Demonstration of Class-A LoRaWAN device using NAMote-72
Dependencies: LoRaWAN-lib mbed lib_mpl3115a2 lib_mma8451q lib_gps SX1272Lib
Dependents: LoRaWAN-NAMote72-BVS-confirmed-tester-0-7v1_copy
LoRaWAN-NAMote72 Application Demo is a Class-A device example project using LoRaWAN-lib and SX1272Lib libraries.
This project is compliant with LoRaWAN V1.0.1 specification.
Comissioning.h (LoRaWAN Network Configuration)
The end-device can be activated in one of the two ways:
Over the Air (OTA) activation can be enabled as shown in the figure below.
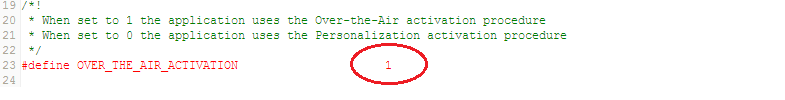
The end-device must be configured with the following parameters:
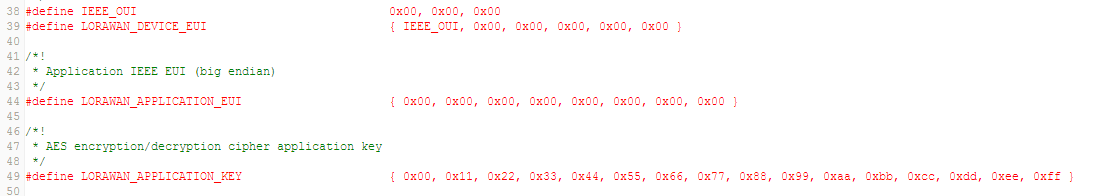
LORAWAN_DEVICE_EUI(8 Bytes) : Fist 3 Bytes is the Organizationally Unique Identifier (OUI) followed by 5 bytes of unique ID. If not defined by user, then the firmware automatically assigns one to the end-deviceLORAWAN_APPLICATION_EUI(8 Bytes)LORAWAN_APPLICATION_KEY(or DEVKEY) (16 Bytes)
Activation by Personalization (ABP) can be enabled as shown in the figure below.
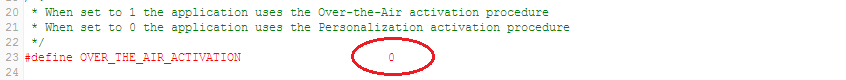
The end-device must be configured with the following parameters:
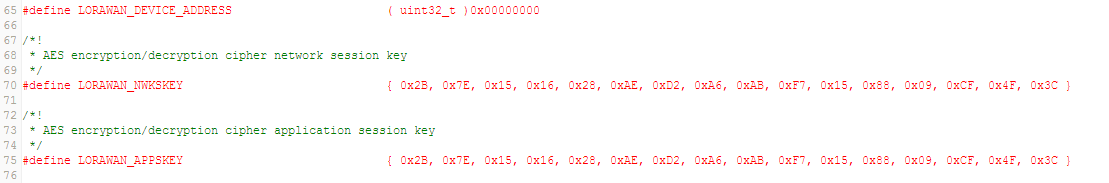
LORAWAN_DEVICE_ADDRESS(4 Bytes) : If not defined by user, then the firmware automatically assigns one to the end-deviceLORAWAN_NWKSKEY(16 Bytes)LORAWAN_APPSKEY(16 Bytes)
Config.h (LoRaWAN Communication Parameters)
- Mode of Operation : Hybrid
If the end-device needs to be configured to operate over 8-channels, then
Hybrid Modeneeds to be enabled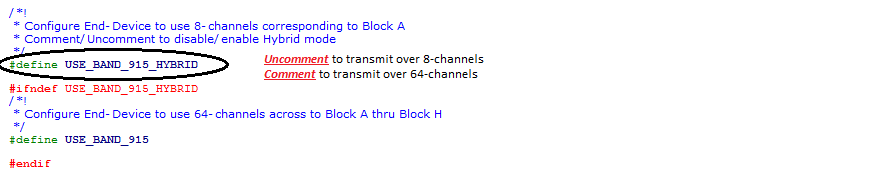
- Mode of Operation : Frequency Hop
If the end-device needs to be configured to operate over 64-channels, then
Hybrid Modeneeds to be disabled
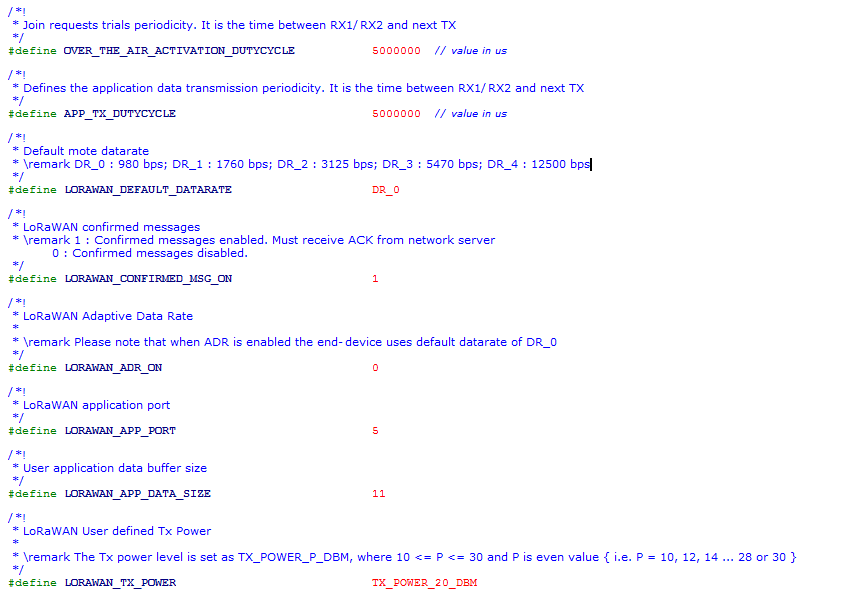
- Delay between successive JOIN REQUESTs :
The delay between successive Join Requests (until the end-device joins the network) can be configured using the parameter
OVER_THE_AIR_ACTIVATION_DUTYCYCLE
- Inter-Frame Delay :
One can change the delay between each frame transmission using
APP_TX_DUTYCYCLEIt is advisable thatAPP_TX_DUTYCYCLEis greater than or equal to 3sec.
- Data Rate :
The data rate can be configured as per LoRaWAN specification using the paramter
LORAWAN_DEFAULT_DATARATE. The range of values are DR_0, DR_1, DR_2, DR_3 and DR_4
- Confirmed/Unconfirmed Messages :
The uplink message or payload can be chosen to be confirmed or unconfirmed using the parameter
LORAWAN_CONFIRMED_MSG_ON. When set to 1, the transmitted messages need to be confirmed with anACKby the network server in the subsequent RX window. When set to 0, noACKis requested.
- ADR ON/OFF :
The ADR can be enabled or disabled using the parameter
LORAWAN_ADR_ON. When set to 1, ADR is enabled and disabled when set to 0.
- Application Port :
The application port can be set using parameter
LORAWAN_APP_PORT.
- Payload Length :
The lenght of the payload (in bytes) to be transmitted can be configured using
LORAWAN_APP_DATA_SIZE
- Transmit Power :
The transmit power can be configured using
LORAWAN_TX_POWER(LoRaMAC verifies if the set power is compliant with the LoRaWAN spec and FCC guidelines)
Main.cpp (Device State Machine)
The end-device state machine is defined.
- Initial State : Device is initialized.
- Join State : For OTA, Join Request is transmitted to the network until Join Accept is received by the end-device. Join event function is called that sets Red LED ON.
- Send State : Transmit payload frame is prepared. Tx event is called that blinks the Red LED indicating uplink transmission.
- Cycle State : Next packet transmission is scheduled
LoRaEventProc.cpp (Events and On-board Application)
Define events during Join, Tx & Rx. Prepare TX packet by appending with appropriate application data.
