 49 | #if ( __CORTEX_M != 0 ) // if Cortex is different from M0/M0+ |
| ubhat | 0:42863a11464a | 50 | # define HAVE_UINT_32T |
| ubhat | 0:42863a11464a | 51 | #endif |
| ubhat | 0:42863a11464a | 52 | |
| ubhat | 0:42863a11464a | 53 | /* define if you don't want any tables */ |
| ubhat | 0:42863a11464a | 54 | #if 1 |
| ubhat | 0:42863a11464a | 55 | # define USE_TABLES |
| ubhat | 0:42863a11464a | 56 | #endif |
| ubhat | 0:42863a11464a | 57 | |
| ubhat | 0:42863a11464a | 58 | /* On Intel Core 2 duo VERSION_1 is faster */ |
| ubhat | 0:42863a11464a | 59 | |
| ubhat | 0:42863a11464a | 60 | /* alternative versions (test for performance on your system) */ |
| ubhat | 0:42863a11464a | 61 | #if 1 |
| ubhat | 0:42863a11464a | 62 | # define VERSION_1 |
| ubhat | 0:42863a11464a | 63 | #endif |
| ubhat | 0:42863a11464a | 64 | |
| ubhat | 0:42863a11464a | 65 | #include "aes.h" |
| ubhat | 0:42863a11464a | 66 | |
| ubhat | 0:42863a11464a | 67 | //#if defined( HAVE_UINT_32T ) |
| ubhat | 0:42863a11464a | 68 | // typedef unsigned long uint32_t; |
| ubhat | 0:42863a11464a | 69 | //#endif |
| ubhat | 0:42863a11464a | 70 | |
| ubhat | 0:42863a11464a | 71 | /* functions for finite field multiplication in the AES Galois field */ |
| ubhat | 0:42863a11464a | 72 | |
| ubhat | 0:42863a11464a | 73 | #define WPOLY 0x011b |
| ubhat | 0:42863a11464a | 74 | #define BPOLY 0x1b |
| ubhat | 0:42863a11464a | 75 | #define DPOLY 0x008d |
| ubhat | 0:42863a11464a | 76 | |
| ubhat | 0:42863a11464a | 77 | #define f1(x) (x) |
| ubhat | 0:42863a11464a | 78 | #define f2(x) ((x << 1) ^ (((x >> 7) & 1) * WPOLY)) |
| ubhat | 0:42863a11464a | 79 | #define f4(x) ((x << 2) ^ (((x >> 6) & 1) * WPOLY) ^ (((x >> 6) & 2) * WPOLY)) |
| ubhat | 0:42863a11464a | 80 | #define f8(x) ((x << 3) ^ (((x >> 5) & 1) * WPOLY) ^ (((x >> 5) & 2) * WPOLY) \ |
| ubhat | 0:42863a11464a | 81 | ^ (((x >> 5) & 4) * WPOLY)) |
| ubhat | 0:42863a11464a | 82 | #define d2(x) (((x) >> 1) ^ ((x) & 1 ? DPOLY : 0)) |
| ubhat | 0:42863a11464a | 83 | |
| ubhat | 0:42863a11464a | 84 | #define f3(x) (f2(x) ^ x) |
| ubhat | 0:42863a11464a | 85 | #define f9(x) (f8(x) ^ x) |
| ubhat | 0:42863a11464a | 86 | #define fb(x) (f8(x) ^ f2(x) ^ x) |
| ubhat | 0:42863a11464a | 87 | #define fd(x) (f8(x) ^ f4(x) ^ x) |
| ubhat | 0:42863a11464a | 88 | #define fe(x) (f8(x) ^ f4(x) ^ f2(x)) |
| ubhat | 0:42863a11464a | 89 | |
| ubhat | 0:42863a11464a | 90 | #if defined( USE_TABLES ) |
| ubhat | 0:42863a11464a | 91 | |
| ubhat | 0:42863a11464a | 92 | #define sb_data(w) { /* S Box data values */ \ |
| ubhat | 0:42863a11464a | 93 | w(0x63), w(0x7c), w(0x77), w(0x7b), w(0xf2), w(0x6b), w(0x6f), w(0xc5),\ |
| ubhat | 0:42863a11464a | 94 | w(0x30), w(0x01), w(0x67), w(0x2b), w(0xfe), w(0xd7), w(0xab), w(0x76),\ |
| ubhat | 0:42863a11464a | 95 | w(0xca), w(0x82), w(0xc9), w(0x7d), w(0xfa), w(0x59), w(0x47), w(0xf0),\ |
| ubhat | 0:42863a11464a | 96 | w(0xad), w(0xd4), w(0xa2), w(0xaf), w(0x9c), w(0xa4), w(0x72), w(0xc0),\ |
| ubhat | 0:42863a11464a | 97 | w(0xb7), w(0xfd), w(0x93), w(0x26), w(0x36), w(0x3f), w(0xf7), w(0xcc),\ |
| ubhat | 0:42863a11464a | 98 | w(0x34), w(0xa5), w(0xe5), w(0xf1), w(0x71), w(0xd8), w(0x31), w(0x15),\ |
| ubhat | 0:42863a11464a | 99 | w(0x04), w(0xc7), w(0x23), w(0xc3), w(0x18), w(0x96), w(0x05), w(0x9a),\ |
| ubhat | 0:42863a11464a | 100 | w(0x07), w(0x12), w(0x80), w(0xe2), w(0xeb), w(0x27), w(0xb2), w(0x75),\ |
| ubhat | 0:42863a11464a | 101 | w(0x09), w(0x83), w(0x2c), w(0x1a), w(0x1b), w(0x6e), w(0x5a), w(0xa0),\ |
| ubhat | 0:42863a11464a | 102 | w(0x52), w(0x3b), w(0xd6), w(0xb3), w(0x29), w(0xe3), w(0x2f), w(0x84),\ |
| ubhat | 0:42863a11464a | 103 | w(0x53), w(0xd1), w(0x00), w(0xed), w(0x20), w(0xfc), w(0xb1), w(0x5b),\ |
| ubhat | 0:42863a11464a | 104 | w(0x6a), w(0xcb), w(0xbe), w(0x39), w(0x4a), w(0x4c), w(0x58), w(0xcf),\ |
| ubhat | 0:42863a11464a | 105 | w(0xd0), w(0xef), w(0xaa), w(0xfb), w(0x43), w(0x4d), w(0x33), w(0x85),\ |
| ubhat | 0:42863a11464a | 106 | w(0x45), w(0xf9), w(0x02), w(0x7f), w(0x50), w(0x3c), w(0x9f), w(0xa8),\ |
| ubhat | 0:42863a11464a | 107 | w(0x51), w(0xa3), w(0x40), w(0x8f), w(0x92), w(0x9d), w(0x38), w(0xf5),\ |
| ubhat | 0:42863a11464a | 108 | w(0xbc), w(0xb6), w(0xda), w(0x21), w(0x10), w(0xff), w(0xf3), w(0xd2),\ |
| ubhat | 0:42863a11464a | 109 | w(0xcd), w(0x0c), w(0x13), w(0xec), w(0x5f), w(0x97), w(0x44), w(0x17),\ |
| ubhat | 0:42863a11464a | 110 | w(0xc4), w(0xa7), w(0x7e), w(0x3d), w(0x64), w(0x5d), w(0x19), w(0x73),\ |
| ubhat | 0:42863a11464a | 111 | w(0x60), w(0x81), w(0x4f), w(0xdc), w(0x22), w(0x2a), w(0x90), w(0x88),\ |
| ubhat | 0:42863a11464a | 112 | w(0x46), w(0xee), w(0xb8), w(0x14), w(0xde), w(0x5e), w(0x0b), w(0xdb),\ |
| ubhat | 0:42863a11464a | 113 | w(0xe0), w(0x32), w(0x3a), w(0x0a), w(0x49), w(0x06), w(0x24), w(0x5c),\ |
| ubhat | 0:42863a11464a | 114 | w(0xc2), w(0xd3), w(0xac), w(0x62), w(0x91), w(0x95), w(0xe4), w(0x79),\ |
| ubhat | 0:42863a11464a | 115 | w(0xe7), w(0xc8), w(0x37), w(0x6d), w(0x8d), w(0xd5), w(0x4e), w(0xa9),\ |
| ubhat | 0:42863a11464a | 116 | w(0x6c), w(0x56), w(0xf4), w(0xea), w(0x65), w(0x7a), w(0xae), w(0x08),\ |
| ubhat | 0:42863a11464a | 117 | w(0xba), w(0x78), w(0x25), w(0x2e), w(0x1c), w(0xa6), w(0xb4), w(0xc6),\ |
| ubhat | 0:42863a11464a | 118 | w(0xe8), w(0xdd), w(0x74), w(0x1f), w(0x4b), w(0xbd), w(0x8b), w(0x8a),\ |
| ubhat | 0:42863a11464a | 119 | w(0x70), w(0x3e), w(0xb5), w(0x66), w(0x48), w(0x03), w(0xf6), w(0x0e),\ |
| ubhat | 0:42863a11464a | 120 | w(0x61), w(0x35), w(0x57), w(0xb9), w(0x86), w(0xc1), w(0x1d), w(0x9e),\ |
| ubhat | 0:42863a11464a | 121 | w(0xe1), w(0xf8), w(0x98), w(0x11), w(0x69), w(0xd9), w(0x8e), w(0x94),\ |
| ubhat | 0:42863a11464a | 122 | w(0x9b), w(0x1e), w(0x87), w(0xe9), w(0xce), w(0x55), w(0x28), w(0xdf),\ |
| ubhat | 0:42863a11464a | 123 | w(0x8c), w(0xa1), w(0x89), w(0x0d), w(0xbf), w(0xe6), w(0x42), w(0x68),\ |
| ubhat | 0:42863a11464a | 124 | w(0x41), w(0x99), w(0x2d), w(0x0f), w(0xb0), w(0x54), w(0xbb), w(0x16) } |
| ubhat | 0:42863a11464a | 125 | |
| ubhat | 0:42863a11464a | 126 | #define isb_data(w) { /* inverse S Box data values */ \ |
| ubhat | 0:42863a11464a | 127 | w(0x52), w(0x09), w(0x6a), w(0xd5), w(0x30), w(0x36), w(0xa5), w(0x38),\ |
| ubhat | 0:42863a11464a | 128 | w(0xbf), w(0x40), w(0xa3), w(0x9e), w(0x81), w(0xf3), w(0xd7), w(0xfb),\ |
| ubhat | 0:42863a11464a | 129 | w(0x7c), w(0xe3), w(0x39), w(0x82), w(0x9b), w(0x2f), w(0xff), w(0x87),\ |
| ubhat | 0:42863a11464a | 130 | w(0x34), w(0x8e), w(0x43), w(0x44), w(0xc4), w(0xde), w(0xe9), w(0xcb),\ |
| ubhat | 0:42863a11464a | 131 | w(0x54), w(0x7b), w(0x94), w(0x32), w(0xa6), w(0xc2), w(0x23), w(0x3d),\ |
| ubhat | 0:42863a11464a | 132 | w(0xee), w(0x4c), w(0x95), w(0x0b), w(0x42), w(0xfa), w(0xc3), w(0x4e),\ |
| ubhat | 0:42863a11464a | 133 | w(0x08), w(0x2e), w(0xa1), w(0x66), w(0x28), w(0xd9), w(0x24), w(0xb2),\ |
| ubhat | 0:42863a11464a | 134 | w(0x76), w(0x5b), w(0xa2), w(0x49), w(0x6d), w(0x8b), w(0xd1), w(0x25),\ |
| ubhat | 0:42863a11464a | 135 | w(0x72), w(0xf8), w(0xf6), w(0x64), w(0x86), w(0x68), w(0x98), w(0x16),\ |
| ubhat | 0:42863a11464a | 136 | w(0xd4), w(0xa4), w(0x5c), w(0xcc), w(0x5d), w(0x65), w(0xb6), w(0x92),\ |
