add rotary
Dependencies: X_NUCLEO_IKS01A1 LoRaWAN-lib SX1272Lib mbed
Fork of Canada-SX1272-LoRaWAN-Bootcamp by
LoRaWAN-SX1272-Mbed-Shield
Overview
LoRaWAN-SX1272-Mbed-Shield application demo is a LoRaWAN Class-A device example project using LoRaWAN-lib and SX1272Lib libraries that send out sensors data.
Prerequisites
1. NUCLEO_L152RE board.
2. SX1272-mbed-shield board.
3. X-NUCLEO-IKS01A1.
4. Grove Red LED.
5. Grove Button.
6. Grove Rotary Angle Sensor.
7. mbed online compiler.
8. Tera Term.
Hardware Configuration
Application 8, 9, 11
1. Connect NUCLEO_L152RE with X-NUCLEO-IKS01A1.
2. On top of X-NUCLEO-IKS01A1, connect SX1272-mbed-shield.
Application 13
1. Connect NUCLEO_L152RE with SX1272-mbed-shield.
2. Connect Grove Red LED with DIO_D6 port on SX1272-mbed-shield.
3. Connect Grove Button with DIO_D8 port on SX1272-mbed-shield.
4. Connect Grove Rotary Angle Sensor with ANA_A1 port SX1272-mbed-shield.
Software Configuration
The end-device must be configured with the following parameters:
- Commissioning.h
- Activation Type: OTA or ABP
- OTA: #define OVER_THE_AIR_ACTIVATION 1
- Network Type: Public or Private
- Public: #define LORAWAN_PUBLIC_NETWORK true
- LORAWAN_DEVICE_EUI (8 Bytes) : Fist 3 Bytes is the Organizationally Unique Identifier (OUI) followed by 5 bytes of unique ID. If not defined by user, then the firmware automatically assigns one to the end-device. (For OTA)
- #define IEEE_OUI 0x00, 0x00, 0x00
- #define LORAWAN_DEVICE_EUI { IEEE_OUI, 0x00, 0x00, 0x00, 0x00, 0x00 }
- #define IEEE_OUI 0x00, 0x00, 0x00
- LORAWAN_APPLICATION_EUI (8 Bytes) (For OTA)
- #define LORAWAN_APPLICATION_EUI { 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00 }
- LORAWAN_APPLICATION_KEY (16 Bytes) (For OTA)
- #define LORAWAN_APPLICATION_KEY { 0x00, 0x11, 0x22, 0x33, 0x44, 0x55, 0x66, 0x77, 0x88, 0x99, 0xaa, 0xbb, 0xcc, 0xdd, 0xee, 0xff }
- #define LORAWAN_APPLICATION_KEY { 0x00, 0x11, 0x22, 0x33, 0x44, 0x55, 0x66, 0x77, 0x88, 0x99, 0xaa, 0xbb, 0xcc, 0xdd, 0xee, 0xff }
- LORAWAN_DEVICE_ADDRESS (For ABP)
- #define LORAWAN_DEVICE_ADDRESS ( uint32_t )0x0
- LORAWAN_NWKSKEY (For ABP)
- #define LORAWAN_NWKSKEY { 0x2B, 0x7E, 0x15, 0x16, 0x28, 0xAE, 0xD2, 0xA6, 0xAB, 0xF7, 0x15, 0x88, 0x09, 0xCF, 0x4F, 0x3C }
- LORAWAN_APPSKEY (For ABP)