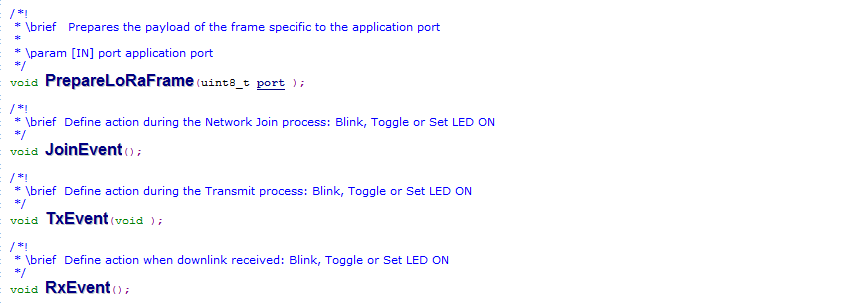
- PrepareLoRaFrame(uint8_t port ) :
Prepare LoRa payload frame with on-board application data such as GPS, Temperature, Battery, etc. LoRa.ApplicationCall(AppType ) calls application AppType defined in
LoRaApp.cpp. AppType is defined inLoRaApp.h
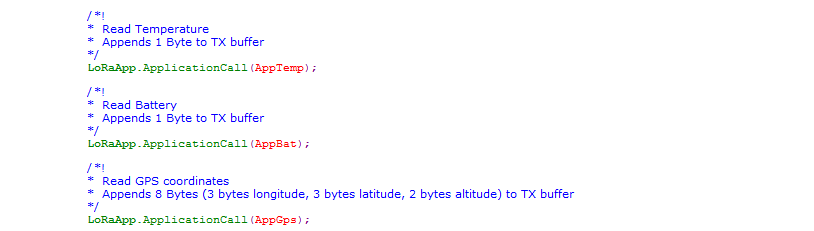
LoRaApp.cpp
User-defined applications such as GPS, Temp, Accelerometer, LED indications etc. Event based actions such as LED blink on Tx, LED toggle on downlink etc
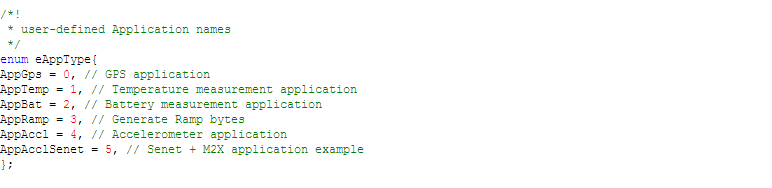
LoRaDeviceStateProc.cpp
Process function calls corresponding to different Device states
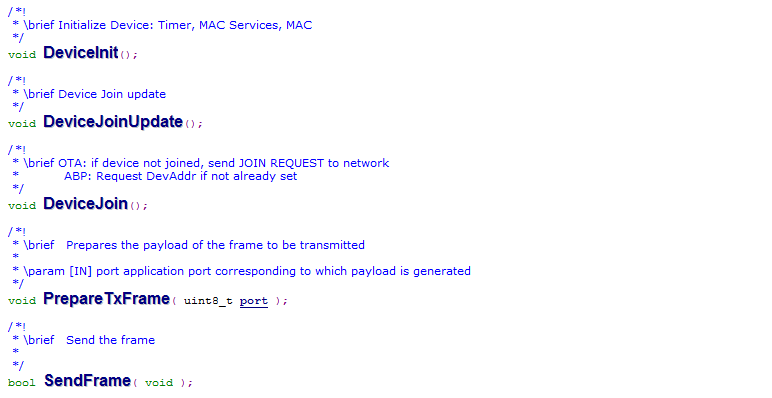
LoRaMacLayerService.cpp
Define MAC Layer Services: MLME & MCPS
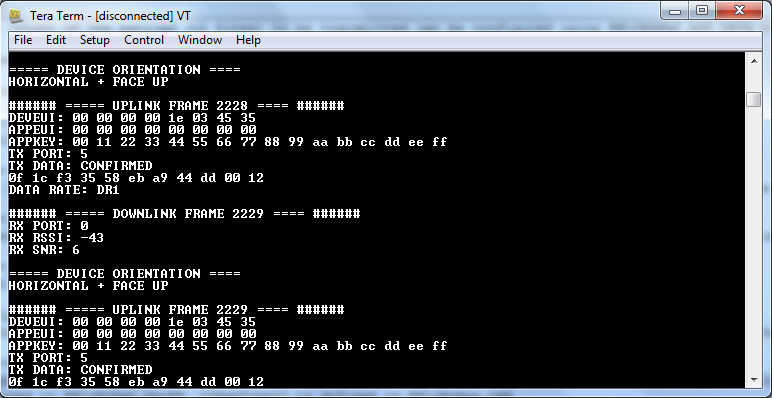
Serial Terminal Display
By using a serial port connection using applications such as teraterm or putty, one can view the status of the End-Device. Once the End-Device Joins the network, transmission parameters such as payload data, application port, message type etc. are displayed on the terminal.
Default Application Payload
This application defaults to sending uplink data to logical port 5. The application payload consists of:
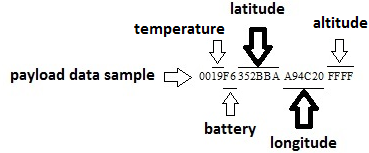
Sample Application Payload Calculation for Longitude/Latitude
Payload => 00 19 F6 352BBA A94C20 FFFF
Temperature Calculation
19H => 2510
Temp = 25/2 = 12.5 oC
Battery Level
FFH => 100 %
F6H => 96.5 %
Longitude Calculation
longitude = A94C20H => 1109507210
longitudinal coordinate = -360 + (longitude10 x 180/(223))
longitudinal coordinate = -121.93
Latitude Calculation
latitude = 352BBAH = 348460210
latitude coordinate = (latitude10 x 90/(223-1))
latitude coordinate = 37.39
system/crypto/aes.cpp@19:678f15b08d8a, 2020-01-28 (annotated)
- Committer:
- nlam
- Date:
- Tue Jan 28 19:10:15 2020 +0000
- Revision:
- 19:678f15b08d8a
- Parent:
- 2:d119a85c793c
Updated to the Mbed latest libraries and resolved build error, uncommented debug.h.
Who changed what in which revision?
| User | Revision | Line number | New contents of line |
|---|---|---|---|
| ubhat | 2:d119a85c793c | 1 | /* |
| ubhat | 2:d119a85c793c | 2 | --------------------------------------------------------------------------- |
| ubhat | 2:d119a85c793c | 3 | Copyright (c) 1998-2008, Brian Gladman, Worcester, UK. All rights reserved. |
| ubhat | 2:d119a85c793c | 4 | |
| ubhat | 2:d119a85c793c | 5 | LICENSE TERMS |
| ubhat | 2:d119a85c793c | 6 | |
| ubhat | 2:d119a85c793c | 7 | The redistribution and use of this software (with or without changes) |
| ubhat | 2:d119a85c793c | 8 | is allowed without the payment of fees or royalties provided that: |
| ubhat | 2:d119a85c793c | 9 | |
| ubhat | 2:d119a85c793c | 10 | 1. source code distributions include the above copyright notice, this |
| ubhat | 2:d119a85c793c | 11 | list of conditions and the following disclaimer; |
| ubhat | 2:d119a85c793c | 12 | |
| ubhat | 2:d119a85c793c | 13 | 2. binary distributions include the above copyright notice, this list |
| ubhat | 2:d119a85c793c | 14 | of conditions and the following disclaimer in their documentation; |
| ubhat | 2:d119a85c793c | 15 | |
| ubhat | 2:d119a85c793c | 16 | 3. the name of the copyright holder is not used to endorse products |
| ubhat | 2:d119a85c793c | 17 | built using this software without specific written permission. |
| ubhat | 2:d119a85c793c | 18 | |
| ubhat | 2:d119a85c793c | 19 | DISCLAIMER |
| ubhat | 2:d119a85c793c | 20 | |
| ubhat | 2:d119a85c793c | 21 | This software is provided 'as is' with no explicit or implied warranties |
| ubhat | 2:d119a85c793c | 22 | in respect of its properties, including, but not limited to, correctness |
| ubhat | 2:d119a85c793c | 23 | and/or fitness for purpose. |
| ubhat | 2:d119a85c793c | 24 | --------------------------------------------------------------------------- |
| ubhat | 2:d119a85c793c | 25 | Issue 09/09/2006 |
| ubhat | 2:d119a85c793c | 26 | |
| ubhat | 2:d119a85c793c | 27 | This is an AES implementation that uses only 8-bit byte operations on the |
| ubhat | 2:d119a85c793c | 28 | cipher state (there are options to use 32-bit types if available). |
| ubhat | 2:d119a85c793c | 29 | |
| ubhat | 2:d119a85c793c | 30 | The combination of mix columns and byte substitution used here is based on |
| ubhat | 2:d119a85c793c | 31 | that developed by Karl Malbrain. His contribution is acknowledged. |
| ubhat | 2:d119a85c793c | 32 | */ |
| ubhat | 2:d119a85c793c | 33 | |
| ubhat | 2:d119a85c793c | 34 | /* define if you have a fast memcpy function on your system */ |
| ubhat | 2:d119a85c793c | 35 | #if 0 |
| ubhat | 2:d119a85c793c | 36 | # define HAVE_MEMCPY |
| ubhat | 2:d119a85c793c | 37 | # include <string.h> |
| ubhat | 2:d119a85c793c | 38 | # if defined( _MSC_VER ) |
| ubhat | 2:d119a85c793c | 39 | # include <intrin.h> |
| ubhat | 2:d119a85c793c | 40 | # pragma intrinsic( memcpy ) |
| ubhat | 2:d119a85c793c | 41 | # endif |
| ubhat | 2:d119a85c793c | 42 | #endif |
| ubhat | 2:d119a85c793c | 43 | |
| ubhat | 2:d119a85c793c | 44 | |
| ubhat | 2:d119a85c793c | 45 | #include <stdlib.h> |
| ubhat | 2:d119a85c793c | 46 | #include <stdint.h> |
| ubhat | 2:d119a85c793c | 47 | |
| ubhat | 2:d119a85c793c | 48 | /* define if you have fast 32-bit types on your system */ |
| ubhat | 2:d119a85c793c | 49 | #if ( __CORTEX_M != 0 ) // if Cortex is different from M0/M0+ |
| ubhat | 2:d119a85c793c | 50 | # define HAVE_UINT_32T |
| ubhat | 2:d119a85c793c | 51 | #endif |
| ubhat | 2:d119a85c793c | 52 | |