| ubhat | 0:42863a11464a | 137 | w(0x6c), w(0x70), w(0x48), w(0x50), w(0xfd), w(0xed), w(0xb9), w(0xda),\ |
| ubhat | 0:42863a11464a | 138 | w(0x5e), w(0x15), w(0x46), w(0x57), w(0xa7), w(0x8d), w(0x9d), w(0x84),\ |
| ubhat | 0:42863a11464a | 139 | w(0x90), w(0xd8), w(0xab), w(0x00), w(0x8c), w(0xbc), w(0xd3), w(0x0a),\ |
| ubhat | 0:42863a11464a | 140 | w(0xf7), w(0xe4), w(0x58), w(0x05), w(0xb8), w(0xb3), w(0x45), w(0x06),\ |
| ubhat | 0:42863a11464a | 141 | w(0xd0), w(0x2c), w(0x1e), w(0x8f), w(0xca), w(0x3f), w(0x0f), w(0x02),\ |
| ubhat | 0:42863a11464a | 142 | w(0xc1), w(0xaf), w(0xbd), w(0x03), w(0x01), w(0x13), w(0x8a), w(0x6b),\ |
| ubhat | 0:42863a11464a | 143 | w(0x3a), w(0x91), w(0x11), w(0x41), w(0x4f), w(0x67), w(0xdc), w(0xea),\ |
| ubhat | 0:42863a11464a | 144 | w(0x97), w(0xf2), w(0xcf), w(0xce), w(0xf0), w(0xb4), w(0xe6), w(0x73),\ |
| ubhat | 0:42863a11464a | 145 | w(0x96), w(0xac), w(0x74), w(0x22), w(0xe7), w(0xad), w(0x35), w(0x85),\ |
| ubhat | 0:42863a11464a | 146 | w(0xe2), w(0xf9), w(0x37), w(0xe8), w(0x1c), w(0x75), w(0xdf), w(0x6e),\ |
| ubhat | 0:42863a11464a | 147 | w(0x47), w(0xf1), w(0x1a), w(0x71), w(0x1d), w(0x29), w(0xc5), w(0x89),\ |
| ubhat | 0:42863a11464a | 148 | w(0x6f), w(0xb7), w(0x62), w(0x0e), w(0xaa), w(0x18), w(0xbe), w(0x1b),\ |
| ubhat | 0:42863a11464a | 149 | w(0xfc), w(0x56), w(0x3e), w(0x4b), w(0xc6), w(0xd2), w(0x79), w(0x20),\ |
| ubhat | 0:42863a11464a | 150 | w(0x9a), w(0xdb), w(0xc0), w(0xfe), w(0x78), w(0xcd), w(0x5a), w(0xf4),\ |
| ubhat | 0:42863a11464a | 151 | w(0x1f), w(0xdd), w(0xa8), w(0x33), w(0x88), w(0x07), w(0xc7), w(0x31),\ |
| ubhat | 0:42863a11464a | 152 | w(0xb1), w(0x12), w(0x10), w(0x59), w(0x27), w(0x80), w(0xec), w(0x5f),\ |
| ubhat | 0:42863a11464a | 153 | w(0x60), w(0x51), w(0x7f), w(0xa9), w(0x19), w(0xb5), w(0x4a), w(0x0d),\ |
| ubhat | 0:42863a11464a | 154 | w(0x2d), w(0xe5), w(0x7a), w(0x9f), w(0x93), w(0xc9), w(0x9c), w(0xef),\ |
| ubhat | 0:42863a11464a | 155 | w(0xa0), w(0xe0), w(0x3b), w(0x4d), w(0xae), w(0x2a), w(0xf5), w(0xb0),\ |
| ubhat | 0:42863a11464a | 156 | w(0xc8), w(0xeb), w(0xbb), w(0x3c), w(0x83), w(0x53), w(0x99), w(0x61),\ |
| ubhat | 0:42863a11464a | 157 | w(0x17), w(0x2b), w(0x04), w(0x7e), w(0xba), w(0x77), w(0xd6), w(0x26),\ |
| ubhat | 0:42863a11464a | 158 | w(0xe1), w(0x69), w(0x14), w(0x63), w(0x55), w(0x21), w(0x0c), w(0x7d) } |
| ubhat | 0:42863a11464a | 159 | |
| ubhat | 0:42863a11464a | 160 | #define mm_data(w) { /* basic data for forming finite field tables */ \ |
| ubhat | 0:42863a11464a | 161 | w(0x00), w(0x01), w(0x02), w(0x03), w(0x04), w(0x05), w(0x06), w(0x07),\ |
| ubhat | 0:42863a11464a | 162 | w(0x08), w(0x09), w(0x0a), w(0x0b), w(0x0c), w(0x0d), w(0x0e), w(0x0f),\ |
| ubhat | 0:42863a11464a | 163 | w(0x10), w(0x11), w(0x12), w(0x13), w(0x14), w(0x15), w(0x16), w(0x17),\ |
| ubhat | 0:42863a11464a | 164 | w(0x18), w(0x19), w(0x1a), w(0x1b), w(0x1c), w(0x1d), w(0x1e), w(0x1f),\ |
| ubhat | 0:42863a11464a | 165 | w(0x20), w(0x21), w(0x22), w(0x23), w(0x24), w(0x25), w(0x26), w(0x27),\ |
| ubhat | 0:42863a11464a | 166 | w(0x28), w(0x29), w(0x2a), w(0x2b), w(0x2c), w(0x2d), w(0x2e), w(0x2f),\ |
| ubhat | 0:42863a11464a | 167 | w(0x30), w(0x31), w(0x32), w(0x33), w(0x34), w(0x35), w(0x36), w(0x37),\ |
| ubhat | 0:42863a11464a | 168 | w(0x38), w(0x39), w(0x3a), w(0x3b), w(0x3c), w(0x3d), w(0x3e), w(0x3f),\ |
| ubhat | 0:42863a11464a | 169 | w(0x40), w(0x41), w(0x42), w(0x43), w(0x44), w(0x45), w(0x46), w(0x47),\ |
| ubhat | 0:42863a11464a | 170 | w(0x48), w(0x49), w(0x4a), w(0x4b), w(0x4c), w(0x4d), w(0x4e), w(0x4f),\ |
| ubhat | 0:42863a11464a | 171 | w(0x50), w(0x51), w(0x52), w(0x53), w(0x54), w(0x55), w(0x56), w(0x57),\ |
| ubhat | 0:42863a11464a | 172 | w(0x58), w(0x59), w(0x5a), w(0x5b), w(0x5c), w(0x5d), w(0x5e), w(0x5f),\ |
| ubhat | 0:42863a11464a | 173 | w(0x60), w(0x61), w(0x62), w(0x63), w(0x64), w(0x65), w(0x66), w(0x67),\ |
| ubhat | 0:42863a11464a | 174 | w(0x68), w(0x69), w(0x6a), w(0x6b), w(0x6c), w(0x6d), w(0x6e), w(0x6f),\ |
| ubhat | 0:42863a11464a | 175 | w(0x70), w(0x71), w(0x72), w(0x73), w(0x74), w(0x75), w(0x76), w(0x77),\ |
| ubhat | 0:42863a11464a | 176 | w(0x78), w(0x79), w(0x7a), w(0x7b), w(0x7c), w(0x7d), w(0x7e), w(0x7f),\ |
| ubhat | 0:42863a11464a | 177 | w(0x80), w(0x81), w(0x82), w(0x83), w(0x84), w(0x85), w(0x86), w(0x87),\ |
| ubhat | 0:42863a11464a | 178 | w(0x88), w(0x89), w(0x8a), w(0x8b), w(0x8c), w(0x8d), w(0x8e), w(0x8f),\ |
| ubhat | 0:42863a11464a | 179 | w(0x90), w(0x91), w(0x92), w(0x93), w(0x94), w(0x95), w(0x96), w(0x97),\ |
| ubhat | 0:42863a11464a | 180 | w(0x98), w(0x99), w(0x9a), w(0x9b), w(0x9c), w(0x9d), w(0x9e), w(0x9f),\ |
| ubhat | 0:42863a11464a | 181 | w(0xa0), w(0xa1), w(0xa2), w(0xa3), w(0xa4), w(0xa5), w(0xa6), w(0xa7),\ |
| ubhat | 0:42863a11464a | 182 | w(0xa8), w(0xa9), w(0xaa), w(0xab), w(0xac), w(0xad), w(0xae), w(0xaf),\ |
| ubhat | 0:42863a11464a | 183 | w(0xb0), w(0xb1), w(0xb2), w(0xb3), w(0xb4), w(0xb5), w(0xb6), w(0xb7),\ |
| ubhat | 0:42863a11464a | 184 | w(0xb8), w(0xb9), w(0xba), w(0xbb), w(0xbc), w(0xbd), w(0xbe), w(0xbf),\ |
| ubhat | 0:42863a11464a | 185 | w(0xc0), w(0xc1), w(0xc2), w(0xc3), w(0xc4), w(0xc5), w(0xc6), w(0xc7),\ |
| ubhat | 0:42863a11464a | 186 | w(0xc8), w(0xc9), w(0xca), w(0xcb), w(0xcc), w(0xcd), w(0xce), w(0xcf),\ |
| ubhat | 0:42863a11464a | 187 | w(0xd0), w(0xd1), w(0xd2), w(0xd3), w(0xd4), w(0xd5), w(0xd6), w(0xd7),\ |
| ubhat | 0:42863a11464a | 188 | w(0xd8), w(0xd9), w(0xda), w(0xdb), w(0xdc), w(0xdd), w(0xde), w(0xdf),\ |
| ubhat | 0:42863a11464a | 189 | w(0xe0), w(0xe1), w(0xe2), w(0xe3), w(0xe4), w(0xe5), w(0xe6), w(0xe7),\ |
| ubhat | 0:42863a11464a | 190 | w(0xe8), w(0xe9), w(0xea), w(0xeb), w(0xec), w(0xed), w(0xee), w(0xef),\ |
| ubhat | 0:42863a11464a | 191 | w(0xf0), w(0xf1), w(0xf2), w(0xf3), w(0xf4), w(0xf5), w(0xf6), w(0xf7),\ |
| ubhat | 0:42863a11464a | 192 | w(0xf8), w(0xf9), w(0xfa), w(0xfb), w(0xfc), w(0xfd), w(0xfe), w(0xff) } |
| ubhat | 0:42863a11464a | 193 | |
| ubhat | 0:42863a11464a | 194 | static const uint8_t sbox[256] = sb_data(f1); |
| ubhat | 0:42863a11464a | 195 | |
| ubhat | 0:42863a11464a | 196 | #if defined( AES_DEC_PREKEYED ) |
| ubhat | 0:42863a11464a | 197 | static const uint8_t isbox[256] = isb_data(f1); |
| ubhat | 0:42863a11464a | 198 | #endif |
| ubhat | 0:42863a11464a | 199 | |
| ubhat | 0:42863a11464a | 200 | static const uint8_t gfm2_sbox[256] = sb_data(f2); |
| ubhat | 0:42863a11464a | 201 | static const uint8_t gfm3_sbox[256] = sb_data(f3); |
| ubhat | 0:42863a11464a | 202 | |
| ubhat | 0:42863a11464a | 203 | #if defined( AES_DEC_PREKEYED ) |
| ubhat | 0:42863a11464a | 204 | static const uint8_t gfmul_9[256] = mm_data(f9); |
| ubhat | 0:42863a11464a | 205 | static const uint8_t gfmul_b[256] = mm_data(fb); |
| ubhat | 0:42863a11464a | 206 | static const uint8_t gfmul_d[256] = mm_data(fd); |
| ubhat | 0:42863a11464a | 207 | static const uint8_t gfmul_e[256] = mm_data(fe); |
| ubhat | 0:42863a11464a | 208 | #endif |
| ubhat | 0:42863a11464a | 209 | |
| ubhat | 0:42863a11464a | 210 | #define s_box(x) sbox[(x)] |
| ubhat | 0:42863a11464a | 211 | #if defined( AES_DEC_PREKEYED ) |
| ubhat | 0:42863a11464a | 212 | #define is_box(x) isbox[(x)] |
