【これは旧バージョンです】 AndroidのBLEラジコンプロポアプリ「BLEPropo」と接続し、RCサーボとDCモータを制御するプログラムです。 mbed HRM1017で動作を確認しています。 BLEPropo → https://github.com/lipoyang/BLEPropo
Fork of BLE_RCBController2 by
BLEを使ったAndroid用ラジコンプロポアプリ「BLEPropo」に対応するmbed HRM1017用ファームウェアです。
BLEPropoは、GitHubにて公開中。
https://github.com/lipoyang/BLEPropo

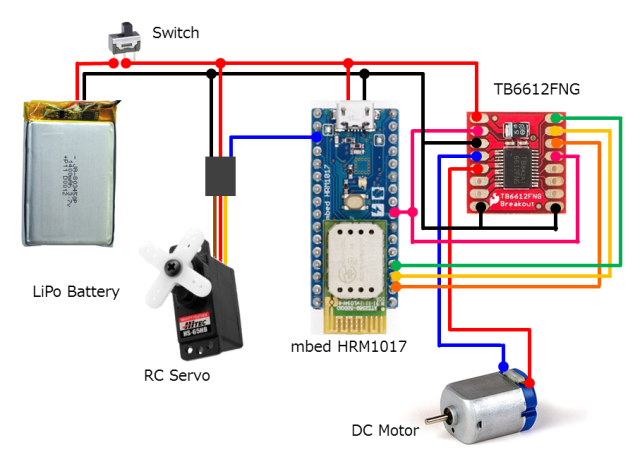
ラジコンは、mbed HRM1017とRCサーボやDCモータを組み合わせて作ります。
HRM1017/common/binary.h@4:ebda47d22091, 2014-08-20 (annotated)
- Committer:
- jksoft
- Date:
- Wed Aug 20 13:41:01 2014 +0000
- Revision:
- 4:ebda47d22091
- Parent:
- nRF51822/common/binary.h@1:48f6e08a3ac2
?????????
Who changed what in which revision?
| User | Revision | Line number | New contents of line |
|---|---|---|---|
| jksoft | 0:8c643bfe55b7 | 1 | /**************************************************************************/ |
| jksoft | 0:8c643bfe55b7 | 2 | /*! |
| jksoft | 0:8c643bfe55b7 | 3 | @file binary.h |
| jksoft | 0:8c643bfe55b7 | 4 | @author hathach (tinyusb.org) |
| jksoft | 0:8c643bfe55b7 | 5 | |
| jksoft | 0:8c643bfe55b7 | 6 | @section LICENSE |
| jksoft | 0:8c643bfe55b7 | 7 | |
| jksoft | 0:8c643bfe55b7 | 8 | Software License Agreement (BSD License) |
| jksoft | 0:8c643bfe55b7 | 9 | |
| jksoft | 0:8c643bfe55b7 | 10 | Copyright (c) 2013, K. Townsend (microBuilder.eu) |
| jksoft | 0:8c643bfe55b7 | 11 | All rights reserved. |
| jksoft | 0:8c643bfe55b7 | 12 | |
| jksoft | 0:8c643bfe55b7 | 13 | Redistribution and use in source and binary forms, with or without |
| jksoft | 0:8c643bfe55b7 | 14 | modification, are permitted provided that the following conditions are met: |
| jksoft | 0:8c643bfe55b7 | 15 | 1. Redistributions of source code must retain the above copyright |
| jksoft | 0:8c643bfe55b7 | 16 | notice, this list of conditions and the following disclaimer. |
| jksoft | 0:8c643bfe55b7 | 17 | 2. Redistributions in binary form must reproduce the above copyright |
| jksoft | 0:8c643bfe55b7 | 18 | notice, this list of conditions and the following disclaimer in the |
| jksoft | 0:8c643bfe55b7 | 19 | documentation and/or other materials provided with the distribution. |
| jksoft | 0:8c643bfe55b7 | 20 | 3. Neither the name of the copyright holders nor the |
| jksoft | 0:8c643bfe55b7 | 21 | names of its contributors may be used to endorse or promote products |
| jksoft | 0:8c643bfe55b7 | 22 | derived from this software without specific prior written permission. |
| jksoft | 0:8c643bfe55b7 | 23 | |
| jksoft | 0:8c643bfe55b7 | 24 | THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS ''AS IS'' AND ANY |
| jksoft | 0:8c643bfe55b7 | 25 | EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED |
| jksoft | 0:8c643bfe55b7 | 26 | WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE ARE |
| jksoft | 0:8c643bfe55b7 | 27 | DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER BE LIABLE FOR ANY |
| jksoft | 0:8c643bfe55b7 | 28 | DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES |
| jksoft | 0:8c643bfe55b7 | 29 | INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; |
| jksoft | 0:8c643bfe55b7 | 30 | LOSS OF USE, DATA, OR PROFITS; OR BUSINESS INTERRUPTION HOWEVER CAUSED AND |
| jksoft | 0:8c643bfe55b7 | 31 | ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT |
| jksoft | 0:8c643bfe55b7 | 32 | INCLUDING NEGLIGENCE OR OTHERWISE ARISING IN ANY WAY OUT OF THE USE OF THIS |
| jksoft | 0:8c643bfe55b7 | 33 | SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. |
| jksoft | 0:8c643bfe55b7 | 34 | */ |