| ubhat | 2:d119a85c793c | 53 | /* define if you don't want any tables */ |
| ubhat | 2:d119a85c793c | 54 | #if 1 |
| ubhat | 2:d119a85c793c | 55 | # define USE_TABLES |
| ubhat | 2:d119a85c793c | 56 | #endif |
| ubhat | 2:d119a85c793c | 57 | |
| ubhat | 2:d119a85c793c | 58 | /* On Intel Core 2 duo VERSION_1 is faster */ |
| ubhat | 2:d119a85c793c | 59 | |
| ubhat | 2:d119a85c793c | 60 | /* alternative versions (test for performance on your system) */ |
| ubhat | 2:d119a85c793c | 61 | #if 1 |
| ubhat | 2:d119a85c793c | 62 | # define VERSION_1 |
| ubhat | 2:d119a85c793c | 63 | #endif |
| ubhat | 2:d119a85c793c | 64 | |
| ubhat | 2:d119a85c793c | 65 | #include "aes.h" |
| ubhat | 2:d119a85c793c | 66 | |
| ubhat | 2:d119a85c793c | 67 | //#if defined( HAVE_UINT_32T ) |
| ubhat | 2:d119a85c793c | 68 | // typedef unsigned long uint32_t; |
| ubhat | 2:d119a85c793c | 69 | //#endif |
| ubhat | 2:d119a85c793c | 70 | |
| ubhat | 2:d119a85c793c | 71 | /* functions for finite field multiplication in the AES Galois field */ |
| ubhat | 2:d119a85c793c | 72 | |
| ubhat | 2:d119a85c793c | 73 | #define WPOLY 0x011b |
| ubhat | 2:d119a85c793c | 74 | #define BPOLY 0x1b |
| ubhat | 2:d119a85c793c | 75 | #define DPOLY 0x008d |
| ubhat | 2:d119a85c793c | 76 | |
| ubhat | 2:d119a85c793c | 77 | #define f1(x) (x) |
| ubhat | 2:d119a85c793c | 78 | #define f2(x) ((x << 1) ^ (((x >> 7) & 1) * WPOLY)) |
| ubhat | 2:d119a85c793c | 79 | #define f4(x) ((x << 2) ^ (((x >> 6) & 1) * WPOLY) ^ (((x >> 6) & 2) * WPOLY)) |
| ubhat | 2:d119a85c793c | 80 | #define f8(x) ((x << 3) ^ (((x >> 5) & 1) * WPOLY) ^ (((x >> 5) & 2) * WPOLY) \ |
| ubhat | 2:d119a85c793c | 81 | ^ (((x >> 5) & 4) * WPOLY)) |
| ubhat | 2:d119a85c793c | 82 | #define d2(x) (((x) >> 1) ^ ((x) & 1 ? DPOLY : 0)) |
| ubhat | 2:d119a85c793c | 83 | |
| ubhat | 2:d119a85c793c | 84 | #define f3(x) (f2(x) ^ x) |
| ubhat | 2:d119a85c793c | 85 | #define f9(x) (f8(x) ^ x) |
| ubhat | 2:d119a85c793c | 86 | #define fb(x) (f8(x) ^ f2(x) ^ x) |
| ubhat | 2:d119a85c793c | 87 | #define fd(x) (f8(x) ^ f4(x) ^ x) |
| ubhat | 2:d119a85c793c | 88 | #define fe(x) (f8(x) ^ f4(x) ^ f2(x)) |
| ubhat | 2:d119a85c793c | 89 | |
| ubhat | 2:d119a85c793c | 90 | #if defined( USE_TABLES ) |
| ubhat | 2:d119a85c793c | 91 | |
| ubhat | 2:d119a85c793c | 92 | #define sb_data(w) { /* S Box data values */ \ |
| ubhat | 2:d119a85c793c | 93 | w(0x63), w(0x7c), w(0x77), w(0x7b), w(0xf2), w(0x6b), w(0x6f), w(0xc5),\ |
| ubhat | 2:d119a85c793c | 94 | w(0x30), w(0x01), w(0x67), w(0x2b), w(0xfe), w(0xd7), w(0xab), w(0x76),\ |
| ubhat | 2:d119a85c793c | 95 | w(0xca), w(0x82), w(0xc9), w(0x7d), w(0xfa), w(0x59), w(0x47), w(0xf0),\ |
| ubhat | 2:d119a85c793c | 96 | w(0xad), w(0xd4), w(0xa2), w(0xaf), w(0x9c), w(0xa4), w(0x72), w(0xc0),\ |
| ubhat | 2:d119a85c793c | 97 | w(0xb7), w(0xfd), w(0x93), w(0x26), w(0x36), w(0x3f), w(0xf7), w(0xcc),\ |
| ubhat | 2:d119a85c793c | 98 | w(0x34), w(0xa5), w(0xe5), w(0xf1), w(0x71), w(0xd8), w(0x31), w(0x15),\ |
| ubhat | 2:d119a85c793c | 99 | w(0x04), w(0xc7), w(0x23), w(0xc3), w(0x18), w(0x96), w(0x05), w(0x9a),\ |
| ubhat | 2:d119a85c793c | 100 | w(0x07), w(0x12), w(0x80), w(0xe2), w(0xeb), w(0x27), w(0xb2), w(0x75),\ |
| ubhat | 2:d119a85c793c | 101 | w(0x09), w(0x83), w(0x2c), w(0x1a), w(0x1b), w(0x6e), w(0x5a), w(0xa0),\ |
| ubhat | 2:d119a85c793c | 102 | w(0x52), w(0x3b), w(0xd6), w(0xb3), w(0x29), w(0xe3), w(0x2f), w(0x84),\ |
| ubhat | 2:d119a85c793c | 103 | w(0x53), w(0xd1), w(0x00), w(0xed), w(0x20), w(0xfc), w(0xb1), w(0x5b),\ |
| ubhat | 2:d119a85c793c | 104 | w(0x6a), w(0xcb), w(0xbe), w(0x39), w(0x4a), w(0x4c), w(0x58), w(0xcf),\ |
| ubhat | 2:d119a85c793c | 105 | w(0xd0), w(0xef), w(0xaa), w(0xfb), w(0x43), w(0x4d), w(0x33), w(0x85),\ |
| ubhat | 2:d119a85c793c | 106 | w(0x45), w(0xf9), w(0x02), w(0x7f), w(0x50), w(0x3c), w(0x9f), w(0xa8),\ |
| ubhat | 2:d119a85c793c | 107 | w(0x51), w(0xa3), w(0x40), w(0x8f), w(0x92), w(0x9d), w(0x38), w(0xf5),\ |
| ubhat | 2:d119a85c793c | 108 | w(0xbc), w(0xb6), w(0xda), w(0x21), w(0x10), w(0xff), w(0xf3), w(0xd2),\ |
| ubhat | 2:d119a85c793c | 109 | w(0xcd), w(0x0c), w(0x13), w(0xec), w(0x5f), w(0x97), w(0x44), w(0x17),\ |
| ubhat | 2:d119a85c793c | 110 | w(0xc4), w(0xa7), w(0x7e), w(0x3d), w(0x64), w(0x5d), w(0x19), w(0x73),\ |
| ubhat | 2:d119a85c793c | 111 | w(0x60), w(0x81), w(0x4f), w(0xdc), w(0x22), w(0x2a), w(0x90), w(0x88),\ |
| ubhat | 2:d119a85c793c | 112 | w(0x46), w(0xee), w(0xb8), w(0x14), w(0xde), w(0x5e), w(0x0b), w(0xdb),\ |
| ubhat | 2:d119a85c793c | 113 | w(0xe0), w(0x32), w(0x3a), w(0x0a), w(0x49), w(0x06), w(0x24), w(0x5c),\ |
| ubhat | 2:d119a85c793c | 114 | w(0xc2), w(0xd3), w(0xac), w(0x62), w(0x91), w(0x95), w(0xe4), w(0x79),\ |
| ubhat | 2:d119a85c793c | 115 | w(0xe7), w(0xc8), w(0x37), w(0x6d), w(0x8d), w(0xd5), w(0x4e), w(0xa9),\ |
| ubhat | 2:d119a85c793c | 116 | w(0x6c), w(0x56), w(0xf4), w(0xea), w(0x65), w(0x7a), w(0xae), w(0x08),\ |
| ubhat | 2:d119a85c793c | 117 | w(0xba), w(0x78), w(0x25), w(0x2e), w(0x1c), w(0xa6), w(0xb4), w(0xc6),\ |
| ubhat | 2:d119a85c793c | 118 | w(0xe8), w(0xdd), w(0x74), w(0x1f), w(0x4b), w(0xbd), w(0x8b), w(0x8a),\ |
| ubhat | 2:d119a85c793c | 119 | w(0x70), w(0x3e), w(0xb5), w(0x66), w(0x48), w(0x03), w(0xf6), w(0x0e),\ |
| ubhat | 2:d119a85c793c | 120 | w(0x61), w(0x35), w(0x57), w(0xb9), w(0x86), w(0xc1), w(0x1d), w(0x9e),\ |
| ubhat | 2:d119a85c793c | 121 | w(0xe1), w(0xf8), w(0x98), w(0x11), w(0x69), w(0xd9), w(0x8e), w(0x94),\ |
| ubhat | 2:d119a85c793c | 122 | w(0x9b), w(0x1e), w(0x87), w(0xe9), w(0xce), w(0x55), w(0x28), w(0xdf),\ |