| ubhat | 0:42863a11464a | 213 | #endif |
| ubhat | 0:42863a11464a | 214 | #define gfm2_sb(x) gfm2_sbox[(x)] |
| ubhat | 0:42863a11464a | 215 | #define gfm3_sb(x) gfm3_sbox[(x)] |
| ubhat | 0:42863a11464a | 216 | #if defined( AES_DEC_PREKEYED ) |
| ubhat | 0:42863a11464a | 217 | #define gfm_9(x) gfmul_9[(x)] |
| ubhat | 0:42863a11464a | 218 | #define gfm_b(x) gfmul_b[(x)] |
| ubhat | 0:42863a11464a | 219 | #define gfm_d(x) gfmul_d[(x)] |
| ubhat | 0:42863a11464a | 220 | #define gfm_e(x) gfmul_e[(x)] |
| ubhat | 0:42863a11464a | 221 | #endif |
| ubhat | 0:42863a11464a | 222 | #else |
| ubhat | 0:42863a11464a | 223 | |
| ubhat | 0:42863a11464a | 224 | /* this is the high bit of x right shifted by 1 */ |
| ubhat | 0:42863a11464a | 225 | /* position. Since the starting polynomial has */ |
| ubhat | 0:42863a11464a | 226 | /* 9 bits (0x11b), this right shift keeps the */ |
| ubhat | 0:42863a11464a | 227 | /* values of all top bits within a byte */ |
| ubhat | 0:42863a11464a | 228 | |
| ubhat | 0:42863a11464a | 229 | static uint8_t hibit(const uint8_t x) |
| ubhat | 0:42863a11464a | 230 | { uint8_t r = (uint8_t)((x >> 1) | (x >> 2)); |
| ubhat | 0:42863a11464a | 231 | |
| ubhat | 0:42863a11464a | 232 | r |= (r >> 2); |
| ubhat | 0:42863a11464a | 233 | r |= (r >> 4); |
| ubhat | 0:42863a11464a | 234 | return (r + 1) >> 1; |
| ubhat | 0:42863a11464a | 235 | } |
| ubhat | 0:42863a11464a | 236 | |
| ubhat | 0:42863a11464a | 237 | /* return the inverse of the finite field element x */ |
| ubhat | 0:42863a11464a | 238 | |
| ubhat | 0:42863a11464a | 239 | static uint8_t gf_inv(const uint8_t x) |
| ubhat | 0:42863a11464a | 240 | { uint8_t p1 = x, p2 = BPOLY, n1 = hibit(x), n2 = 0x80, v1 = 1, v2 = 0; |
| ubhat | 0:42863a11464a | 241 | |
| ubhat | 0:42863a11464a | 242 | if(x < 2) |
| ubhat | 0:42863a11464a | 243 | return x; |
| ubhat | 0:42863a11464a | 244 | |
| ubhat | 0:42863a11464a | 245 | for( ; ; ) |
| ubhat | 0:42863a11464a | 246 | { |
| ubhat | 0:42863a11464a | 247 | if(n1) |
| ubhat | 0:42863a11464a | 248 | while(n2 >= n1) /* divide polynomial p2 by p1 */ |
| ubhat | 0:42863a11464a | 249 | { |
| ubhat | 0:42863a11464a | 250 | n2 /= n1; /* shift smaller polynomial left */ |
| ubhat | 0:42863a11464a | 251 | p2 ^= (p1 * n2) & 0xff; /* and remove from larger one */ |
| ubhat | 0:42863a11464a | 252 | v2 ^= (v1 * n2); /* shift accumulated value and */ |
| ubhat | 0:42863a11464a | 253 | n2 = hibit(p2); /* add into result */ |
| ubhat | 0:42863a11464a | 254 | } |
| ubhat | 0:42863a11464a | 255 | else |
| ubhat | 0:42863a11464a | 256 | return v1; |
| ubhat | 0:42863a11464a | 257 | |
| ubhat | 0:42863a11464a | 258 | if(n2) /* repeat with values swapped */ |
| ubhat | 0:42863a11464a | 259 | while(n1 >= n2) |
| ubhat | 0:42863a11464a | 260 | { |
| ubhat | 0:42863a11464a | 261 | n1 /= n2; |
| ubhat | 0:42863a11464a | 262 | p1 ^= p2 * n1; |
| ubhat | 0:42863a11464a | 263 | v1 ^= v2 * n1; |
| ubhat | 0:42863a11464a | 264 | n1 = hibit(p1); |
| ubhat | 0:42863a11464a | 265 | } |
| ubhat | 0:42863a11464a | 266 | else |
| ubhat | 0:42863a11464a | 267 | return v2; |
| ubhat | 0:42863a11464a | 268 | } |
| ubhat | 0:42863a11464a | 269 | } |
| ubhat | 0:42863a11464a | 270 | |
| ubhat | 0:42863a11464a | 271 | /* The forward and inverse affine transformations used in the S-box */ |
| ubhat | 0:42863a11464a | 272 | uint8_t fwd_affine(const uint8_t x) |
| ubhat | 0:42863a11464a | 273 | { |
| ubhat | 0:42863a11464a | 274 | #if defined( HAVE_UINT_32T ) |
| ubhat | 0:42863a11464a | 275 | uint32_t w = x; |
| ubhat | 0:42863a11464a | 276 | w ^= (w << 1) ^ (w << 2) ^ (w << 3) ^ (w << 4); |
| ubhat | 0:42863a11464a | 277 | return 0x63 ^ ((w ^ (w >> 8)) & 0xff); |
| ubhat | 0:42863a11464a | 278 | #else |
| ubhat | 0:42863a11464a | 279 | return 0x63 ^ x ^ (x << 1) ^ (x << 2) ^ (x << 3) ^ (x << 4) |
| ubhat | 0:42863a11464a | 280 | ^ (x >> 7) ^ (x >> 6) ^ (x >> 5) ^ (x >> 4); |
| ubhat | 0:42863a11464a | 281 | #endif |
| ubhat | 0:42863a11464a | 282 | } |
| ubhat | 0:42863a11464a | 283 | |
| ubhat | 0:42863a11464a | 284 | uint8_t inv_affine(const uint8_t x) |
| ubhat | 0:42863a11464a | 285 | { |
| ubhat | 0:42863a11464a | 286 | #if defined( HAVE_UINT_32T ) |
| ubhat | 0:42863a11464a | 287 | uint32_t w = x; |
| ubhat | 0:42863a11464a | 288 | w = (w << 1) ^ (w << 3) ^ (w << 6); |
| ubhat | 0:42863a11464a | 289 | return 0x05 ^ ((w ^ (w >> 8)) & 0xff); |
| ubhat | 0:42863a11464a | 290 | #else |
| ubhat | 0:42863a11464a | 291 | return 0x05 ^ (x << 1) ^ (x << 3) ^ (x << 6) |
| ubhat | 0:42863a11464a | 292 | ^ (x >> 7) ^ (x >> 5) ^ (x >> 2); |
| ubhat | 0:42863a11464a | 293 | #endif |
| ubhat | 0:42863a11464a | 294 | } |
| ubhat | 0:42863a11464a | 295 | |
| ubhat | 0:42863a11464a | 296 | #define s_box(x) fwd_affine(gf_inv(x)) |
| ubhat | 0:42863a11464a | 297 | #define is_box(x) gf_inv(inv_affine(x)) |
| ubhat | 0:42863a11464a | 298 | #define gfm2_sb(x) f2(s_box(x)) |
| ubhat | 0:42863a11464a | 299 | #define gfm3_sb(x) f3(s_box(x)) |
| ubhat | 0:42863a11464a | 300 | #define gfm_9(x) f9(x) |
| ubhat | 0:42863a11464a | 301 | #define gfm_b(x) fb(x) |
| ubhat | 0:42863a11464a | 302 | #define gfm_d(x) fd(x) |
| ubhat | 0:42863a11464a | 303 | #define gfm_e(x) fe(x) |
| ubhat | 0:42863a11464a | 304 | |
| ubhat | 0:42863a11464a | 305 | #endif |
| ubhat | 0:42863a11464a | 306 | |
| ubhat | 0:42863a11464a | 307 | #if defined( HAVE_MEMCPY ) |
| ubhat | 0:42863a11464a | 308 | # define block_copy_nn(d, s, l) memcpy(d, s, l) |
| ubhat | 0:42863a11464a | 309 | # define block_copy(d, s) memcpy(d, s, N_BLOCK) |
| ubhat | 0:42863a11464a | 310 | #else |
| ubhat | 0:42863a11464a | 311 | # define block_copy_nn(d, s, l) copy_block_nn(d, s, l) |
| ubhat | 0:42863a11464a | 312 | # define block_copy(d, s) copy_block(d, s) |
| ubhat | 0:42863a11464a | 313 | #endif |
| ubhat | 0:42863a11464a | 314 | |
| ubhat | 0:42863a11464a | 315 | static void copy_block( void *d, const void *s ) |
| ubhat | 0:42863a11464a | 316 | { |
| ubhat | 0:42863a11464a | 317 | #if defined( HAVE_UINT_32T ) |
| ubhat | 0:42863a11464a | 318 | ((uint32_t*)d)[ 0] = ((uint32_t*)s)[ 0]; |
| ubhat | 0:42863a11464a | 319 | ((uint32_t*)d)[ 1] = ((uint32_t*)s)[ 1]; |
| ubhat | 0:42863a11464a | 320 | ((uint32_t*)d)[ 2] = ((uint32_t*)s)[ 2]; |
| ubhat | 0:42863a11464a | 321 | ((uint32_t*)d)[ 3] = ((uint32_t*)s)[ 3]; |
| ubhat | 0:42863a11464a | 322 | #else |
| ubhat | 0:42863a11464a | 323 | ((uint8_t*)d)[ 0] = ((uint8_t*)s)[ 0]; |
| ubhat | 0:42863a11464a | 324 | ((uint8_t*)d)[ 1] = ((uint8_t*)s)[ 1]; |
| ubhat | 0:42863a11464a | 325 | ((uint8_t*)d)[ 2] = ((uint8_t*)s)[ 2]; |
| ubhat | 0:42863a11464a | 326 | ((uint8_t*)d)[ 3] = ((uint8_t*)s)[ 3]; |
| ubhat | 0:42863a11464a | 327 | ((uint8_t*)d)[ 4] = ((uint8_t*)s)[ 4]; |
| ubhat | 0:42863a11464a | 328 | ((uint8_t*)d)[ 5] = ((uint8_t*)s)[ 5]; |
| ubhat | 0:42863a11464a | 329 | ((uint8_t*)d)[ 6] = ((uint8_t*)s)[ 6]; |
| ubhat | 0:42863a11464a | 330 | ((uint8_t*)d)[ 7] = ((uint8_t*)s)[ 7]; |
| ubhat | 0:42863a11464a | 331 | ((uint8_t*)d)[ 8] = ((uint8_t*)s)[ 8]; |
| ubhat | 0:42863a11464a | 332 | ((uint8_t*)d)[ 9] = ((uint8_t*)s)[ 9]; |
| ubhat | 0:42863a11464a | 333 | ((uint8_t*)d)[10] = ((uint8_t*)s)[10]; |
