Debug BLE application with nRF Sniffer
1. Introduction
The nRF Bluetooth® Smart Sniffer is a tool for debugging Bluetooth low energy (BLE) applications. The sniffer can pick up (sniff) every packet between a selected peripheral and the central device it is communicating with, even when the link is encrypted. When developing a BLE solution, knowing what happens over-the-air between devices can help you isolate, debug and troubleshoot any potential issues.
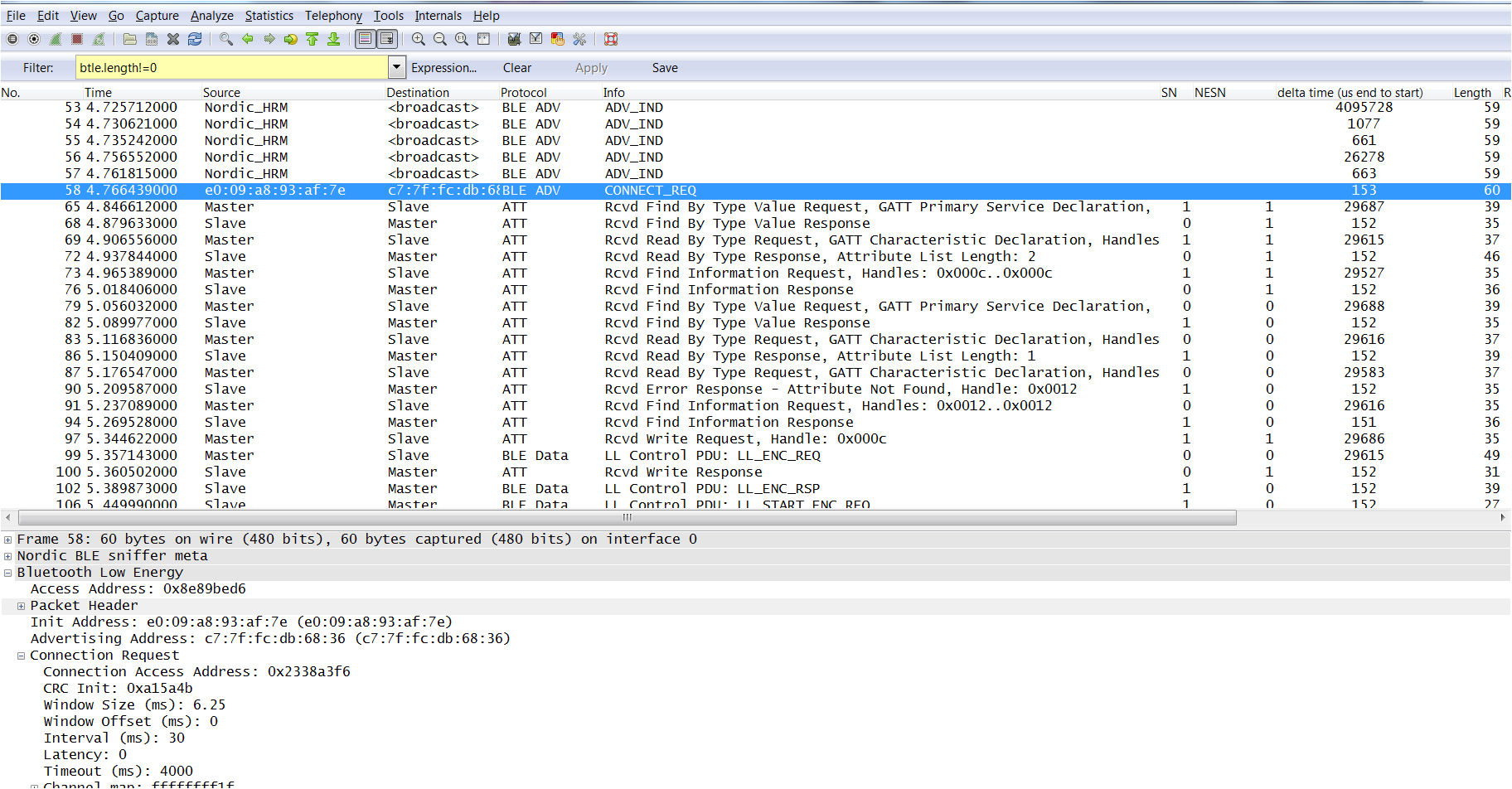
nRFSniffer trace on Wireshark showing a advertising packets, and the connection established by an iPhone.