| ubhat | 2:d119a85c793c | 123 | w(0x8c), w(0xa1), w(0x89), w(0x0d), w(0xbf), w(0xe6), w(0x42), w(0x68),\ |
| ubhat | 2:d119a85c793c | 124 | w(0x41), w(0x99), w(0x2d), w(0x0f), w(0xb0), w(0x54), w(0xbb), w(0x16) } |
| ubhat | 2:d119a85c793c | 125 | |
| ubhat | 2:d119a85c793c | 126 | #define isb_data(w) { /* inverse S Box data values */ \ |
| ubhat | 2:d119a85c793c | 127 | w(0x52), w(0x09), w(0x6a), w(0xd5), w(0x30), w(0x36), w(0xa5), w(0x38),\ |
| ubhat | 2:d119a85c793c | 128 | w(0xbf), w(0x40), w(0xa3), w(0x9e), w(0x81), w(0xf3), w(0xd7), w(0xfb),\ |
| ubhat | 2:d119a85c793c | 129 | w(0x7c), w(0xe3), w(0x39), w(0x82), w(0x9b), w(0x2f), w(0xff), w(0x87),\ |
| ubhat | 2:d119a85c793c | 130 | w(0x34), w(0x8e), w(0x43), w(0x44), w(0xc4), w(0xde), w(0xe9), w(0xcb),\ |
| ubhat | 2:d119a85c793c | 131 | w(0x54), w(0x7b), w(0x94), w(0x32), w(0xa6), w(0xc2), w(0x23), w(0x3d),\ |
| ubhat | 2:d119a85c793c | 132 | w(0xee), w(0x4c), w(0x95), w(0x0b), w(0x42), w(0xfa), w(0xc3), w(0x4e),\ |
| ubhat | 2:d119a85c793c | 133 | w(0x08), w(0x2e), w(0xa1), w(0x66), w(0x28), w(0xd9), w(0x24), w(0xb2),\ |
| ubhat | 2:d119a85c793c | 134 | w(0x76), w(0x5b), w(0xa2), w(0x49), w(0x6d), w(0x8b), w(0xd1), w(0x25),\ |
| ubhat | 2:d119a85c793c | 135 | w(0x72), w(0xf8), w(0xf6), w(0x64), w(0x86), w(0x68), w(0x98), w(0x16),\ |
| ubhat | 2:d119a85c793c | 136 | w(0xd4), w(0xa4), w(0x5c), w(0xcc), w(0x5d), w(0x65), w(0xb6), w(0x92),\ |
| ubhat | 2:d119a85c793c | 137 | w(0x6c), w(0x70), w(0x48), w(0x50), w(0xfd), w(0xed), w(0xb9), w(0xda),\ |
| ubhat | 2:d119a85c793c | 138 | w(0x5e), w(0x15), w(0x46), w(0x57), w(0xa7), w(0x8d), w(0x9d), w(0x84),\ |
| ubhat | 2:d119a85c793c | 139 | w(0x90), w(0xd8), w(0xab), w(0x00), w(0x8c), w(0xbc), w(0xd3), w(0x0a),\ |
| ubhat | 2:d119a85c793c | 140 | w(0xf7), w(0xe4), w(0x58), w(0x05), w(0xb8), w(0xb3), w(0x45), w(0x06),\ |
| ubhat | 2:d119a85c793c | 141 | w(0xd0), w(0x2c), w(0x1e), w(0x8f), w(0xca), w(0x3f), w(0x0f), w(0x02),\ |
| ubhat | 2:d119a85c793c | 142 | w(0xc1), w(0xaf), w(0xbd), w(0x03), w(0x01), w(0x13), w(0x8a), w(0x6b),\ |
| ubhat | 2:d119a85c793c | 143 | w(0x3a), w(0x91), w(0x11), w(0x41), w(0x4f), w(0x67), w(0xdc), w(0xea),\ |
| ubhat | 2:d119a85c793c | 144 | w(0x97), w(0xf2), w(0xcf), w(0xce), w(0xf0), w(0xb4), w(0xe6), w(0x73),\ |
| ubhat | 2:d119a85c793c | 145 | w(0x96), w(0xac), w(0x74), w(0x22), w(0xe7), w(0xad), w(0x35), w(0x85),\ |
| ubhat | 2:d119a85c793c | 146 | w(0xe2), w(0xf9), w(0x37), w(0xe8), w(0x1c), w(0x75), w(0xdf), w(0x6e),\ |
| ubhat | 2:d119a85c793c | 147 | w(0x47), w(0xf1), w(0x1a), w(0x71), w(0x1d), w(0x29), w(0xc5), w(0x89),\ |
| ubhat | 2:d119a85c793c | 148 | w(0x6f), w(0xb7), w(0x62), w(0x0e), w(0xaa), w(0x18), w(0xbe), w(0x1b),\ |
| ubhat | 2:d119a85c793c | 149 | w(0xfc), w(0x56), w(0x3e), w(0x4b), w(0xc6), w(0xd2), w(0x79), w(0x20),\ |
| ubhat | 2:d119a85c793c | 150 | w(0x9a), w(0xdb), w(0xc0), w(0xfe), w(0x78), w(0xcd), w(0x5a), w(0xf4),\ |
| ubhat | 2:d119a85c793c | 151 | w(0x1f), w(0xdd), w(0xa8), w(0x33), w(0x88), w(0x07), w(0xc7), w(0x31),\ |
| ubhat | 2:d119a85c793c | 152 | w(0xb1), w(0x12), w(0x10), w(0x59), w(0x27), w(0x80), w(0xec), w(0x5f),\ |
| ubhat | 2:d119a85c793c | 153 | w(0x60), w(0x51), w(0x7f), w(0xa9), w(0x19), w(0xb5), w(0x4a), w(0x0d),\ |
| ubhat | 2:d119a85c793c | 154 | w(0x2d), w(0xe5), w(0x7a), w(0x9f), w(0x93), w(0xc9), w(0x9c), w(0xef),\ |
| ubhat | 2:d119a85c793c | 155 | w(0xa0), w(0xe0), w(0x3b), w(0x4d), w(0xae), w(0x2a), w(0xf5), w(0xb0),\ |
| ubhat | 2:d119a85c793c | 156 | w(0xc8), w(0xeb), w(0xbb), w(0x3c), w(0x83), w(0x53), w(0x99), w(0x61),\ |
| ubhat | 2:d119a85c793c | 157 | w(0x17), w(0x2b), w(0x04), w(0x7e), w(0xba), w(0x77), w(0xd6), w(0x26),\ |
| ubhat | 2:d119a85c793c | 158 | w(0xe1), w(0x69), w(0x14), w(0x63), w(0x55), w(0x21), w(0x0c), w(0x7d) } |
| ubhat | 2:d119a85c793c | 159 | |
| ubhat | 2:d119a85c793c | 160 | #define mm_data(w) { /* basic data for forming finite field tables */ \ |
| ubhat | 2:d119a85c793c | 161 | w(0x00), w(0x01), w(0x02), w(0x03), w(0x04), w(0x05), w(0x06), w(0x07),\ |
| ubhat | 2:d119a85c793c | 162 | w(0x08), w(0x09), w(0x0a), w(0x0b), w(0x0c), w(0x0d), w(0x0e), w(0x0f),\ |
| ubhat | 2:d119a85c793c | 163 | w(0x10), w(0x11), w(0x12), w(0x13), w(0x14), w(0x15), w(0x16), w(0x17),\ |
| ubhat | 2:d119a85c793c | 164 | w(0x18), w(0x19), w(0x1a), w(0x1b), w(0x1c), w(0x1d), w(0x1e), w(0x1f),\ |
| ubhat | 2:d119a85c793c | 165 | w(0x20), w(0x21), w(0x22), w(0x23), w(0x24), w(0x25), w(0x26), w(0x27),\ |
| ubhat | 2:d119a85c793c | 166 | w(0x28), w(0x29), w(0x2a), w(0x2b), w(0x2c), w(0x2d), w(0x2e), w(0x2f),\ |
| ubhat | 2:d119a85c793c | 167 | w(0x30), w(0x31), w(0x32), w(0x33), w(0x34), w(0x35), w(0x36), w(0x37),\ |
| ubhat | 2:d119a85c793c | 168 | w(0x38), w(0x39), w(0x3a), w(0x3b), w(0x3c), w(0x3d), w(0x3e), w(0x3f),\ |
| ubhat | 2:d119a85c793c | 169 | w(0x40), w(0x41), w(0x42), w(0x43), w(0x44), w(0x45), w(0x46), w(0x47),\ |
| ubhat | 2:d119a85c793c | 170 | w(0x48), w(0x49), w(0x4a), w(0x4b), w(0x4c), w(0x4d), w(0x4e), w(0x4f),\ |
| ubhat | 2:d119a85c793c | 171 | w(0x50), w(0x51), w(0x52), w(0x53), w(0x54), w(0x55), w(0x56), w(0x57),\ |
| ubhat | 2:d119a85c793c | 172 | w(0x58), w(0x59), w(0x5a), w(0x5b), w(0x5c), w(0x5d), w(0x5e), w(0x5f),\ |
| ubhat | 2:d119a85c793c | 173 | w(0x60), w(0x61), w(0x62), w(0x63), w(0x64), w(0x65), w(0x66), w(0x67),\ |
| ubhat | 2:d119a85c793c | 174 | w(0x68), w(0x69), w(0x6a), w(0x6b), w(0x6c), w(0x6d), w(0x6e), w(0x6f),\ |