| ubhat | 0:42863a11464a | 334 | ((uint8_t*)d)[11] = ((uint8_t*)s)[11]; |
| ubhat | 0:42863a11464a | 335 | ((uint8_t*)d)[12] = ((uint8_t*)s)[12]; |
| ubhat | 0:42863a11464a | 336 | ((uint8_t*)d)[13] = ((uint8_t*)s)[13]; |
| ubhat | 0:42863a11464a | 337 | ((uint8_t*)d)[14] = ((uint8_t*)s)[14]; |
| ubhat | 0:42863a11464a | 338 | ((uint8_t*)d)[15] = ((uint8_t*)s)[15]; |
| ubhat | 0:42863a11464a | 339 | #endif |
| ubhat | 0:42863a11464a | 340 | } |
| ubhat | 0:42863a11464a | 341 | |
| ubhat | 0:42863a11464a | 342 | static void copy_block_nn( uint8_t * d, const uint8_t *s, uint8_t nn ) |
| ubhat | 0:42863a11464a | 343 | { |
| ubhat | 0:42863a11464a | 344 | while( nn-- ) |
| ubhat | 0:42863a11464a | 345 | //*((uint8_t*)d)++ = *((uint8_t*)s)++; |
| ubhat | 0:42863a11464a | 346 | *d++ = *s++; |
| ubhat | 0:42863a11464a | 347 | } |
| ubhat | 0:42863a11464a | 348 | |
| ubhat | 0:42863a11464a | 349 | static void xor_block( void *d, const void *s ) |
| ubhat | 0:42863a11464a | 350 | { |
| ubhat | 0:42863a11464a | 351 | #if defined( HAVE_UINT_32T ) |
| ubhat | 0:42863a11464a | 352 | ((uint32_t*)d)[ 0] ^= ((uint32_t*)s)[ 0]; |
| ubhat | 0:42863a11464a | 353 | ((uint32_t*)d)[ 1] ^= ((uint32_t*)s)[ 1]; |
| ubhat | 0:42863a11464a | 354 | ((uint32_t*)d)[ 2] ^= ((uint32_t*)s)[ 2]; |
| ubhat | 0:42863a11464a | 355 | ((uint32_t*)d)[ 3] ^= ((uint32_t*)s)[ 3]; |
| ubhat | 0:42863a11464a | 356 | #else |
| ubhat | 0:42863a11464a | 357 | ((uint8_t*)d)[ 0] ^= ((uint8_t*)s)[ 0]; |
| ubhat | 0:42863a11464a | 358 | ((uint8_t*)d)[ 1] ^= ((uint8_t*)s)[ 1]; |
| ubhat | 0:42863a11464a | 359 | ((uint8_t*)d)[ 2] ^= ((uint8_t*)s)[ 2]; |
| ubhat | 0:42863a11464a | 360 | ((uint8_t*)d)[ 3] ^= ((uint8_t*)s)[ 3]; |
| ubhat | 0:42863a11464a | 361 | ((uint8_t*)d)[ 4] ^= ((uint8_t*)s)[ 4]; |
| ubhat | 0:42863a11464a | 362 | ((uint8_t*)d)[ 5] ^= ((uint8_t*)s)[ 5]; |
| ubhat | 0:42863a11464a | 363 | ((uint8_t*)d)[ 6] ^= ((uint8_t*)s)[ 6]; |
| ubhat | 0:42863a11464a | 364 | ((uint8_t*)d)[ 7] ^= ((uint8_t*)s)[ 7]; |
| ubhat | 0:42863a11464a | 365 | ((uint8_t*)d)[ 8] ^= ((uint8_t*)s)[ 8]; |
| ubhat | 0:42863a11464a | 366 | ((uint8_t*)d)[ 9] ^= ((uint8_t*)s)[ 9]; |
| ubhat | 0:42863a11464a | 367 | ((uint8_t*)d)[10] ^= ((uint8_t*)s)[10]; |
| ubhat | 0:42863a11464a | 368 | ((uint8_t*)d)[11] ^= ((uint8_t*)s)[11]; |
| ubhat | 0:42863a11464a | 369 | ((uint8_t*)d)[12] ^= ((uint8_t*)s)[12]; |
| ubhat | 0:42863a11464a | 370 | ((uint8_t*)d)[13] ^= ((uint8_t*)s)[13]; |
| ubhat | 0:42863a11464a | 371 | ((uint8_t*)d)[14] ^= ((uint8_t*)s)[14]; |
| ubhat | 0:42863a11464a | 372 | ((uint8_t*)d)[15] ^= ((uint8_t*)s)[15]; |
| ubhat | 0:42863a11464a | 373 | #endif |
| ubhat | 0:42863a11464a | 374 | } |
| ubhat | 0:42863a11464a | 375 | |
| ubhat | 0:42863a11464a | 376 | static void copy_and_key( void *d, const void *s, const void *k ) |
| ubhat | 0:42863a11464a | 377 | { |
| ubhat | 0:42863a11464a | 378 | #if defined( HAVE_UINT_32T ) |
| ubhat | 0:42863a11464a | 379 | ((uint32_t*)d)[ 0] = ((uint32_t*)s)[ 0] ^ ((uint32_t*)k)[ 0]; |
| ubhat | 0:42863a11464a | 380 | ((uint32_t*)d)[ 1] = ((uint32_t*)s)[ 1] ^ ((uint32_t*)k)[ 1]; |
| ubhat | 0:42863a11464a | 381 | ((uint32_t*)d)[ 2] = ((uint32_t*)s)[ 2] ^ ((uint32_t*)k)[ 2]; |
| ubhat | 0:42863a11464a | 382 | ((uint32_t*)d)[ 3] = ((uint32_t*)s)[ 3] ^ ((uint32_t*)k)[ 3]; |
| ubhat | 0:42863a11464a | 383 | #elif 1 |
| ubhat | 0:42863a11464a | 384 | ((uint8_t*)d)[ 0] = ((uint8_t*)s)[ 0] ^ ((uint8_t*)k)[ 0]; |
| ubhat | 0:42863a11464a | 385 | ((uint8_t*)d)[ 1] = ((uint8_t*)s)[ 1] ^ ((uint8_t*)k)[ 1]; |
| ubhat | 0:42863a11464a | 386 | ((uint8_t*)d)[ 2] = ((uint8_t*)s)[ 2] ^ ((uint8_t*)k)[ 2]; |
| ubhat | 0:42863a11464a | 387 | ((uint8_t*)d)[ 3] = ((uint8_t*)s)[ 3] ^ ((uint8_t*)k)[ 3]; |
| ubhat | 0:42863a11464a | 388 | ((uint8_t*)d)[ 4] = ((uint8_t*)s)[ 4] ^ ((uint8_t*)k)[ 4]; |
| ubhat | 0:42863a11464a | 389 | ((uint8_t*)d)[ 5] = ((uint8_t*)s)[ 5] ^ ((uint8_t*)k)[ 5]; |
| ubhat | 0:42863a11464a | 390 | ((uint8_t*)d)[ 6] = ((uint8_t*)s)[ 6] ^ ((uint8_t*)k)[ 6]; |
| ubhat | 0:42863a11464a | 391 | ((uint8_t*)d)[ 7] = ((uint8_t*)s)[ 7] ^ ((uint8_t*)k)[ 7]; |
| ubhat | 0:42863a11464a | 392 | ((uint8_t*)d)[ 8] = ((uint8_t*)s)[ 8] ^ ((uint8_t*)k)[ 8]; |
| ubhat | 0:42863a11464a | 393 | ((uint8_t*)d)[ 9] = ((uint8_t*)s)[ 9] ^ ((uint8_t*)k)[ 9]; |
| ubhat | 0:42863a11464a | 394 | ((uint8_t*)d)[10] = ((uint8_t*)s)[10] ^ ((uint8_t*)k)[10]; |
| ubhat | 0:42863a11464a | 395 | ((uint8_t*)d)[11] = ((uint8_t*)s)[11] ^ ((uint8_t*)k)[11]; |
| ubhat | 0:42863a11464a | 396 | ((uint8_t*)d)[12] = ((uint8_t*)s)[12] ^ ((uint8_t*)k)[12]; |
| ubhat | 0:42863a11464a | 397 | ((uint8_t*)d)[13] = ((uint8_t*)s)[13] ^ ((uint8_t*)k)[13]; |
| ubhat | 0:42863a11464a | 398 | ((uint8_t*)d)[14] = ((uint8_t*)s)[14] ^ ((uint8_t*)k)[14]; |
| ubhat | 0:42863a11464a | 399 | ((uint8_t*)d)[15] = ((uint8_t*)s)[15] ^ ((uint8_t*)k)[15]; |
| ubhat | 0:42863a11464a | 400 | #else |
| ubhat | 0:42863a11464a | 401 | block_copy(d, s); |
| ubhat | 0:42863a11464a | 402 | xor_block(d, k); |
| ubhat | 0:42863a11464a | 403 | #endif |
| ubhat | 0:42863a11464a | 404 | } |
| ubhat | 0:42863a11464a | 405 | |
| ubhat | 0:42863a11464a | 406 | static void add_round_key( uint8_t d[N_BLOCK], const uint8_t k[N_BLOCK] ) |
| ubhat | 0:42863a11464a | 407 | { |
| ubhat | 0:42863a11464a | 408 | xor_block(d, k); |
| ubhat | 0:42863a11464a | 409 | } |
| ubhat | 0:42863a11464a | 410 | |
| ubhat | 0:42863a11464a | 411 | static void shift_sub_rows( uint8_t st[N_BLOCK] ) |
| ubhat | 0:42863a11464a | 412 | { uint8_t tt; |
| ubhat | 0:42863a11464a | 413 | |
| ubhat | 0:42863a11464a | 414 | st[ 0] = s_box(st[ 0]); st[ 4] = s_box(st[ 4]); |
| ubhat | 0:42863a11464a | 415 | st[ 8] = s_box(st[ 8]); st[12] = s_box(st[12]); |
| ubhat | 0:42863a11464a | 416 | |
| ubhat | 0:42863a11464a | 417 | tt = st[1]; st[ 1] = s_box(st[ 5]); st[ 5] = s_box(st[ 9]); |
| ubhat | 0:42863a11464a | 418 | st[ 9] = s_box(st[13]); st[13] = s_box( tt ); |
| ubhat | 0:42863a11464a | 419 | |
| ubhat | 0:42863a11464a | 420 | tt = st[2]; st[ 2] = s_box(st[10]); st[10] = s_box( tt ); |
| ubhat | 0:42863a11464a | 421 | tt = st[6]; st[ 6] = s_box(st[14]); st[14] = s_box( tt ); |
| ubhat | 0:42863a11464a | 422 | |
| ubhat | 0:42863a11464a | 423 | tt = st[15]; st[15] = s_box(st[11]); st[11] = s_box(st[ 7]); |
| ubhat | 0:42863a11464a | 424 | st[ 7] = s_box(st[ 3]); st[ 3] = s_box( tt ); |
| ubhat | 0:42863a11464a | 425 | } |
| ubhat | 0:42863a11464a | 426 | |
| ubhat | 0:42863a11464a | 427 | #if defined( AES_DEC_PREKEYED ) |
| ubhat | 0:42863a11464a | 428 | |
| ubhat | 0:42863a11464a | 429 | static void inv_shift_sub_rows( uint8_t st[N_BLOCK] ) |
| ubhat | 0:42863a11464a | 430 | { uint8_t tt; |
| ubhat | 0:42863a11464a | 431 | |
| ubhat | 0:42863a11464a | 432 | st[ 0] = is_box(st[ 0]); st[ 4] = is_box(st[ 4]); |
| ubhat | 0:42863a11464a | 433 | st[ 8] = is_box(st[ 8]); st[12] = is_box(st[12]); |
| ubhat | 0:42863a11464a | 434 | |
| ubhat | 0:42863a11464a | 435 | tt = st[13]; st[13] = is_box(st[9]); st[ 9] = is_box(st[5]); |
| ubhat | 0:42863a11464a | 436 | st[ 5] = is_box(st[1]); st[ 1] = is_box( tt ); |
| ubhat | 0:42863a11464a | 437 | |
| ubhat | 0:42863a11464a | 438 | tt = st[2]; st[ 2] = is_box(st[10]); st[10] = is_box( tt ); |