2. What you need to get started
Hardware
- An PCA10000 dongle or a nRF51 Evaluation board
- A PC computer running Windows 7 or later
How to set up the hardware
- Connect the hardware to a USB port.
- Place the hardware (PCA10000) close to the Peripheral and Central device.
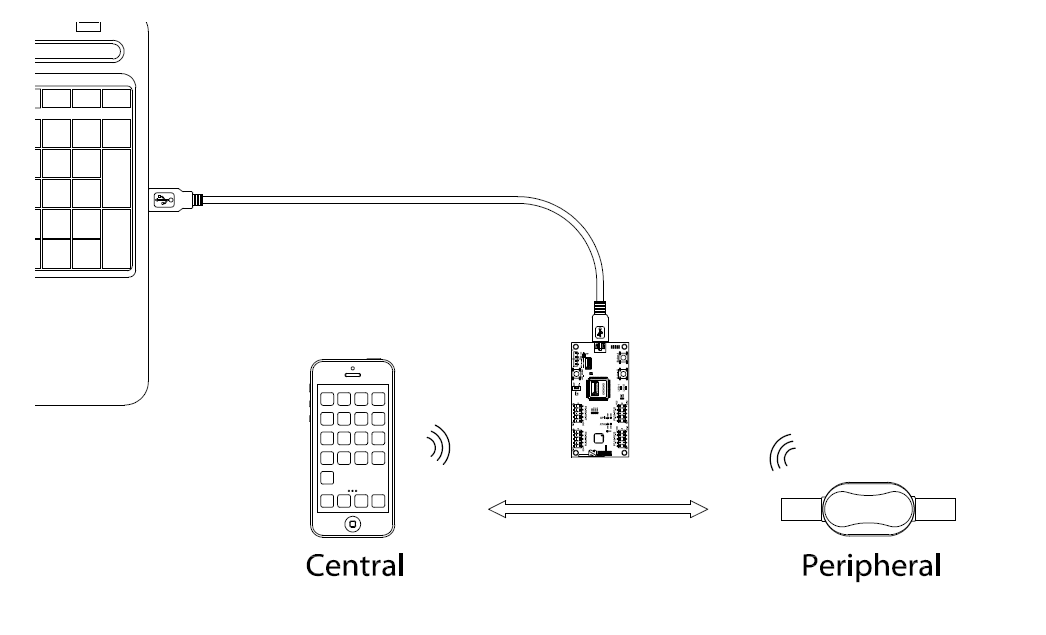 Hardware setup, if you don’t have the USB extension cable, you can just plug the PCA10000 dongle directly into the USB port, make sure the PCA10000 is in the range of no more than 50 cm to the peripheral and the central.
Hardware setup, if you don’t have the USB extension cable, you can just plug the PCA10000 dongle directly into the USB port, make sure the PCA10000 is in the range of no more than 50 cm to the peripheral and the central.
Software
Download and unzip the following materials:
- nRF tools from www.nordicsemi.com. Download here: /media/uploads/nemovn/nrftools_6_0_0_installer.exe
- ble-sniffer_win_1.0.1_1111_Sniffer.exe found in ble-sniffer_<os>_<version>_Sniffer.zip. Download here: /media/uploads/nemovn/ble-sniffer_win_1.0.1.zip
- Wireshark from wireshark.org. Download 64-bit version here: /media/uploads/nemovn/wireshark-win64-1.10.9.exe . Download 32-bit version here: /media/uploads/nemovn/wireshark-win32-1.10.9.exe
Wireshark v1.10 is recommended. The latest Wireshark version, v1.12, may not be fully compatible with the current sniffer software.
3. Flashing the sniffer firmware
- Run ble-sniffer_win_1.0.1_1111_Sniffer.exe from the unziped nRF Sniffer folder.