| ubhat | 2:d119a85c793c | 175 | w(0x70), w(0x71), w(0x72), w(0x73), w(0x74), w(0x75), w(0x76), w(0x77),\ |
| ubhat | 2:d119a85c793c | 176 | w(0x78), w(0x79), w(0x7a), w(0x7b), w(0x7c), w(0x7d), w(0x7e), w(0x7f),\ |
| ubhat | 2:d119a85c793c | 177 | w(0x80), w(0x81), w(0x82), w(0x83), w(0x84), w(0x85), w(0x86), w(0x87),\ |
| ubhat | 2:d119a85c793c | 178 | w(0x88), w(0x89), w(0x8a), w(0x8b), w(0x8c), w(0x8d), w(0x8e), w(0x8f),\ |
| ubhat | 2:d119a85c793c | 179 | w(0x90), w(0x91), w(0x92), w(0x93), w(0x94), w(0x95), w(0x96), w(0x97),\ |
| ubhat | 2:d119a85c793c | 180 | w(0x98), w(0x99), w(0x9a), w(0x9b), w(0x9c), w(0x9d), w(0x9e), w(0x9f),\ |
| ubhat | 2:d119a85c793c | 181 | w(0xa0), w(0xa1), w(0xa2), w(0xa3), w(0xa4), w(0xa5), w(0xa6), w(0xa7),\ |
| ubhat | 2:d119a85c793c | 182 | w(0xa8), w(0xa9), w(0xaa), w(0xab), w(0xac), w(0xad), w(0xae), w(0xaf),\ |
| ubhat | 2:d119a85c793c | 183 | w(0xb0), w(0xb1), w(0xb2), w(0xb3), w(0xb4), w(0xb5), w(0xb6), w(0xb7),\ |
| ubhat | 2:d119a85c793c | 184 | w(0xb8), w(0xb9), w(0xba), w(0xbb), w(0xbc), w(0xbd), w(0xbe), w(0xbf),\ |
| ubhat | 2:d119a85c793c | 185 | w(0xc0), w(0xc1), w(0xc2), w(0xc3), w(0xc4), w(0xc5), w(0xc6), w(0xc7),\ |
| ubhat | 2:d119a85c793c | 186 | w(0xc8), w(0xc9), w(0xca), w(0xcb), w(0xcc), w(0xcd), w(0xce), w(0xcf),\ |
| ubhat | 2:d119a85c793c | 187 | w(0xd0), w(0xd1), w(0xd2), w(0xd3), w(0xd4), w(0xd5), w(0xd6), w(0xd7),\ |
| ubhat | 2:d119a85c793c | 188 | w(0xd8), w(0xd9), w(0xda), w(0xdb), w(0xdc), w(0xdd), w(0xde), w(0xdf),\ |
| ubhat | 2:d119a85c793c | 189 | w(0xe0), w(0xe1), w(0xe2), w(0xe3), w(0xe4), w(0xe5), w(0xe6), w(0xe7),\ |
| ubhat | 2:d119a85c793c | 190 | w(0xe8), w(0xe9), w(0xea), w(0xeb), w(0xec), w(0xed), w(0xee), w(0xef),\ |
| ubhat | 2:d119a85c793c | 191 | w(0xf0), w(0xf1), w(0xf2), w(0xf3), w(0xf4), w(0xf5), w(0xf6), w(0xf7),\ |
| ubhat | 2:d119a85c793c | 192 | w(0xf8), w(0xf9), w(0xfa), w(0xfb), w(0xfc), w(0xfd), w(0xfe), w(0xff) } |
| ubhat | 2:d119a85c793c | 193 | |
| ubhat | 2:d119a85c793c | 194 | static const uint8_t sbox[256] = sb_data(f1); |
| ubhat | 2:d119a85c793c | 195 | |
| ubhat | 2:d119a85c793c | 196 | #if defined( AES_DEC_PREKEYED ) |
| ubhat | 2:d119a85c793c | 197 | static const uint8_t isbox[256] = isb_data(f1); |
| ubhat | 2:d119a85c793c | 198 | #endif |
| ubhat | 2:d119a85c793c | 199 | |
| ubhat | 2:d119a85c793c | 200 | static const uint8_t gfm2_sbox[256] = sb_data(f2); |
| ubhat | 2:d119a85c793c | 201 | static const uint8_t gfm3_sbox[256] = sb_data(f3); |
| ubhat | 2:d119a85c793c | 202 | |
| ubhat | 2:d119a85c793c | 203 | #if defined( AES_DEC_PREKEYED ) |
| ubhat | 2:d119a85c793c | 204 | static const uint8_t gfmul_9[256] = mm_data(f9); |
| ubhat | 2:d119a85c793c | 205 | static const uint8_t gfmul_b[256] = mm_data(fb); |
| ubhat | 2:d119a85c793c | 206 | static const uint8_t gfmul_d[256] = mm_data(fd); |
| ubhat | 2:d119a85c793c | 207 | static const uint8_t gfmul_e[256] = mm_data(fe); |
| ubhat | 2:d119a85c793c | 208 | #endif |
| ubhat | 2:d119a85c793c | 209 | |
| ubhat | 2:d119a85c793c | 210 | #define s_box(x) sbox[(x)] |
| ubhat | 2:d119a85c793c | 211 | #if defined( AES_DEC_PREKEYED ) |
| ubhat | 2:d119a85c793c | 212 | #define is_box(x) isbox[(x)] |
| ubhat | 2:d119a85c793c | 213 | #endif |
| ubhat | 2:d119a85c793c | 214 | #define gfm2_sb(x) gfm2_sbox[(x)] |
| ubhat | 2:d119a85c793c | 215 | #define gfm3_sb(x) gfm3_sbox[(x)] |
| ubhat | 2:d119a85c793c | 216 | #if defined( AES_DEC_PREKEYED ) |
| ubhat | 2:d119a85c793c | 217 | #define gfm_9(x) gfmul_9[(x)] |
| ubhat | 2:d119a85c793c | 218 | #define gfm_b(x) gfmul_b[(x)] |
| ubhat | 2:d119a85c793c | 219 | #define gfm_d(x) gfmul_d[(x)] |
| ubhat | 2:d119a85c793c | 220 | #define gfm_e(x) gfmul_e[(x)] |
| ubhat | 2:d119a85c793c | 221 | #endif |
| ubhat | 2:d119a85c793c | 222 | #else |
| ubhat | 2:d119a85c793c | 223 | |
| ubhat | 2:d119a85c793c | 224 | /* this is the high bit of x right shifted by 1 */ |
| ubhat | 2:d119a85c793c | 225 | /* position. Since the starting polynomial has */ |
| ubhat | 2:d119a85c793c | 226 | /* 9 bits (0x11b), this right shift keeps the */ |
| ubhat | 2:d119a85c793c | 227 | /* values of all top bits within a byte */ |
| ubhat | 2:d119a85c793c | 228 | |
| ubhat | 2:d119a85c793c | 229 | static uint8_t hibit(const uint8_t x) |
| ubhat | 2:d119a85c793c | 230 | { uint8_t r = (uint8_t)((x >> 1) | (x >> 2)); |
| ubhat | 2:d119a85c793c | 231 | |
| ubhat | 2:d119a85c793c | 232 | r |= (r >> 2); |
| ubhat | 2:d119a85c793c | 233 | r |= (r >> 4); |
| ubhat | 2:d119a85c793c | 234 | return (r + 1) >> 1; |
| ubhat | 2:d119a85c793c | 235 | } |
| ubhat | 2:d119a85c793c | 236 | |
| ubhat | 2:d119a85c793c | 237 | /* return the inverse of the finite field element x */ |
| ubhat | 2:d119a85c793c | 238 | |
| ubhat | 2:d119a85c793c | 239 | static uint8_t gf_inv(const uint8_t x) |
| ubhat | 2:d119a85c793c | 240 | { uint8_t p1 = x, p2 = BPOLY, n1 = hibit(x), n2 = 0x80, v1 = 1, v2 = 0; |
| ubhat | 2:d119a85c793c | 241 | |
| ubhat | 2:d119a85c793c | 242 | if(x < 2) |
| ubhat | 2:d119a85c793c | 243 | return x; |
| ubhat | 2:d119a85c793c | 244 | |
| ubhat | 2:d119a85c793c | 245 | for( ; ; ) |
| ubhat | 2:d119a85c793c | 246 | { |
| ubhat | 2:d119a85c793c | 247 | if(n1) |
| ubhat | 2:d119a85c793c | 248 | while(n2 >= n1) /* divide polynomial p2 by p1 */ |
| ubhat | 2:d119a85c793c | 249 | { |
| ubhat | 2:d119a85c793c | 250 | n2 /= n1; /* shift smaller polynomial left */ |
| ubhat | 2:d119a85c793c | 251 | p2 ^= (p1 * n2) & 0xff; /* and remove from larger one */ |