- #define LORAWAN_APPSKEY { 0x2B, 0x7E, 0x15, 0x16, 0x28, 0xAE, 0xD2, 0xA6, 0xAB, 0xF7, 0x15, 0x88, 0x09, 0xCF, 0x4F, 0x3C }
- Activation Type: OTA or ABP
- Configure.h
- Communication Type: Hybrid or FHSS
- Hybrid: #define USE_BAND_915_HYBRID
- Join request Period:
- 5 sec: #define OVER_THE_AIR_ACTIVATION_DUTYCYCLE 5000000 value in us
- TX Period:
- 5 sec: #define APP_TX_DUTYCYCLE 5000000 value in us
- Uplink message: Confirmed or Unconfirmed
- Confirmed: #define LORAWAN_CONFIRMED_MSG_ON 1
- ADR(Adaptive Data Rate): ON or OFF
- OFF: #define LORAWAN_ADR_ON 0
- Default data rate: DR_0 or DR_1 or DR_2 or DR_3 or DR_4
- DR_0: #define LORAWAN_DEFAULT_DATARATE DR_0
- Application Type: 8 (IKS01A1) or 9 (IKS01A1+Cayenne) or 11 (Push Button) or 13 (rotary+Cayenne)
- 9: #define LORAWAN_APP_PORT 9
- Tx Power: 10 to 30
- 20 dBm: #define LORAWAN_TX_POWER TX_POWER_20_DBM
- Communication Type: Hybrid or FHSS
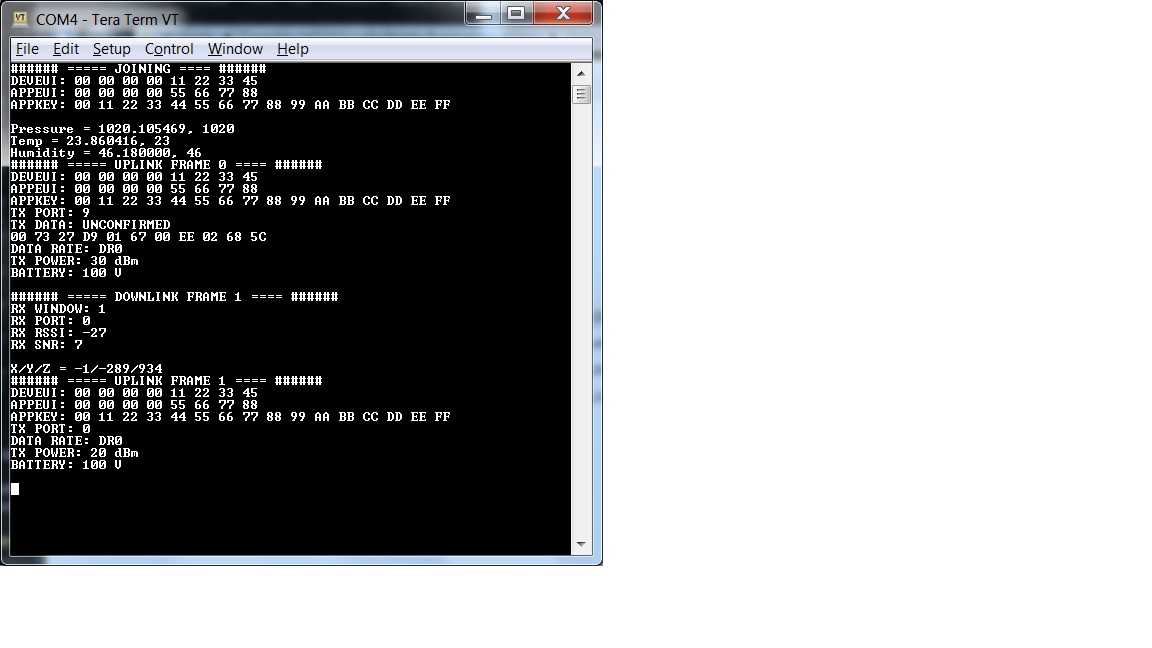
Serial Terminal Display
- Use Tera Term to see the sending message (baud rate: 115200):
- button = 0 (if not press) button = 1 (if pressed)
- rotary = 0 ~ 300
- button = 0 (if not press) button = 1 (if pressed)
system/crypto/cmac.cpp
- Committer:
- terence304
- Date:
- 2018-02-10
- Revision:
- 17:a822234a2299
- Parent:
- 0:6cc76d70e2a1
File content as of revision 17:a822234a2299:
/**************************************************************************
Copyright (C) 2009 Lander Casado, Philippas Tsigas
All rights reserved.
Permission is hereby granted, free of charge, to any person obtaining
a copy of this software and associated documentation files
(the "Software"), to deal with the Software without restriction, including
without limitation the rights to use, copy, modify, merge, publish,
distribute, sublicense, and/or sell copies of the Software, and to
permit persons to whom the Software is furnished to do so, subject to
the following conditions:
Redistributions of source code must retain the above copyright notice,
this list of conditions and the following disclaimers. Redistributions in
binary form must reproduce the above copyright notice, this list of
conditions and the following disclaimers in the documentation and/or
other materials provided with the distribution.