| ubhat | 0:42863a11464a | 439 | tt = st[6]; st[ 6] = is_box(st[14]); st[14] = is_box( tt ); |
| ubhat | 0:42863a11464a | 440 | |
| ubhat | 0:42863a11464a | 441 | tt = st[3]; st[ 3] = is_box(st[ 7]); st[ 7] = is_box(st[11]); |
| ubhat | 0:42863a11464a | 442 | st[11] = is_box(st[15]); st[15] = is_box( tt ); |
| ubhat | 0:42863a11464a | 443 | } |
| ubhat | 0:42863a11464a | 444 | |
| ubhat | 0:42863a11464a | 445 | #endif |
| ubhat | 0:42863a11464a | 446 | |
| ubhat | 0:42863a11464a | 447 | #if defined( VERSION_1 ) |
| ubhat | 0:42863a11464a | 448 | static void mix_sub_columns( uint8_t dt[N_BLOCK] ) |
| ubhat | 0:42863a11464a | 449 | { uint8_t st[N_BLOCK]; |
| ubhat | 0:42863a11464a | 450 | block_copy(st, dt); |
| ubhat | 0:42863a11464a | 451 | #else |
| ubhat | 0:42863a11464a | 452 | static void mix_sub_columns( uint8_t dt[N_BLOCK], uint8_t st[N_BLOCK] ) |
| ubhat | 0:42863a11464a | 453 | { |
| ubhat | 0:42863a11464a | 454 | #endif |
| ubhat | 0:42863a11464a | 455 | dt[ 0] = gfm2_sb(st[0]) ^ gfm3_sb(st[5]) ^ s_box(st[10]) ^ s_box(st[15]); |
| ubhat | 0:42863a11464a | 456 | dt[ 1] = s_box(st[0]) ^ gfm2_sb(st[5]) ^ gfm3_sb(st[10]) ^ s_box(st[15]); |
| ubhat | 0:42863a11464a | 457 | dt[ 2] = s_box(st[0]) ^ s_box(st[5]) ^ gfm2_sb(st[10]) ^ gfm3_sb(st[15]); |
| ubhat | 0:42863a11464a | 458 | dt[ 3] = gfm3_sb(st[0]) ^ s_box(st[5]) ^ s_box(st[10]) ^ gfm2_sb(st[15]); |
| ubhat | 0:42863a11464a | 459 | |
| ubhat | 0:42863a11464a | 460 | dt[ 4] = gfm2_sb(st[4]) ^ gfm3_sb(st[9]) ^ s_box(st[14]) ^ s_box(st[3]); |
| ubhat | 0:42863a11464a | 461 | dt[ 5] = s_box(st[4]) ^ gfm2_sb(st[9]) ^ gfm3_sb(st[14]) ^ s_box(st[3]); |
| ubhat | 0:42863a11464a | 462 | dt[ 6] = s_box(st[4]) ^ s_box(st[9]) ^ gfm2_sb(st[14]) ^ gfm3_sb(st[3]); |
| ubhat | 0:42863a11464a | 463 | dt[ 7] = gfm3_sb(st[4]) ^ s_box(st[9]) ^ s_box(st[14]) ^ gfm2_sb(st[3]); |
| ubhat | 0:42863a11464a | 464 | |
| ubhat | 0:42863a11464a | 465 | dt[ 8] = gfm2_sb(st[8]) ^ gfm3_sb(st[13]) ^ s_box(st[2]) ^ s_box(st[7]); |
| ubhat | 0:42863a11464a | 466 | dt[ 9] = s_box(st[8]) ^ gfm2_sb(st[13]) ^ gfm3_sb(st[2]) ^ s_box(st[7]); |
| ubhat | 0:42863a11464a | 467 | dt[10] = s_box(st[8]) ^ s_box(st[13]) ^ gfm2_sb(st[2]) ^ gfm3_sb(st[7]); |
| ubhat | 0:42863a11464a | 468 | dt[11] = gfm3_sb(st[8]) ^ s_box(st[13]) ^ s_box(st[2]) ^ gfm2_sb(st[7]); |
| ubhat | 0:42863a11464a | 469 | |
| ubhat | 0:42863a11464a | 470 | dt[12] = gfm2_sb(st[12]) ^ gfm3_sb(st[1]) ^ s_box(st[6]) ^ s_box(st[11]); |
| ubhat | 0:42863a11464a | 471 | dt[13] = s_box(st[12]) ^ gfm2_sb(st[1]) ^ gfm3_sb(st[6]) ^ s_box(st[11]); |
| ubhat | 0:42863a11464a | 472 | dt[14] = s_box(st[12]) ^ s_box(st[1]) ^ gfm2_sb(st[6]) ^ gfm3_sb(st[11]); |
| ubhat | 0:42863a11464a | 473 | dt[15] = gfm3_sb(st[12]) ^ s_box(st[1]) ^ s_box(st[6]) ^ gfm2_sb(st[11]); |
| ubhat | 0:42863a11464a | 474 | } |
| ubhat | 0:42863a11464a | 475 | |
| ubhat | 0:42863a11464a | 476 | #if defined( AES_DEC_PREKEYED ) |
| ubhat | 0:42863a11464a | 477 | |
| ubhat | 0:42863a11464a | 478 | #if defined( VERSION_1 ) |
| ubhat | 0:42863a11464a | 479 | static void inv_mix_sub_columns( uint8_t dt[N_BLOCK] ) |
| ubhat | 0:42863a11464a | 480 | { uint8_t st[N_BLOCK]; |
| ubhat | 0:42863a11464a | 481 | block_copy(st, dt); |
| ubhat | 0:42863a11464a | 482 | #else |
| ubhat | 0:42863a11464a | 483 | static void inv_mix_sub_columns( uint8_t dt[N_BLOCK], uint8_t st[N_BLOCK] ) |
| ubhat | 0:42863a11464a | 484 | { |
| ubhat | 0:42863a11464a | 485 | #endif |
| ubhat | 0:42863a11464a | 486 | dt[ 0] = is_box(gfm_e(st[ 0]) ^ gfm_b(st[ 1]) ^ gfm_d(st[ 2]) ^ gfm_9(st[ 3])); |
| ubhat | 0:42863a11464a | 487 | dt[ 5] = is_box(gfm_9(st[ 0]) ^ gfm_e(st[ 1]) ^ gfm_b(st[ 2]) ^ gfm_d(st[ 3])); |
| ubhat | 0:42863a11464a | 488 | dt[10] = is_box(gfm_d(st[ 0]) ^ gfm_9(st[ 1]) ^ gfm_e(st[ 2]) ^ gfm_b(st[ 3])); |
| ubhat | 0:42863a11464a | 489 | dt[15] = is_box(gfm_b(st[ 0]) ^ gfm_d(st[ 1]) ^ gfm_9(st[ 2]) ^ gfm_e(st[ 3])); |
| ubhat | 0:42863a11464a | 490 | |
| ubhat | 0:42863a11464a | 491 | dt[ 4] = is_box(gfm_e(st[ 4]) ^ gfm_b(st[ 5]) ^ gfm_d(st[ 6]) ^ gfm_9(st[ 7])); |
| ubhat | 0:42863a11464a | 492 | dt[ 9] = is_box(gfm_9(st[ 4]) ^ gfm_e(st[ 5]) ^ gfm_b(st[ 6]) ^ gfm_d(st[ 7])); |
| ubhat | 0:42863a11464a | 493 | dt[14] = is_box(gfm_d(st[ 4]) ^ gfm_9(st[ 5]) ^ gfm_e(st[ 6]) ^ gfm_b(st[ 7])); |
| ubhat | 0:42863a11464a | 494 | dt[ 3] = is_box(gfm_b(st[ 4]) ^ gfm_d(st[ 5]) ^ gfm_9(st[ 6]) ^ gfm_e(st[ 7])); |
| ubhat | 0:42863a11464a | 495 | |
| ubhat | 0:42863a11464a | 496 | dt[ 8] = is_box(gfm_e(st[ 8]) ^ gfm_b(st[ 9]) ^ gfm_d(st[10]) ^ gfm_9(st[11])); |
| ubhat | 0:42863a11464a | 497 | dt[13] = is_box(gfm_9(st[ 8]) ^ gfm_e(st[ 9]) ^ gfm_b(st[10]) ^ gfm_d(st[11])); |
| ubhat | 0:42863a11464a | 498 | dt[ 2] = is_box(gfm_d(st[ 8]) ^ gfm_9(st[ 9]) ^ gfm_e(st[10]) ^ gfm_b(st[11])); |
| ubhat | 0:42863a11464a | 499 | dt[ 7] = is_box(gfm_b(st[ 8]) ^ gfm_d(st[ 9]) ^ gfm_9(st[10]) ^ gfm_e(st[11])); |
| ubhat | 0:42863a11464a | 500 | |
| ubhat | 0:42863a11464a | 501 | dt[12] = is_box(gfm_e(st[12]) ^ gfm_b(st[13]) ^ gfm_d(st[14]) ^ gfm_9(st[15])); |
| ubhat | 0:42863a11464a | 502 | dt[ 1] = is_box(gfm_9(st[12]) ^ gfm_e(st[13]) ^ gfm_b(st[14]) ^ gfm_d(st[15])); |
| ubhat | 0:42863a11464a | 503 | dt[ 6] = is_box(gfm_d(st[12]) ^ gfm_9(st[13]) ^ gfm_e(st[14]) ^ gfm_b(st[15])); |
| ubhat | 0:42863a11464a | 504 | dt[11] = is_box(gfm_b(st[12]) ^ gfm_d(st[13]) ^ gfm_9(st[14]) ^ gfm_e(st[15])); |
| ubhat | 0:42863a11464a | 505 | } |
| ubhat | 0:42863a11464a | 506 | |
| ubhat | 0:42863a11464a | 507 | #endif |
| ubhat | 0:42863a11464a | 508 | |
| ubhat | 0:42863a11464a | 509 | #if defined( AES_ENC_PREKEYED ) || defined( AES_DEC_PREKEYED ) |
| ubhat | 0:42863a11464a | 510 | |
| ubhat | 0:42863a11464a | 511 | /* Set the cipher key for the pre-keyed version */ |
| ubhat | 0:42863a11464a | 512 | |
| ubhat | 0:42863a11464a | 513 | return_type aes_set_key( const uint8_t key[], length_type keylen, aes_context ctx[1] ) |
| ubhat | 0:42863a11464a | 514 | { |
| ubhat | 0:42863a11464a | 515 | uint8_t cc, rc, hi; |
| ubhat | 0:42863a11464a | 516 | |
| ubhat | 0:42863a11464a | 517 | switch( keylen ) |
| ubhat | 0:42863a11464a | 518 | { |
| ubhat | 0:42863a11464a | 519 | case 16: |
| ubhat | 0:42863a11464a | 520 | case 24: |
| ubhat | 0:42863a11464a | 521 | case 32: |
| ubhat | 0:42863a11464a | 522 | break; |
| ubhat | 0:42863a11464a | 523 | default: |
| ubhat | 0:42863a11464a | 524 | ctx->rnd = 0; |
| ubhat | 0:42863a11464a | 525 | return ( uint8_t )-1; |
| ubhat | 0:42863a11464a | 526 | } |
| ubhat | 0:42863a11464a | 527 | block_copy_nn(ctx->ksch, key, keylen); |
| ubhat | 0:42863a11464a | 528 | hi = (keylen + 28) << 2; |
| ubhat | 0:42863a11464a | 529 | ctx->rnd = (hi >> 4) - 1; |
| ubhat | 0:42863a11464a | 530 | for( cc = keylen, rc = 1; cc < hi; cc += 4 ) |
| ubhat | 0:42863a11464a | 531 | { uint8_t tt, t0, t1, t2, t3; |
| ubhat | 0:42863a11464a | 532 | |
| ubhat | 0:42863a11464a | 533 | t0 = ctx->ksch[cc - 4]; |
| ubhat | 0:42863a11464a | 534 | t1 = ctx->ksch[cc - 3]; |
| ubhat | 0:42863a11464a | 535 | t2 = ctx->ksch[cc - 2]; |
| ubhat | 0:42863a11464a | 536 | t3 = ctx->ksch[cc - 1]; |
| ubhat | 0:42863a11464a | 537 | if( cc % keylen == 0 ) |
| ubhat | 0:42863a11464a | 538 | { |
| ubhat | 0:42863a11464a | 539 | tt = t0; |