| ubhat | 2:d119a85c793c | 252 | v2 ^= (v1 * n2); /* shift accumulated value and */ |
| ubhat | 2:d119a85c793c | 253 | n2 = hibit(p2); /* add into result */ |
| ubhat | 2:d119a85c793c | 254 | } |
| ubhat | 2:d119a85c793c | 255 | else |
| ubhat | 2:d119a85c793c | 256 | return v1; |
| ubhat | 2:d119a85c793c | 257 | |
| ubhat | 2:d119a85c793c | 258 | if(n2) /* repeat with values swapped */ |
| ubhat | 2:d119a85c793c | 259 | while(n1 >= n2) |
| ubhat | 2:d119a85c793c | 260 | { |
| ubhat | 2:d119a85c793c | 261 | n1 /= n2; |
| ubhat | 2:d119a85c793c | 262 | p1 ^= p2 * n1; |
| ubhat | 2:d119a85c793c | 263 | v1 ^= v2 * n1; |
| ubhat | 2:d119a85c793c | 264 | n1 = hibit(p1); |
| ubhat | 2:d119a85c793c | 265 | } |
| ubhat | 2:d119a85c793c | 266 | else |
| ubhat | 2:d119a85c793c | 267 | return v2; |
| ubhat | 2:d119a85c793c | 268 | } |
| ubhat | 2:d119a85c793c | 269 | } |
| ubhat | 2:d119a85c793c | 270 | |
| ubhat | 2:d119a85c793c | 271 | /* The forward and inverse affine transformations used in the S-box */ |
| ubhat | 2:d119a85c793c | 272 | uint8_t fwd_affine(const uint8_t x) |
| ubhat | 2:d119a85c793c | 273 | { |
| ubhat | 2:d119a85c793c | 274 | #if defined( HAVE_UINT_32T ) |
| ubhat | 2:d119a85c793c | 275 | uint32_t w = x; |
| ubhat | 2:d119a85c793c | 276 | w ^= (w << 1) ^ (w << 2) ^ (w << 3) ^ (w << 4); |
| ubhat | 2:d119a85c793c | 277 | return 0x63 ^ ((w ^ (w >> 8)) & 0xff); |
| ubhat | 2:d119a85c793c | 278 | #else |
| ubhat | 2:d119a85c793c | 279 | return 0x63 ^ x ^ (x << 1) ^ (x << 2) ^ (x << 3) ^ (x << 4) |
| ubhat | 2:d119a85c793c | 280 | ^ (x >> 7) ^ (x >> 6) ^ (x >> 5) ^ (x >> 4); |
| ubhat | 2:d119a85c793c | 281 | #endif |
| ubhat | 2:d119a85c793c | 282 | } |
| ubhat | 2:d119a85c793c | 283 | |
| ubhat | 2:d119a85c793c | 284 | uint8_t inv_affine(const uint8_t x) |
| ubhat | 2:d119a85c793c | 285 | { |
| ubhat | 2:d119a85c793c | 286 | #if defined( HAVE_UINT_32T ) |
| ubhat | 2:d119a85c793c | 287 | uint32_t w = x; |
| ubhat | 2:d119a85c793c | 288 | w = (w << 1) ^ (w << 3) ^ (w << 6); |
| ubhat | 2:d119a85c793c | 289 | return 0x05 ^ ((w ^ (w >> 8)) & 0xff); |
| ubhat | 2:d119a85c793c | 290 | #else |
| ubhat | 2:d119a85c793c | 291 | return 0x05 ^ (x << 1) ^ (x << 3) ^ (x << 6) |
| ubhat | 2:d119a85c793c | 292 | ^ (x >> 7) ^ (x >> 5) ^ (x >> 2); |
| ubhat | 2:d119a85c793c | 293 | #endif |
| ubhat | 2:d119a85c793c | 294 | } |
| ubhat | 2:d119a85c793c | 295 | |
| ubhat | 2:d119a85c793c | 296 | #define s_box(x) fwd_affine(gf_inv(x)) |
| ubhat | 2:d119a85c793c | 297 | #define is_box(x) gf_inv(inv_affine(x)) |
| ubhat | 2:d119a85c793c | 298 | #define gfm2_sb(x) f2(s_box(x)) |
| ubhat | 2:d119a85c793c | 299 | #define gfm3_sb(x) f3(s_box(x)) |
| ubhat | 2:d119a85c793c | 300 | #define gfm_9(x) f9(x) |
| ubhat | 2:d119a85c793c | 301 | #define gfm_b(x) fb(x) |
| ubhat | 2:d119a85c793c | 302 | #define gfm_d(x) fd(x) |
| ubhat | 2:d119a85c793c | 303 | #define gfm_e(x) fe(x) |
| ubhat | 2:d119a85c793c | 304 | |
| ubhat | 2:d119a85c793c | 305 | #endif |
| ubhat | 2:d119a85c793c | 306 | |
| ubhat | 2:d119a85c793c | 307 | #if defined( HAVE_MEMCPY ) |
| ubhat | 2:d119a85c793c | 308 | # define block_copy_nn(d, s, l) memcpy(d, s, l) |
| ubhat | 2:d119a85c793c | 309 | # define block_copy(d, s) memcpy(d, s, N_BLOCK) |
| ubhat | 2:d119a85c793c | 310 | #else |
| ubhat | 2:d119a85c793c | 311 | # define block_copy_nn(d, s, l) copy_block_nn(d, s, l) |
| ubhat | 2:d119a85c793c | 312 | # define block_copy(d, s) copy_block(d, s) |
| ubhat | 2:d119a85c793c | 313 | #endif |
| ubhat | 2:d119a85c793c | 314 | |
| ubhat | 2:d119a85c793c | 315 | static void copy_block( void *d, const void *s ) |
| ubhat | 2:d119a85c793c | 316 | { |
| ubhat | 2:d119a85c793c | 317 | #if defined( HAVE_UINT_32T ) |
| ubhat | 2:d119a85c793c | 318 | ((uint32_t*)d)[ 0] = ((uint32_t*)s)[ 0]; |
| ubhat | 2:d119a85c793c | 319 | ((uint32_t*)d)[ 1] = ((uint32_t*)s)[ 1]; |
| ubhat | 2:d119a85c793c | 320 | ((uint32_t*)d)[ 2] = ((uint32_t*)s)[ 2]; |
| ubhat | 2:d119a85c793c | 321 | ((uint32_t*)d)[ 3] = ((uint32_t*)s)[ 3]; |
| ubhat | 2:d119a85c793c | 322 | #else |
| ubhat | 2:d119a85c793c | 323 | ((uint8_t*)d)[ 0] = ((uint8_t*)s)[ 0]; |
| ubhat | 2:d119a85c793c | 324 | ((uint8_t*)d)[ 1] = ((uint8_t*)s)[ 1]; |
| ubhat | 2:d119a85c793c | 325 | ((uint8_t*)d)[ 2] = ((uint8_t*)s)[ 2]; |
| ubhat | 2:d119a85c793c | 326 | ((uint8_t*)d)[ 3] = ((uint8_t*)s)[ 3]; |
| ubhat | 2:d119a85c793c | 327 | ((uint8_t*)d)[ 4] = ((uint8_t*)s)[ 4]; |
| ubhat | 2:d119a85c793c | 328 | ((uint8_t*)d)[ 5] = ((uint8_t*)s)[ 5]; |
| ubhat | 2:d119a85c793c | 329 | ((uint8_t*)d)[ 6] = ((uint8_t*)s)[ 6]; |
| ubhat | 2:d119a85c793c | 330 | ((uint8_t*)d)[ 7] = ((uint8_t*)s)[ 7]; |
| ubhat | 2:d119a85c793c | 331 | ((uint8_t*)d)[ 8] = ((uint8_t*)s)[ 8]; |
| ubhat | 2:d119a85c793c | 332 | ((uint8_t*)d)[ 9] = ((uint8_t*)s)[ 9]; |
| ubhat | 2:d119a85c793c | 333 | ((uint8_t*)d)[10] = ((uint8_t*)s)[10]; |
| ubhat | 2:d119a85c793c | 334 | ((uint8_t*)d)[11] = ((uint8_t*)s)[11]; |
| ubhat | 2:d119a85c793c | 335 | ((uint8_t*)d)[12] = ((uint8_t*)s)[12]; |
| ubhat | 2:d119a85c793c | 336 | ((uint8_t*)d)[13] = ((uint8_t*)s)[13]; |
| ubhat | 2:d119a85c793c | 337 | ((uint8_t*)d)[14] = ((uint8_t*)s)[14]; |
| ubhat | 2:d119a85c793c | 338 | ((uint8_t*)d)[15] = ((uint8_t*)s)[15]; |
| ubhat | 2:d119a85c793c | 339 | #endif |
| ubhat | 2:d119a85c793c | 340 | } |
| ubhat | 2:d119a85c793c | 341 | |
| ubhat | 2:d119a85c793c | 342 | static void copy_block_nn( uint8_t * d, const uint8_t *s, uint8_t nn ) |
| ubhat | 2:d119a85c793c | 343 | { |
| ubhat | 2:d119a85c793c | 344 | while( nn-- ) |