- nRF Sniffer console interface will appear and search for the sniffer COM Port.
- Press Ctrl+R to start programming
- If you have more than 1 Segger Jlink device you may need to select the correct PCA10000’s SEGGER serial number
- If the sniffer firmware has been installed properly, you should see this interface:
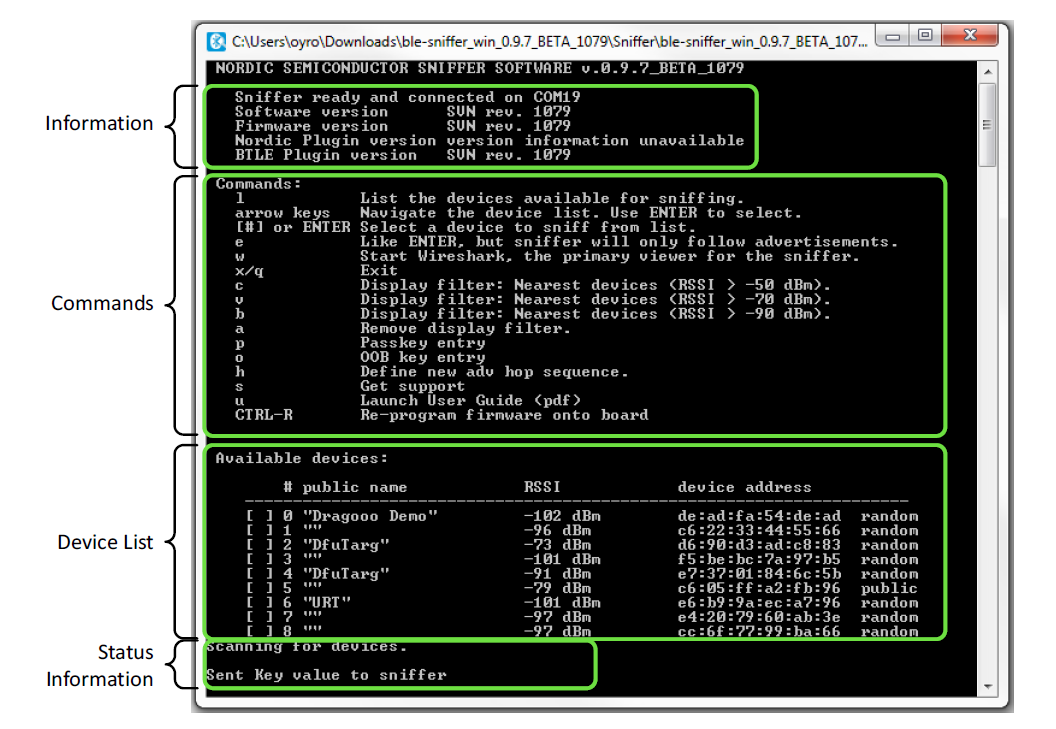 nRFSniffer console showing devices that advertising in the range of the nRF Sniffer
nRFSniffer console showing devices that advertising in the range of the nRF Sniffer
4. Using the sniffer
Once you have the Sniffer console running, the software should automatically find the hardware COM port (you only have to flash the firmware once) and start reporting advertisements and listing nearby devices. If things aren't working as they should, reset the hardware (unplug-wait 5seconds – plugin again) and refresh the device list by typing L or restart the Sniffer program.
Note: If the sniffer console keep searching the COM port when you already pluged the PCA10000 dongle in and already flashed the firmware, you can try to unplug and plug the hardware back again after 5 seconds.
The Sniffer may not manage to pick up all connect requests and will not always pick up on a connection. In such cases, you need to reconnect.
If the sniffer works properly, you can start tracking a connection and debugging by first start with listing the adverting devices by pressing L. Then select the peripheral you want to track by pressing the index number or use up and down arrow buttons and press enter to select. After that you can start wireshark to display the captured packages by pressing “W” and you are ready for shooting trouble.