| ubhat | 0:42863a11464a | 540 | t0 = s_box(t1) ^ rc; |
| ubhat | 0:42863a11464a | 541 | t1 = s_box(t2); |
| ubhat | 0:42863a11464a | 542 | t2 = s_box(t3); |
| ubhat | 0:42863a11464a | 543 | t3 = s_box(tt); |
| ubhat | 0:42863a11464a | 544 | rc = f2(rc); |
| ubhat | 0:42863a11464a | 545 | } |
| ubhat | 0:42863a11464a | 546 | else if( keylen > 24 && cc % keylen == 16 ) |
| ubhat | 0:42863a11464a | 547 | { |
| ubhat | 0:42863a11464a | 548 | t0 = s_box(t0); |
| ubhat | 0:42863a11464a | 549 | t1 = s_box(t1); |
| ubhat | 0:42863a11464a | 550 | t2 = s_box(t2); |
| ubhat | 0:42863a11464a | 551 | t3 = s_box(t3); |
| ubhat | 0:42863a11464a | 552 | } |
| ubhat | 0:42863a11464a | 553 | tt = cc - keylen; |
| ubhat | 0:42863a11464a | 554 | ctx->ksch[cc + 0] = ctx->ksch[tt + 0] ^ t0; |
| ubhat | 0:42863a11464a | 555 | ctx->ksch[cc + 1] = ctx->ksch[tt + 1] ^ t1; |
| ubhat | 0:42863a11464a | 556 | ctx->ksch[cc + 2] = ctx->ksch[tt + 2] ^ t2; |
| ubhat | 0:42863a11464a | 557 | ctx->ksch[cc + 3] = ctx->ksch[tt + 3] ^ t3; |
| ubhat | 0:42863a11464a | 558 | } |
| ubhat | 0:42863a11464a | 559 | return 0; |
| ubhat | 0:42863a11464a | 560 | } |
| ubhat | 0:42863a11464a | 561 | |
| ubhat | 0:42863a11464a | 562 | #endif |
| ubhat | 0:42863a11464a | 563 | |
| ubhat | 0:42863a11464a | 564 | #if defined( AES_ENC_PREKEYED ) |
| ubhat | 0:42863a11464a | 565 | |
| ubhat | 0:42863a11464a | 566 | /* Encrypt a single block of 16 bytes */ |
| ubhat | 0:42863a11464a | 567 | |
| ubhat | 0:42863a11464a | 568 | return_type aes_encrypt( const uint8_t in[N_BLOCK], uint8_t out[N_BLOCK], const aes_context ctx[1] ) |
| ubhat | 0:42863a11464a | 569 | { |
| ubhat | 0:42863a11464a | 570 | if( ctx->rnd ) |
| ubhat | 0:42863a11464a | 571 | { |
| ubhat | 0:42863a11464a | 572 | uint8_t s1[N_BLOCK], r; |
| ubhat | 0:42863a11464a | 573 | copy_and_key( s1, in, ctx->ksch ); |
| ubhat | 0:42863a11464a | 574 | |
| ubhat | 0:42863a11464a | 575 | for( r = 1 ; r < ctx->rnd ; ++r ) |
| ubhat | 0:42863a11464a | 576 | #if defined( VERSION_1 ) |
| ubhat | 0:42863a11464a | 577 | { |
| ubhat | 0:42863a11464a | 578 | mix_sub_columns( s1 ); |
| ubhat | 0:42863a11464a | 579 | add_round_key( s1, ctx->ksch + r * N_BLOCK); |
| ubhat | 0:42863a11464a | 580 | } |
| ubhat | 0:42863a11464a | 581 | #else |
| ubhat | 0:42863a11464a | 582 | { uint8_t s2[N_BLOCK]; |
| ubhat | 0:42863a11464a | 583 | mix_sub_columns( s2, s1 ); |
| ubhat | 0:42863a11464a | 584 | copy_and_key( s1, s2, ctx->ksch + r * N_BLOCK); |
| ubhat | 0:42863a11464a | 585 | } |
| ubhat | 0:42863a11464a | 586 | #endif |
| ubhat | 0:42863a11464a | 587 | shift_sub_rows( s1 ); |
| ubhat | 0:42863a11464a | 588 | copy_and_key( out, s1, ctx->ksch + r * N_BLOCK ); |
| ubhat | 0:42863a11464a | 589 | } |
| ubhat | 0:42863a11464a | 590 | else |
| ubhat | 0:42863a11464a | 591 | return ( uint8_t )-1; |
| ubhat | 0:42863a11464a | 592 | return 0; |
| ubhat | 0:42863a11464a | 593 | } |
| ubhat | 0:42863a11464a | 594 | |
| ubhat | 0:42863a11464a | 595 | /* CBC encrypt a number of blocks (input and return an IV) */ |
| ubhat | 0:42863a11464a | 596 | |
| ubhat | 0:42863a11464a | 597 | return_type aes_cbc_encrypt( const uint8_t *in, uint8_t *out, |
| ubhat | 0:42863a11464a | 598 | int32_t n_block, uint8_t iv[N_BLOCK], const aes_context ctx[1] ) |
| ubhat | 0:42863a11464a | 599 | { |
| ubhat | 0:42863a11464a | 600 | |
| ubhat | 0:42863a11464a | 601 | while(n_block--) |
| ubhat | 0:42863a11464a | 602 | { |
| ubhat | 0:42863a11464a | 603 | xor_block(iv, in); |
| ubhat | 0:42863a11464a | 604 | if(aes_encrypt(iv, iv, ctx) != EXIT_SUCCESS) |
| ubhat | 0:42863a11464a | 605 | return EXIT_FAILURE; |
| ubhat | 0:42863a11464a | 606 | //memcpy(out, iv, N_BLOCK); |
| ubhat | 0:42863a11464a | 607 | block_copy(out, iv); |
| ubhat | 0:42863a11464a | 608 | in += N_BLOCK; |
| ubhat | 0:42863a11464a | 609 | out += N_BLOCK; |
| ubhat | 0:42863a11464a | 610 | } |
| ubhat | 0:42863a11464a | 611 | return EXIT_SUCCESS; |
| ubhat | 0:42863a11464a | 612 | } |
| ubhat | 0:42863a11464a | 613 | |
| ubhat | 0:42863a11464a | 614 | #endif |
| ubhat | 0:42863a11464a | 615 | |
| ubhat | 0:42863a11464a | 616 | #if defined( AES_DEC_PREKEYED ) |
| ubhat | 0:42863a11464a | 617 | |
| ubhat | 0:42863a11464a | 618 | /* Decrypt a single block of 16 bytes */ |
| ubhat | 0:42863a11464a | 619 | |
| ubhat | 0:42863a11464a | 620 | return_type aes_decrypt( const uint8_t in[N_BLOCK], uint8_t out[N_BLOCK], const aes_context ctx[1] ) |
| ubhat | 0:42863a11464a | 621 | { |
| ubhat | 0:42863a11464a | 622 | if( ctx->rnd ) |
| ubhat | 0:42863a11464a | 623 | { |
| ubhat | 0:42863a11464a | 624 | uint8_t s1[N_BLOCK], r; |
| ubhat | 0:42863a11464a | 625 | copy_and_key( s1, in, ctx->ksch + ctx->rnd * N_BLOCK ); |
| ubhat | 0:42863a11464a | 626 | inv_shift_sub_rows( s1 ); |
| ubhat | 0:42863a11464a | 627 | |
| ubhat | 0:42863a11464a | 628 | for( r = ctx->rnd ; --r ; ) |
| ubhat | 0:42863a11464a | 629 | #if defined( VERSION_1 ) |
| ubhat | 0:42863a11464a | 630 | { |
| ubhat | 0:42863a11464a | 631 | add_round_key( s1, ctx->ksch + r * N_BLOCK ); |
| ubhat | 0:42863a11464a | 632 | inv_mix_sub_columns( s1 ); |
| ubhat | 0:42863a11464a | 633 | } |
| ubhat | 0:42863a11464a | 634 | #else |
| ubhat | 0:42863a11464a | 635 | { uint8_t s2[N_BLOCK]; |
| ubhat | 0:42863a11464a | 636 | copy_and_key( s2, s1, ctx->ksch + r * N_BLOCK ); |
| ubhat | 0:42863a11464a | 637 | inv_mix_sub_columns( s1, s2 ); |
| ubhat | 0:42863a11464a | 638 | } |
| ubhat | 0:42863a11464a | 639 | #endif |
| ubhat | 0:42863a11464a | 640 | copy_and_key( out, s1, ctx->ksch ); |
| ubhat | 0:42863a11464a | 641 | } |
| ubhat | 0:42863a11464a | 642 | else |
| ubhat | 0:42863a11464a | 643 | return -1; |
| ubhat | 0:42863a11464a | 644 | return 0; |
| ubhat | 0:42863a11464a | 645 | } |
| ubhat | 0:42863a11464a | 646 | |
| ubhat | 0:42863a11464a | 647 | /* CBC decrypt a number of blocks (input and return an IV) */ |
| ubhat | 0:42863a11464a | 648 | |
| ubhat | 0:42863a11464a | 649 | return_type aes_cbc_decrypt( const uint8_t *in, uint8_t *out, |
| ubhat | 0:42863a11464a | 650 | int32_t n_block, uint8_t iv[N_BLOCK], const aes_context ctx[1] ) |
| ubhat | 0:42863a11464a | 651 | { |
| ubhat | 0:42863a11464a | 652 | while(n_block--) |
| ubhat | 0:42863a11464a | 653 | { uint8_t tmp[N_BLOCK]; |
| ubhat | 0:42863a11464a | 654 | |
| ubhat | 0:42863a11464a | 655 | //memcpy(tmp, in, N_BLOCK); |
| ubhat | 0:42863a11464a | 656 | block_copy(tmp, in); |
| ubhat | 0:42863a11464a | 657 | if(aes_decrypt(in, out, ctx) != EXIT_SUCCESS) |
| ubhat | 0:42863a11464a | 658 | return EXIT_FAILURE; |
| ubhat | 0:42863a11464a | 659 | xor_block(out, iv); |
| ubhat | 0:42863a11464a | 660 | //memcpy(iv, tmp, N_BLOCK); |
| ubhat | 0:42863a11464a | 661 | block_copy(iv, tmp); |
| ubhat | 0:42863a11464a | 662 | in += N_BLOCK; |
| ubhat | 0:42863a11464a | 663 | out += N_BLOCK; |
| ubhat | 0:42863a11464a | 664 | } |
| ubhat | 0:42863a11464a | 665 | return EXIT_SUCCESS; |
| ubhat | 0:42863a11464a | 666 | } |
| ubhat | 0:42863a11464a | 667 | |
| ubhat | 0:42863a11464a | 668 | #endif |
| ubhat | 0:42863a11464a | 669 | |
| ubhat | 0:42863a11464a | 670 | #if defined( AES_ENC_128_OTFK ) |
| ubhat | 0:42863a11464a | 671 | |