| ubhat | 2:d119a85c793c | 345 | //*((uint8_t*)d)++ = *((uint8_t*)s)++; |
| ubhat | 2:d119a85c793c | 346 | *d++ = *s++; |
| ubhat | 2:d119a85c793c | 347 | } |
| ubhat | 2:d119a85c793c | 348 | |
| ubhat | 2:d119a85c793c | 349 | static void xor_block( void *d, const void *s ) |
| ubhat | 2:d119a85c793c | 350 | { |
| ubhat | 2:d119a85c793c | 351 | #if defined( HAVE_UINT_32T ) |
| ubhat | 2:d119a85c793c | 352 | ((uint32_t*)d)[ 0] ^= ((uint32_t*)s)[ 0]; |
| ubhat | 2:d119a85c793c | 353 | ((uint32_t*)d)[ 1] ^= ((uint32_t*)s)[ 1]; |
| ubhat | 2:d119a85c793c | 354 | ((uint32_t*)d)[ 2] ^= ((uint32_t*)s)[ 2]; |
| ubhat | 2:d119a85c793c | 355 | ((uint32_t*)d)[ 3] ^= ((uint32_t*)s)[ 3]; |
| ubhat | 2:d119a85c793c | 356 | #else |
| ubhat | 2:d119a85c793c | 357 | ((uint8_t*)d)[ 0] ^= ((uint8_t*)s)[ 0]; |
| ubhat | 2:d119a85c793c | 358 | ((uint8_t*)d)[ 1] ^= ((uint8_t*)s)[ 1]; |
| ubhat | 2:d119a85c793c | 359 | ((uint8_t*)d)[ 2] ^= ((uint8_t*)s)[ 2]; |
| ubhat | 2:d119a85c793c | 360 | ((uint8_t*)d)[ 3] ^= ((uint8_t*)s)[ 3]; |
| ubhat | 2:d119a85c793c | 361 | ((uint8_t*)d)[ 4] ^= ((uint8_t*)s)[ 4]; |
| ubhat | 2:d119a85c793c | 362 | ((uint8_t*)d)[ 5] ^= ((uint8_t*)s)[ 5]; |
| ubhat | 2:d119a85c793c | 363 | ((uint8_t*)d)[ 6] ^= ((uint8_t*)s)[ 6]; |
| ubhat | 2:d119a85c793c | 364 | ((uint8_t*)d)[ 7] ^= ((uint8_t*)s)[ 7]; |
| ubhat | 2:d119a85c793c | 365 | ((uint8_t*)d)[ 8] ^= ((uint8_t*)s)[ 8]; |
| ubhat | 2:d119a85c793c | 366 | ((uint8_t*)d)[ 9] ^= ((uint8_t*)s)[ 9]; |
| ubhat | 2:d119a85c793c | 367 | ((uint8_t*)d)[10] ^= ((uint8_t*)s)[10]; |
| ubhat | 2:d119a85c793c | 368 | ((uint8_t*)d)[11] ^= ((uint8_t*)s)[11]; |
| ubhat | 2:d119a85c793c | 369 | ((uint8_t*)d)[12] ^= ((uint8_t*)s)[12]; |
| ubhat | 2:d119a85c793c | 370 | ((uint8_t*)d)[13] ^= ((uint8_t*)s)[13]; |
| ubhat | 2:d119a85c793c | 371 | ((uint8_t*)d)[14] ^= ((uint8_t*)s)[14]; |
| ubhat | 2:d119a85c793c | 372 | ((uint8_t*)d)[15] ^= ((uint8_t*)s)[15]; |
| ubhat | 2:d119a85c793c | 373 | #endif |
| ubhat | 2:d119a85c793c | 374 | } |
| ubhat | 2:d119a85c793c | 375 | |
| ubhat | 2:d119a85c793c | 376 | static void copy_and_key( void *d, const void *s, const void *k ) |
| ubhat | 2:d119a85c793c | 377 | { |
| ubhat | 2:d119a85c793c | 378 | #if defined( HAVE_UINT_32T ) |
| ubhat | 2:d119a85c793c | 379 | ((uint32_t*)d)[ 0] = ((uint32_t*)s)[ 0] ^ ((uint32_t*)k)[ 0]; |
| ubhat | 2:d119a85c793c | 380 | ((uint32_t*)d)[ 1] = ((uint32_t*)s)[ 1] ^ ((uint32_t*)k)[ 1]; |
| ubhat | 2:d119a85c793c | 381 | ((uint32_t*)d)[ 2] = ((uint32_t*)s)[ 2] ^ ((uint32_t*)k)[ 2]; |
| ubhat | 2:d119a85c793c | 382 | ((uint32_t*)d)[ 3] = ((uint32_t*)s)[ 3] ^ ((uint32_t*)k)[ 3]; |
| ubhat | 2:d119a85c793c | 383 | #elif 1 |
| ubhat | 2:d119a85c793c | 384 | ((uint8_t*)d)[ 0] = ((uint8_t*)s)[ 0] ^ ((uint8_t*)k)[ 0]; |
| ubhat | 2:d119a85c793c | 385 | ((uint8_t*)d)[ 1] = ((uint8_t*)s)[ 1] ^ ((uint8_t*)k)[ 1]; |
| ubhat | 2:d119a85c793c | 386 | ((uint8_t*)d)[ 2] = ((uint8_t*)s)[ 2] ^ ((uint8_t*)k)[ 2]; |
| ubhat | 2:d119a85c793c | 387 | ((uint8_t*)d)[ 3] = ((uint8_t*)s)[ 3] ^ ((uint8_t*)k)[ 3]; |
| ubhat | 2:d119a85c793c | 388 | ((uint8_t*)d)[ 4] = ((uint8_t*)s)[ 4] ^ ((uint8_t*)k)[ 4]; |
| ubhat | 2:d119a85c793c | 389 | ((uint8_t*)d)[ 5] = ((uint8_t*)s)[ 5] ^ ((uint8_t*)k)[ 5]; |
| ubhat | 2:d119a85c793c | 390 | ((uint8_t*)d)[ 6] = ((uint8_t*)s)[ 6] ^ ((uint8_t*)k)[ 6]; |
| ubhat | 2:d119a85c793c | 391 | ((uint8_t*)d)[ 7] = ((uint8_t*)s)[ 7] ^ ((uint8_t*)k)[ 7]; |
| ubhat | 2:d119a85c793c | 392 | ((uint8_t*)d)[ 8] = ((uint8_t*)s)[ 8] ^ ((uint8_t*)k)[ 8]; |
| ubhat | 2:d119a85c793c | 393 | ((uint8_t*)d)[ 9] = ((uint8_t*)s)[ 9] ^ ((uint8_t*)k)[ 9]; |
| ubhat | 2:d119a85c793c | 394 | ((uint8_t*)d)[10] = ((uint8_t*)s)[10] ^ ((uint8_t*)k)[10]; |
| ubhat | 2:d119a85c793c | 395 | ((uint8_t*)d)[11] = ((uint8_t*)s)[11] ^ ((uint8_t*)k)[11]; |
| ubhat | 2:d119a85c793c | 396 | ((uint8_t*)d)[12] = ((uint8_t*)s)[12] ^ ((uint8_t*)k)[12]; |
| ubhat | 2:d119a85c793c | 397 | ((uint8_t*)d)[13] = ((uint8_t*)s)[13] ^ ((uint8_t*)k)[13]; |
| ubhat | 2:d119a85c793c | 398 | ((uint8_t*)d)[14] = ((uint8_t*)s)[14] ^ ((uint8_t*)k)[14]; |
| ubhat | 2:d119a85c793c | 399 | ((uint8_t*)d)[15] = ((uint8_t*)s)[15] ^ ((uint8_t*)k)[15]; |
| ubhat | 2:d119a85c793c | 400 | #else |
| ubhat | 2:d119a85c793c | 401 | block_copy(d, s); |
| ubhat | 2:d119a85c793c | 402 | xor_block(d, k); |
| ubhat | 2:d119a85c793c | 403 | #endif |
| ubhat | 2:d119a85c793c | 404 | } |
| ubhat | 2:d119a85c793c | 405 | |
| ubhat | 2:d119a85c793c | 406 | static void add_round_key( uint8_t d[N_BLOCK], const uint8_t k[N_BLOCK] ) |
| ubhat | 2:d119a85c793c | 407 | { |
| ubhat | 2:d119a85c793c | 408 | xor_block(d, k); |
| ubhat | 2:d119a85c793c | 409 | } |
| ubhat | 2:d119a85c793c | 410 | |
| ubhat | 2:d119a85c793c | 411 | static void shift_sub_rows( uint8_t st[N_BLOCK] ) |
| ubhat | 2:d119a85c793c | 412 | { uint8_t tt; |
| ubhat | 2:d119a85c793c | 413 | |
| ubhat | 2:d119a85c793c | 414 | st[ 0] = s_box(st[ 0]); st[ 4] = s_box(st[ 4]); |
| ubhat | 2:d119a85c793c | 415 | st[ 8] = s_box(st[ 8]); st[12] = s_box(st[12]); |
| ubhat | 2:d119a85c793c | 416 | |
| ubhat | 2:d119a85c793c | 417 | tt = st[1]; st[ 1] = s_box(st[ 5]); st[ 5] = s_box(st[ 9]); |
| ubhat | 2:d119a85c793c | 418 | st[ 9] = s_box(st[13]); st[13] = s_box( tt ); |
| ubhat | 2:d119a85c793c | 419 | |
| ubhat | 2:d119a85c793c | 420 | tt = st[2]; st[ 2] = s_box(st[10]); st[10] = s_box( tt ); |
| ubhat | 2:d119a85c793c | 421 | tt = st[6]; st[ 6] = s_box(st[14]); st[14] = s_box( tt ); |
| ubhat | 2:d119a85c793c | 422 | |