In no event shall the authors or copyright holders be liable for any special,
incidental, indirect or consequential damages of any kind, or any damages
whatsoever resulting from loss of use, data or profits, whether or not
advised of the possibility of damage, and on any theory of liability,
arising out of or in connection with the use or performance of this software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS
OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY,
FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE
CONTRIBUTORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER
LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING
FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER
DEALINGS WITH THE SOFTWARE
*****************************************************************************/
//#include <sys/param.h>
//#include <sys/systm.h>
#include <stdint.h>
#include "aes.h"
#include "cmac.h"
#include "utilities.h"
#define LSHIFT(v, r) do { \
int32_t i; \
for (i = 0; i < 15; i++) \
(r)[i] = (v)[i] << 1 | (v)[i + 1] >> 7; \
(r)[15] = (v)[15] << 1; \
} while (0)
#define XOR(v, r) do { \
int32_t i; \
for (i = 0; i < 16; i++) \
{ \
(r)[i] = (r)[i] ^ (v)[i]; \
} \
} while (0) \
void AES_CMAC_Init(AES_CMAC_CTX *ctx)
{
memset1(ctx->X, 0, sizeof ctx->X);
ctx->M_n = 0;
memset1(ctx->rijndael.ksch, '\0', 240);
}
void AES_CMAC_SetKey(AES_CMAC_CTX *ctx, const uint8_t key[AES_CMAC_KEY_LENGTH])
{
//rijndael_set_key_enc_only(&ctx->rijndael, key, 128);
aes_set_key( key, AES_CMAC_KEY_LENGTH, &ctx->rijndael);
}
void AES_CMAC_Update(AES_CMAC_CTX *ctx, const uint8_t *data, uint32_t len)
{
uint32_t mlen;
uint8_t in[16];
if (ctx->M_n > 0) {
mlen = MIN(16 - ctx->M_n, len);
memcpy1(ctx->M_last + ctx->M_n, data, mlen);
ctx->M_n += mlen;
if (ctx->M_n < 16 || len == mlen)
return;
XOR(ctx->M_last, ctx->X);
//rijndael_encrypt(&ctx->rijndael, ctx->X, ctx->X);
aes_encrypt( ctx->X, ctx->X, &ctx->rijndael);
data += mlen;
len -= mlen;
}
while (len > 16) { /* not last block */
XOR(data, ctx->X);
//rijndael_encrypt(&ctx->rijndael, ctx->X, ctx->X);
memcpy1(in, &ctx->X[0], 16); //Bestela ez du ondo iten
aes_encrypt( in, in, &ctx->rijndael);
memcpy1(&ctx->X[0], in, 16);
data += 16;
len -= 16;
}
/* potential last block, save it */
memcpy1(ctx->M_last, data, len);
ctx->M_n = len;
}
void AES_CMAC_Final(uint8_t digest[AES_CMAC_DIGEST_LENGTH], AES_CMAC_CTX *ctx)
{
uint8_t K[16];
uint8_t in[16];
/* generate subkey K1 */
memset1(K, '\0', 16);
//rijndael_encrypt(&ctx->rijndael, K, K);
aes_encrypt( K, K, &ctx->rijndael);
if (K[0] & 0x80) {
LSHIFT(K, K);
K[15] ^= 0x87;
} else
LSHIFT(K, K);
if (ctx->M_n == 16) {
/* last block was a complete block */
XOR(K, ctx->M_last);
} else {
/* generate subkey K2 */
if (K[0] & 0x80) {
LSHIFT(K, K);
K[15] ^= 0x87;
} else
LSHIFT(K, K);
/* padding(M_last) */
ctx->M_last[ctx->M_n] = 0x80;
while (++ctx->M_n < 16)
ctx->M_last[ctx->M_n] = 0;
XOR(K, ctx->M_last);
}
XOR(ctx->M_last, ctx->X);
//rijndael_encrypt(&ctx->rijndael, ctx->X, digest);
memcpy1(in, &ctx->X[0], 16); //Bestela ez du ondo iten
aes_encrypt(in, digest, &ctx->rijndael);
memset1(K, 0, sizeof K);
}