| ubhat | 0:42863a11464a | 672 | /* The 'on the fly' encryption key update for for 128 bit keys */ |
| ubhat | 0:42863a11464a | 673 | |
| ubhat | 0:42863a11464a | 674 | static void update_encrypt_key_128( uint8_t k[N_BLOCK], uint8_t *rc ) |
| ubhat | 0:42863a11464a | 675 | { uint8_t cc; |
| ubhat | 0:42863a11464a | 676 | |
| ubhat | 0:42863a11464a | 677 | k[0] ^= s_box(k[13]) ^ *rc; |
| ubhat | 0:42863a11464a | 678 | k[1] ^= s_box(k[14]); |
| ubhat | 0:42863a11464a | 679 | k[2] ^= s_box(k[15]); |
| ubhat | 0:42863a11464a | 680 | k[3] ^= s_box(k[12]); |
| ubhat | 0:42863a11464a | 681 | *rc = f2( *rc ); |
| ubhat | 0:42863a11464a | 682 | |
| ubhat | 0:42863a11464a | 683 | for(cc = 4; cc < 16; cc += 4 ) |
| ubhat | 0:42863a11464a | 684 | { |
| ubhat | 0:42863a11464a | 685 | k[cc + 0] ^= k[cc - 4]; |
| ubhat | 0:42863a11464a | 686 | k[cc + 1] ^= k[cc - 3]; |
| ubhat | 0:42863a11464a | 687 | k[cc + 2] ^= k[cc - 2]; |
| ubhat | 0:42863a11464a | 688 | k[cc + 3] ^= k[cc - 1]; |
| ubhat | 0:42863a11464a | 689 | } |
| ubhat | 0:42863a11464a | 690 | } |
| ubhat | 0:42863a11464a | 691 | |
| ubhat | 0:42863a11464a | 692 | /* Encrypt a single block of 16 bytes with 'on the fly' 128 bit keying */ |
| ubhat | 0:42863a11464a | 693 | |
| ubhat | 0:42863a11464a | 694 | void aes_encrypt_128( const uint8_t in[N_BLOCK], uint8_t out[N_BLOCK], |
| ubhat | 0:42863a11464a | 695 | const uint8_t key[N_BLOCK], uint8_t o_key[N_BLOCK] ) |
| ubhat | 0:42863a11464a | 696 | { uint8_t s1[N_BLOCK], r, rc = 1; |
| ubhat | 0:42863a11464a | 697 | |
| ubhat | 0:42863a11464a | 698 | if(o_key != key) |
| ubhat | 0:42863a11464a | 699 | block_copy( o_key, key ); |
| ubhat | 0:42863a11464a | 700 | copy_and_key( s1, in, o_key ); |
| ubhat | 0:42863a11464a | 701 | |
| ubhat | 0:42863a11464a | 702 | for( r = 1 ; r < 10 ; ++r ) |
| ubhat | 0:42863a11464a | 703 | #if defined( VERSION_1 ) |
| ubhat | 0:42863a11464a | 704 | { |
| ubhat | 0:42863a11464a | 705 | mix_sub_columns( s1 ); |
| ubhat | 0:42863a11464a | 706 | update_encrypt_key_128( o_key, &rc ); |
| ubhat | 0:42863a11464a | 707 | add_round_key( s1, o_key ); |
| ubhat | 0:42863a11464a | 708 | } |
| ubhat | 0:42863a11464a | 709 | #else |
| ubhat | 0:42863a11464a | 710 | { uint8_t s2[N_BLOCK]; |
| ubhat | 0:42863a11464a | 711 | mix_sub_columns( s2, s1 ); |
| ubhat | 0:42863a11464a | 712 | update_encrypt_key_128( o_key, &rc ); |
| ubhat | 0:42863a11464a | 713 | copy_and_key( s1, s2, o_key ); |
| ubhat | 0:42863a11464a | 714 | } |
| ubhat | 0:42863a11464a | 715 | #endif |
| ubhat | 0:42863a11464a | 716 | |
| ubhat | 0:42863a11464a | 717 | shift_sub_rows( s1 ); |
| ubhat | 0:42863a11464a | 718 | update_encrypt_key_128( o_key, &rc ); |
| ubhat | 0:42863a11464a | 719 | copy_and_key( out, s1, o_key ); |
| ubhat | 0:42863a11464a | 720 | } |
| ubhat | 0:42863a11464a | 721 | |
| ubhat | 0:42863a11464a | 722 | #endif |
| ubhat | 0:42863a11464a | 723 | |
| ubhat | 0:42863a11464a | 724 | #if defined( AES_DEC_128_OTFK ) |
| ubhat | 0:42863a11464a | 725 | |
| ubhat | 0:42863a11464a | 726 | /* The 'on the fly' decryption key update for for 128 bit keys */ |
| ubhat | 0:42863a11464a | 727 | |
| ubhat | 0:42863a11464a | 728 | static void update_decrypt_key_128( uint8_t k[N_BLOCK], uint8_t *rc ) |
| ubhat | 0:42863a11464a | 729 | { uint8_t cc; |
| ubhat | 0:42863a11464a | 730 | |
| ubhat | 0:42863a11464a | 731 | for( cc = 12; cc > 0; cc -= 4 ) |
| ubhat | 0:42863a11464a | 732 | { |
| ubhat | 0:42863a11464a | 733 | k[cc + 0] ^= k[cc - 4]; |
| ubhat | 0:42863a11464a | 734 | k[cc + 1] ^= k[cc - 3]; |
| ubhat | 0:42863a11464a | 735 | k[cc + 2] ^= k[cc - 2]; |
| ubhat | 0:42863a11464a | 736 | k[cc + 3] ^= k[cc - 1]; |
| ubhat | 0:42863a11464a | 737 | } |
| ubhat | 0:42863a11464a | 738 | *rc = d2(*rc); |
| ubhat | 0:42863a11464a | 739 | k[0] ^= s_box(k[13]) ^ *rc; |
| ubhat | 0:42863a11464a | 740 | k[1] ^= s_box(k[14]); |
| ubhat | 0:42863a11464a | 741 | k[2] ^= s_box(k[15]); |
| ubhat | 0:42863a11464a | 742 | k[3] ^= s_box(k[12]); |
| ubhat | 0:42863a11464a | 743 | } |
| ubhat | 0:42863a11464a | 744 | |
| ubhat | 0:42863a11464a | 745 | /* Decrypt a single block of 16 bytes with 'on the fly' 128 bit keying */ |
| ubhat | 0:42863a11464a | 746 | |
| ubhat | 0:42863a11464a | 747 | void aes_decrypt_128( const uint8_t in[N_BLOCK], uint8_t out[N_BLOCK], |
| ubhat | 0:42863a11464a | 748 | const uint8_t key[N_BLOCK], uint8_t o_key[N_BLOCK] ) |
| ubhat | 0:42863a11464a | 749 | { |
| ubhat | 0:42863a11464a | 750 | uint8_t s1[N_BLOCK], r, rc = 0x6c; |
| ubhat | 0:42863a11464a | 751 | if(o_key != key) |
| ubhat | 0:42863a11464a | 752 | block_copy( o_key, key ); |
| ubhat | 0:42863a11464a | 753 | |
| ubhat | 0:42863a11464a | 754 | copy_and_key( s1, in, o_key ); |
| ubhat | 0:42863a11464a | 755 | inv_shift_sub_rows( s1 ); |
| ubhat | 0:42863a11464a | 756 | |
| ubhat | 0:42863a11464a | 757 | for( r = 10 ; --r ; ) |
| ubhat | 0:42863a11464a | 758 | #if defined( VERSION_1 ) |
| ubhat | 0:42863a11464a | 759 | { |
| ubhat | 0:42863a11464a | 760 | update_decrypt_key_128( o_key, &rc ); |
| ubhat | 0:42863a11464a | 761 | add_round_key( s1, o_key ); |
| ubhat | 0:42863a11464a | 762 | inv_mix_sub_columns( s1 ); |
| ubhat | 0:42863a11464a | 763 | } |
| ubhat | 0:42863a11464a | 764 | #else |
| ubhat | 0:42863a11464a | 765 | { uint8_t s2[N_BLOCK]; |
| ubhat | 0:42863a11464a | 766 | update_decrypt_key_128( o_key, &rc ); |
| ubhat | 0:42863a11464a | 767 | copy_and_key( s2, s1, o_key ); |
| ubhat | 0:42863a11464a | 768 | inv_mix_sub_columns( s1, s2 ); |
| ubhat | 0:42863a11464a | 769 | } |
| ubhat | 0:42863a11464a | 770 | #endif |
| ubhat | 0:42863a11464a | 771 | update_decrypt_key_128( o_key, &rc ); |
| ubhat | 0:42863a11464a | 772 | copy_and_key( out, s1, o_key ); |
| ubhat | 0:42863a11464a | 773 | } |
| ubhat | 0:42863a11464a | 774 | |
| ubhat | 0:42863a11464a | 775 | #endif |
| ubhat | 0:42863a11464a | 776 | |
| ubhat | 0:42863a11464a | 777 | #if defined( AES_ENC_256_OTFK ) |
| ubhat | 0:42863a11464a | 778 | |
| ubhat | 0:42863a11464a | 779 | /* The 'on the fly' encryption key update for for 256 bit keys */ |
| ubhat | 0:42863a11464a | 780 | |
| ubhat | 0:42863a11464a | 781 | static void update_encrypt_key_256( uint8_t k[2 * N_BLOCK], uint8_t *rc ) |
| ubhat | 0:42863a11464a | 782 | { uint8_t cc; |
| ubhat | 0:42863a11464a | 783 | |
| ubhat | 0:42863a11464a | 784 | k[0] ^= s_box(k[29]) ^ *rc; |
| ubhat | 0:42863a11464a | 785 | k[1] ^= s_box(k[30]); |
| ubhat | 0:42863a11464a | 786 | k[2] ^= s_box(k[31]); |
| ubhat | 0:42863a11464a | 787 | k[3] ^= s_box(k[28]); |
| ubhat | 0:42863a11464a | 788 | *rc = f2( *rc ); |
| ubhat | 0:42863a11464a | 789 | |
| ubhat | 0:42863a11464a | 790 | for(cc = 4; cc < 16; cc += 4) |
| ubhat | 0:42863a11464a | 791 | { |
| ubhat | 0:42863a11464a | 792 | k[cc + 0] ^= k[cc - 4]; |
| ubhat | 0:42863a11464a | 793 | k[cc + 1] ^= k[cc - 3]; |
| ubhat | 0:42863a11464a | 794 | k[cc + 2] ^= k[cc - 2]; |
| ubhat | 0:42863a11464a | 795 | k[cc + 3] ^= k[cc - 1]; |
| ubhat | 0:42863a11464a | 796 | } |
| ubhat | 0:42863a11464a | 797 | |
| ubhat | 0:42863a11464a | 798 | k[16] ^= s_box(k[12]); |
| ubhat | 0:42863a11464a | 799 | k[17] ^= s_box(k[13]); |
| ubhat | 0:42863a11464a | 800 | k[18] ^= s_box(k[14]); |