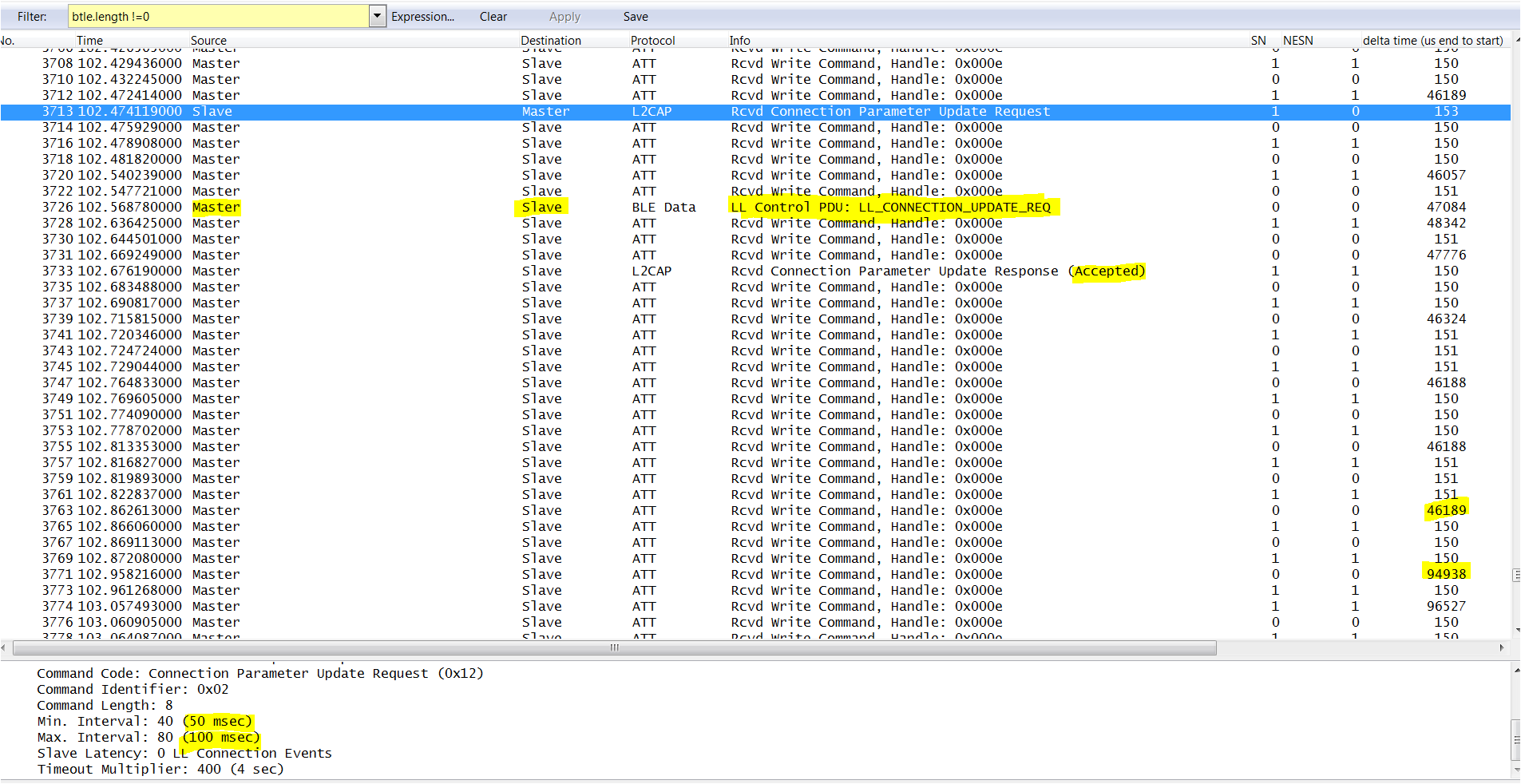
For more detail on how to use wireshark and analyze the BTLE packets please have a look at chapter 4 in the nRFSniffer user guide included in the zip folder or download here: /media/uploads/nemovn/ble-sniffer_win_1.2_user_guide.pdf
Note: One very useful filter you should try is btle.length!=0 to filter out all empty packet and make it easier to spot meaningful information.
Please log in to post comments.