| jksoft | 0:8c643bfe55b7 | 35 | /**************************************************************************/ |
| jksoft | 0:8c643bfe55b7 | 36 | |
| jksoft | 0:8c643bfe55b7 | 37 | /** \ingroup TBD |
| jksoft | 0:8c643bfe55b7 | 38 | * \defgroup TBD |
| jksoft | 0:8c643bfe55b7 | 39 | * \brief TBD |
| jksoft | 0:8c643bfe55b7 | 40 | * |
| jksoft | 0:8c643bfe55b7 | 41 | * @{ |
| jksoft | 0:8c643bfe55b7 | 42 | */ |
| jksoft | 0:8c643bfe55b7 | 43 | |
| jksoft | 0:8c643bfe55b7 | 44 | #ifndef _BINARY_H_ |
| jksoft | 0:8c643bfe55b7 | 45 | #define _BINARY_H_ |
| jksoft | 0:8c643bfe55b7 | 46 | |
| jksoft | 0:8c643bfe55b7 | 47 | #ifdef __cplusplus |
| jksoft | 0:8c643bfe55b7 | 48 | extern "C" { |
| jksoft | 0:8c643bfe55b7 | 49 | #endif |
| jksoft | 0:8c643bfe55b7 | 50 | |
| jksoft | 0:8c643bfe55b7 | 51 | /// n-th Bit |
| jksoft | 0:8c643bfe55b7 | 52 | #define BIT(n) (1 << (n)) |
| jksoft | 0:8c643bfe55b7 | 53 | |
| jksoft | 0:8c643bfe55b7 | 54 | /// set n-th bit of x to 1 |
| jksoft | 0:8c643bfe55b7 | 55 | #define BIT_SET(x, n) ( (x) | BIT(n) ) |
| jksoft | 0:8c643bfe55b7 | 56 | |
| jksoft | 0:8c643bfe55b7 | 57 | /// clear n-th bit of x |
| jksoft | 0:8c643bfe55b7 | 58 | #define BIT_CLR(x, n) ( (x) & (~BIT(n)) ) |
| jksoft | 0:8c643bfe55b7 | 59 | |
| jksoft | 0:8c643bfe55b7 | 60 | /// test n-th bit of x |
| jksoft | 0:8c643bfe55b7 | 61 | #define BIT_TEST(x, n) ( (x) & BIT(n) ) |
| jksoft | 0:8c643bfe55b7 | 62 | |
| jksoft | 0:8c643bfe55b7 | 63 | #if defined(__GNUC__) && !defined(__CC_ARM) // keil does not support binary format |
| jksoft | 0:8c643bfe55b7 | 64 | |
| jksoft | 0:8c643bfe55b7 | 65 | #define BIN8(x) ((uint8_t) (0b##x)) |
| jksoft | 0:8c643bfe55b7 | 66 | #define BIN16(b1, b2) ((uint16_t) (0b##b1##b2)) |
| jksoft | 0:8c643bfe55b7 | 67 | #define BIN32(b1, b2, b3, b4) ((uint32_t) (0b##b1##b2##b3##b4)) |
| jksoft | 0:8c643bfe55b7 | 68 | |
| jksoft | 0:8c643bfe55b7 | 69 | #else |
| jksoft | 0:8c643bfe55b7 | 70 | |
| jksoft | 0:8c643bfe55b7 | 71 | // internal macro of B8, B16, B32 |
| jksoft | 0:8c643bfe55b7 | 72 | #define _B8__(x) (((x&0x0000000FUL)?1:0) \ |
| jksoft | 0:8c643bfe55b7 | 73 | +((x&0x000000F0UL)?2:0) \ |
| jksoft | 0:8c643bfe55b7 | 74 | +((x&0x00000F00UL)?4:0) \ |
| jksoft | 0:8c643bfe55b7 | 75 | +((x&0x0000F000UL)?8:0) \ |
| jksoft | 0:8c643bfe55b7 | 76 | +((x&0x000F0000UL)?16:0) \ |
| jksoft | 0:8c643bfe55b7 | 77 | +((x&0x00F00000UL)?32:0) \ |
| jksoft | 0:8c643bfe55b7 | 78 | +((x&0x0F000000UL)?64:0) \ |
| jksoft | 0:8c643bfe55b7 | 79 | +((x&0xF0000000UL)?128:0)) |
| jksoft | 0:8c643bfe55b7 | 80 | |
| jksoft | 0:8c643bfe55b7 | 81 | #define BIN8(d) ((uint8_t) _B8__(0x##d##UL)) |
| jksoft | 0:8c643bfe55b7 | 82 | #define BIN16(dmsb,dlsb) (((uint16_t)BIN8(dmsb)<<8) + BIN8(dlsb)) |
| jksoft | 0:8c643bfe55b7 | 83 | #define BIN32(dmsb,db2,db3,dlsb) \ |
| jksoft | 0:8c643bfe55b7 | 84 | (((uint32_t)BIN8(dmsb)<<24) \ |
| jksoft | 0:8c643bfe55b7 | 85 | + ((uint32_t)BIN8(db2)<<16) \ |
| jksoft | 0:8c643bfe55b7 | 86 | + ((uint32_t)BIN8(db3)<<8) \ |
| jksoft | 0:8c643bfe55b7 | 87 | + BIN8(dlsb)) |
| jksoft | 0:8c643bfe55b7 | 88 | #endif |
| jksoft | 0:8c643bfe55b7 | 89 | |
| jksoft | 0:8c643bfe55b7 | 90 | #ifdef __cplusplus |
| jksoft | 0:8c643bfe55b7 | 91 | } |
| jksoft | 0:8c643bfe55b7 | 92 | #endif |
| jksoft | 0:8c643bfe55b7 | 93 | |
| jksoft | 0:8c643bfe55b7 | 94 | #endif /* _BINARY_H_ */ |
| jksoft | 0:8c643bfe55b7 | 95 | |
| jksoft | 0:8c643bfe55b7 | 96 | /** @} */ |
 Bizan Nishimura
Bizan Nishimura