| ubhat | 0:42863a11464a | 801 | k[19] ^= s_box(k[15]); |
| ubhat | 0:42863a11464a | 802 | |
| ubhat | 0:42863a11464a | 803 | for( cc = 20; cc < 32; cc += 4 ) |
| ubhat | 0:42863a11464a | 804 | { |
| ubhat | 0:42863a11464a | 805 | k[cc + 0] ^= k[cc - 4]; |
| ubhat | 0:42863a11464a | 806 | k[cc + 1] ^= k[cc - 3]; |
| ubhat | 0:42863a11464a | 807 | k[cc + 2] ^= k[cc - 2]; |
| ubhat | 0:42863a11464a | 808 | k[cc + 3] ^= k[cc - 1]; |
| ubhat | 0:42863a11464a | 809 | } |
| ubhat | 0:42863a11464a | 810 | } |
| ubhat | 0:42863a11464a | 811 | |
| ubhat | 0:42863a11464a | 812 | /* Encrypt a single block of 16 bytes with 'on the fly' 256 bit keying */ |
| ubhat | 0:42863a11464a | 813 | |
| ubhat | 0:42863a11464a | 814 | void aes_encrypt_256( const uint8_t in[N_BLOCK], uint8_t out[N_BLOCK], |
| ubhat | 0:42863a11464a | 815 | const uint8_t key[2 * N_BLOCK], uint8_t o_key[2 * N_BLOCK] ) |
| ubhat | 0:42863a11464a | 816 | { |
| ubhat | 0:42863a11464a | 817 | uint8_t s1[N_BLOCK], r, rc = 1; |
| ubhat | 0:42863a11464a | 818 | if(o_key != key) |
| ubhat | 0:42863a11464a | 819 | { |
| ubhat | 0:42863a11464a | 820 | block_copy( o_key, key ); |
| ubhat | 0:42863a11464a | 821 | block_copy( o_key + 16, key + 16 ); |
| ubhat | 0:42863a11464a | 822 | } |
| ubhat | 0:42863a11464a | 823 | copy_and_key( s1, in, o_key ); |
| ubhat | 0:42863a11464a | 824 | |
| ubhat | 0:42863a11464a | 825 | for( r = 1 ; r < 14 ; ++r ) |
| ubhat | 0:42863a11464a | 826 | #if defined( VERSION_1 ) |
| ubhat | 0:42863a11464a | 827 | { |
| ubhat | 0:42863a11464a | 828 | mix_sub_columns(s1); |
| ubhat | 0:42863a11464a | 829 | if( r & 1 ) |
| ubhat | 0:42863a11464a | 830 | add_round_key( s1, o_key + 16 ); |
| ubhat | 0:42863a11464a | 831 | else |
| ubhat | 0:42863a11464a | 832 | { |
| ubhat | 0:42863a11464a | 833 | update_encrypt_key_256( o_key, &rc ); |
| ubhat | 0:42863a11464a | 834 | add_round_key( s1, o_key ); |
| ubhat | 0:42863a11464a | 835 | } |
| ubhat | 0:42863a11464a | 836 | } |
| ubhat | 0:42863a11464a | 837 | #else |
| ubhat | 0:42863a11464a | 838 | { uint8_t s2[N_BLOCK]; |
| ubhat | 0:42863a11464a | 839 | mix_sub_columns( s2, s1 ); |
| ubhat | 0:42863a11464a | 840 | if( r & 1 ) |
| ubhat | 0:42863a11464a | 841 | copy_and_key( s1, s2, o_key + 16 ); |
| ubhat | 0:42863a11464a | 842 | else |
| ubhat | 0:42863a11464a | 843 | { |
| ubhat | 0:42863a11464a | 844 | update_encrypt_key_256( o_key, &rc ); |
| ubhat | 0:42863a11464a | 845 | copy_and_key( s1, s2, o_key ); |
| ubhat | 0:42863a11464a | 846 | } |
| ubhat | 0:42863a11464a | 847 | } |
| ubhat | 0:42863a11464a | 848 | #endif |
| ubhat | 0:42863a11464a | 849 | |
| ubhat | 0:42863a11464a | 850 | shift_sub_rows( s1 ); |
| ubhat | 0:42863a11464a | 851 | update_encrypt_key_256( o_key, &rc ); |
| ubhat | 0:42863a11464a | 852 | copy_and_key( out, s1, o_key ); |
| ubhat | 0:42863a11464a | 853 | } |
| ubhat | 0:42863a11464a | 854 | |
| ubhat | 0:42863a11464a | 855 | #endif |
| ubhat | 0:42863a11464a | 856 | |
| ubhat | 0:42863a11464a | 857 | #if defined( AES_DEC_256_OTFK ) |
| ubhat | 0:42863a11464a | 858 | |
| ubhat | 0:42863a11464a | 859 | /* The 'on the fly' encryption key update for for 256 bit keys */ |
| ubhat | 0:42863a11464a | 860 | |
| ubhat | 0:42863a11464a | 861 | static void update_decrypt_key_256( uint8_t k[2 * N_BLOCK], uint8_t *rc ) |
| ubhat | 0:42863a11464a | 862 | { uint8_t cc; |
| ubhat | 0:42863a11464a | 863 | |
| ubhat | 0:42863a11464a | 864 | for(cc = 28; cc > 16; cc -= 4) |
| ubhat | 0:42863a11464a | 865 | { |
| ubhat | 0:42863a11464a | 866 | k[cc + 0] ^= k[cc - 4]; |
| ubhat | 0:42863a11464a | 867 | k[cc + 1] ^= k[cc - 3]; |
| ubhat | 0:42863a11464a | 868 | k[cc + 2] ^= k[cc - 2]; |
| ubhat | 0:42863a11464a | 869 | k[cc + 3] ^= k[cc - 1]; |
| ubhat | 0:42863a11464a | 870 | } |
| ubhat | 0:42863a11464a | 871 | |
| ubhat | 0:42863a11464a | 872 | k[16] ^= s_box(k[12]); |
| ubhat | 0:42863a11464a | 873 | k[17] ^= s_box(k[13]); |
| ubhat | 0:42863a11464a | 874 | k[18] ^= s_box(k[14]); |
| ubhat | 0:42863a11464a | 875 | k[19] ^= s_box(k[15]); |
| ubhat | 0:42863a11464a | 876 | |
| ubhat | 0:42863a11464a | 877 | for(cc = 12; cc > 0; cc -= 4) |
| ubhat | 0:42863a11464a | 878 | { |
| ubhat | 0:42863a11464a | 879 | k[cc + 0] ^= k[cc - 4]; |
| ubhat | 0:42863a11464a | 880 | k[cc + 1] ^= k[cc - 3]; |
| ubhat | 0:42863a11464a | 881 | k[cc + 2] ^= k[cc - 2]; |
| ubhat | 0:42863a11464a | 882 | k[cc + 3] ^= k[cc - 1]; |
| ubhat | 0:42863a11464a | 883 | } |
| ubhat | 0:42863a11464a | 884 | |
| ubhat | 0:42863a11464a | 885 | *rc = d2(*rc); |
| ubhat | 0:42863a11464a | 886 | k[0] ^= s_box(k[29]) ^ *rc; |
| ubhat | 0:42863a11464a | 887 | k[1] ^= s_box(k[30]); |
| ubhat | 0:42863a11464a | 888 | k[2] ^= s_box(k[31]); |
| ubhat | 0:42863a11464a | 889 | k[3] ^= s_box(k[28]); |
| ubhat | 0:42863a11464a | 890 | } |
| ubhat | 0:42863a11464a | 891 | |
| ubhat | 0:42863a11464a | 892 | /* Decrypt a single block of 16 bytes with 'on the fly' |
| ubhat | 0:42863a11464a | 893 | 256 bit keying |
| ubhat | 0:42863a11464a | 894 | */ |
| ubhat | 0:42863a11464a | 895 | void aes_decrypt_256( const uint8_t in[N_BLOCK], uint8_t out[N_BLOCK], |
| ubhat | 0:42863a11464a | 896 | const uint8_t key[2 * N_BLOCK], uint8_t o_key[2 * N_BLOCK] ) |
| ubhat | 0:42863a11464a | 897 | { |
| ubhat | 0:42863a11464a | 898 | uint8_t s1[N_BLOCK], r, rc = 0x80; |
| ubhat | 0:42863a11464a | 899 | |
| ubhat | 0:42863a11464a | 900 | if(o_key != key) |
| ubhat | 0:42863a11464a | 901 | { |
| ubhat | 0:42863a11464a | 902 | block_copy( o_key, key ); |
| ubhat | 0:42863a11464a | 903 | block_copy( o_key + 16, key + 16 ); |
| ubhat | 0:42863a11464a | 904 | } |
| ubhat | 0:42863a11464a | 905 | |
| ubhat | 0:42863a11464a | 906 | copy_and_key( s1, in, o_key ); |
| ubhat | 0:42863a11464a | 907 | inv_shift_sub_rows( s1 ); |
| ubhat | 0:42863a11464a | 908 | |
| ubhat | 0:42863a11464a | 909 | for( r = 14 ; --r ; ) |
| ubhat | 0:42863a11464a | 910 | #if defined( VERSION_1 ) |
| ubhat | 0:42863a11464a | 911 | { |
| ubhat | 0:42863a11464a | 912 | if( ( r & 1 ) ) |
| ubhat | 0:42863a11464a | 913 | { |
| ubhat | 0:42863a11464a | 914 | update_decrypt_key_256( o_key, &rc ); |
| ubhat | 0:42863a11464a | 915 | add_round_key( s1, o_key + 16 ); |
| ubhat | 0:42863a11464a | 916 | } |
| ubhat | 0:42863a11464a | 917 | else |
| ubhat | 0:42863a11464a | 918 | add_round_key( s1, o_key ); |
| ubhat | 0:42863a11464a | 919 | inv_mix_sub_columns( s1 ); |
| ubhat | 0:42863a11464a | 920 | } |
| ubhat | 0:42863a11464a | 921 | #else |
| ubhat | 0:42863a11464a | 922 | { uint8_t s2[N_BLOCK]; |
| ubhat | 0:42863a11464a | 923 | if( ( r & 1 ) ) |
| ubhat | 0:42863a11464a | 924 | { |
| ubhat | 0:42863a11464a | 925 | update_decrypt_key_256( o_key, &rc ); |
| ubhat | 0:42863a11464a | 926 | copy_and_key( s2, s1, o_key + 16 ); |
| ubhat | 0:42863a11464a | 927 | } |
| ubhat | 0:42863a11464a | 928 | else |
| ubhat | 0:42863a11464a | 929 | copy_and_key( s2, s1, o_key ); |
| ubhat | 0:42863a11464a | 930 | inv_mix_sub_columns( s1, s2 ); |
| ubhat | 0:42863a11464a | 931 | } |
| ubhat | 0:42863a11464a | 932 | #endif |
| ubhat | 0:42863a11464a | 933 | copy_and_key( out, s1, o_key ); |
| ubhat | 0:42863a11464a | 934 | } |
| ubhat | 0:42863a11464a | 935 | |
| ubhat | 0:42863a11464a | 936 | #endif |