| ubhat | 2:d119a85c793c | 423 | tt = st[15]; st[15] = s_box(st[11]); st[11] = s_box(st[ 7]); |
| ubhat | 2:d119a85c793c | 424 | st[ 7] = s_box(st[ 3]); st[ 3] = s_box( tt ); |
| ubhat | 2:d119a85c793c | 425 | } |
| ubhat | 2:d119a85c793c | 426 | |
| ubhat | 2:d119a85c793c | 427 | #if defined( AES_DEC_PREKEYED ) |
| ubhat | 2:d119a85c793c | 428 | |
| ubhat | 2:d119a85c793c | 429 | static void inv_shift_sub_rows( uint8_t st[N_BLOCK] ) |
| ubhat | 2:d119a85c793c | 430 | { uint8_t tt; |
| ubhat | 2:d119a85c793c | 431 | |
| ubhat | 2:d119a85c793c | 432 | st[ 0] = is_box(st[ 0]); st[ 4] = is_box(st[ 4]); |
| ubhat | 2:d119a85c793c | 433 | st[ 8] = is_box(st[ 8]); st[12] = is_box(st[12]); |
| ubhat | 2:d119a85c793c | 434 | |
| ubhat | 2:d119a85c793c | 435 | tt = st[13]; st[13] = is_box(st[9]); st[ 9] = is_box(st[5]); |
| ubhat | 2:d119a85c793c | 436 | st[ 5] = is_box(st[1]); st[ 1] = is_box( tt ); |
| ubhat | 2:d119a85c793c | 437 | |
| ubhat | 2:d119a85c793c | 438 | tt = st[2]; st[ 2] = is_box(st[10]); st[10] = is_box( tt ); |
| ubhat | 2:d119a85c793c | 439 | tt = st[6]; st[ 6] = is_box(st[14]); st[14] = is_box( tt ); |
| ubhat | 2:d119a85c793c | 440 | |
| ubhat | 2:d119a85c793c | 441 | tt = st[3]; st[ 3] = is_box(st[ 7]); st[ 7] = is_box(st[11]); |
| ubhat | 2:d119a85c793c | 442 | st[11] = is_box(st[15]); st[15] = is_box( tt ); |
| ubhat | 2:d119a85c793c | 443 | } |
| ubhat | 2:d119a85c793c | 444 | |
| ubhat | 2:d119a85c793c | 445 | #endif |
| ubhat | 2:d119a85c793c | 446 | |
| ubhat | 2:d119a85c793c | 447 | #if defined( VERSION_1 ) |
| ubhat | 2:d119a85c793c | 448 | static void mix_sub_columns( uint8_t dt[N_BLOCK] ) |
| ubhat | 2:d119a85c793c | 449 | { uint8_t st[N_BLOCK]; |
| ubhat | 2:d119a85c793c | 450 | block_copy(st, dt); |
| ubhat | 2:d119a85c793c | 451 | #else |
| ubhat | 2:d119a85c793c | 452 | static void mix_sub_columns( uint8_t dt[N_BLOCK], uint8_t st[N_BLOCK] ) |
| ubhat | 2:d119a85c793c | 453 | { |
| ubhat | 2:d119a85c793c | 454 | #endif |
| ubhat | 2:d119a85c793c | 455 | dt[ 0] = gfm2_sb(st[0]) ^ gfm3_sb(st[5]) ^ s_box(st[10]) ^ s_box(st[15]); |
| ubhat | 2:d119a85c793c | 456 | dt[ 1] = s_box(st[0]) ^ gfm2_sb(st[5]) ^ gfm3_sb(st[10]) ^ s_box(st[15]); |
| ubhat | 2:d119a85c793c | 457 | dt[ 2] = s_box(st[0]) ^ s_box(st[5]) ^ gfm2_sb(st[10]) ^ gfm3_sb(st[15]); |
| ubhat | 2:d119a85c793c | 458 | dt[ 3] = gfm3_sb(st[0]) ^ s_box(st[5]) ^ s_box(st[10]) ^ gfm2_sb(st[15]); |
| ubhat | 2:d119a85c793c | 459 | |
| ubhat | 2:d119a85c793c | 460 | dt[ 4] = gfm2_sb(st[4]) ^ gfm3_sb(st[9]) ^ s_box(st[14]) ^ s_box(st[3]); |
| ubhat | 2:d119a85c793c | 461 | dt[ 5] = s_box(st[4]) ^ gfm2_sb(st[9]) ^ gfm3_sb(st[14]) ^ s_box(st[3]); |
| ubhat | 2:d119a85c793c | 462 | dt[ 6] = s_box(st[4]) ^ s_box(st[9]) ^ gfm2_sb(st[14]) ^ gfm3_sb(st[3]); |
| ubhat | 2:d119a85c793c | 463 | dt[ 7] = gfm3_sb(st[4]) ^ s_box(st[9]) ^ s_box(st[14]) ^ gfm2_sb(st[3]); |
| ubhat | 2:d119a85c793c | 464 | |
| ubhat | 2:d119a85c793c | 465 | dt[ 8] = gfm2_sb(st[8]) ^ gfm3_sb(st[13]) ^ s_box(st[2]) ^ s_box(st[7]); |
| ubhat | 2:d119a85c793c | 466 | dt[ 9] = s_box(st[8]) ^ gfm2_sb(st[13]) ^ gfm3_sb(st[2]) ^ s_box(st[7]); |
| ubhat | 2:d119a85c793c | 467 | dt[10] = s_box(st[8]) ^ s_box(st[13]) ^ gfm2_sb(st[2]) ^ gfm3_sb(st[7]); |
| ubhat | 2:d119a85c793c | 468 | dt[11] = gfm3_sb(st[8]) ^ s_box(st[13]) ^ s_box(st[2]) ^ gfm2_sb(st[7]); |
| ubhat | 2:d119a85c793c | 469 | |
| ubhat | 2:d119a85c793c | 470 | dt[12] = gfm2_sb(st[12]) ^ gfm3_sb(st[1]) ^ s_box(st[6]) ^ s_box(st[11]); |
| ubhat | 2:d119a85c793c | 471 | dt[13] = s_box(st[12]) ^ gfm2_sb(st[1]) ^ gfm3_sb(st[6]) ^ s_box(st[11]); |
| ubhat | 2:d119a85c793c | 472 | dt[14] = s_box(st[12]) ^ s_box(st[1]) ^ gfm2_sb(st[6]) ^ gfm3_sb(st[11]); |
| ubhat | 2:d119a85c793c | 473 | dt[15] = gfm3_sb(st[12]) ^ s_box(st[1]) ^ s_box(st[6]) ^ gfm2_sb(st[11]); |
| ubhat | 2:d119a85c793c | 474 | } |
| ubhat | 2:d119a85c793c | 475 | |
| ubhat | 2:d119a85c793c | 476 | #if defined( AES_DEC_PREKEYED ) |
| ubhat | 2:d119a85c793c | 477 | |
| ubhat | 2:d119a85c793c | 478 | #if defined( VERSION_1 ) |
| ubhat | 2:d119a85c793c | 479 | static void inv_mix_sub_columns( uint8_t dt[N_BLOCK] ) |
| ubhat | 2:d119a85c793c | 480 | { uint8_t st[N_BLOCK]; |
| ubhat | 2:d119a85c793c | 481 | block_copy(st, dt); |
| ubhat | 2:d119a85c793c | 482 | #else |
| ubhat | 2:d119a85c793c | 483 | static void inv_mix_sub_columns( uint8_t dt[N_BLOCK], uint8_t st[N_BLOCK] ) |
| ubhat | 2:d119a85c793c | 484 | { |
| ubhat | 2:d119a85c793c | 485 | #endif |
| ubhat | 2:d119a85c793c | 486 | dt[ 0] = is_box(gfm_e(st[ 0]) ^ gfm_b(st[ 1]) ^ gfm_d(st[ 2]) ^ gfm_9(st[ 3])); |
| ubhat | 2:d119a85c793c | 487 | dt[ 5] = is_box(gfm_9(st[ 0]) ^ gfm_e(st[ 1]) ^ gfm_b(st[ 2]) ^ gfm_d(st[ 3])); |
| ubhat | 2:d119a85c793c | 488 | dt[10] = is_box(gfm_d(st[ 0]) ^ gfm_9(st[ 1]) ^ gfm_e(st[ 2]) ^ gfm_b(st[ 3])); |
| ubhat | 2:d119a85c793c | 489 | dt[15] = is_box(gfm_b(st[ 0]) ^ gfm_d(st[ 1]) ^ gfm_9(st[ 2]) ^ gfm_e(st[ 3])); |
| ubhat | 2:d119a85c793c | 490 | |
| ubhat | 2:d119a85c793c | 491 | dt[ 4] = is_box(gfm_e(st[ 4]) ^ gfm_b(st[ 5]) ^ gfm_d(st[ 6]) ^ gfm_9(st[ 7])); |
| ubhat | 2:d119a85c793c | 492 | dt[ 9] = is_box(gfm_9(st[ 4]) ^ gfm_e(st[ 5]) ^ gfm_b(st[ 6]) ^ gfm_d(st[ 7])); |
| ubhat | 2:d119a85c793c | 493 | dt[14] = is_box(gfm_d(st[ 4]) ^ gfm_9(st[ 5]) ^ gfm_e(st[ 6]) ^ gfm_b(st[ 7])); |
| ubhat | 2:d119a85c793c | 494 | dt[ 3] = is_box(gfm_b(st[ 4]) ^ gfm_d(st[ 5]) ^ gfm_9(st[ 6]) ^ gfm_e(st[ 7])); |
| ubhat | 2:d119a85c793c | 495 | |
| ubhat | 2:d119a85c793c | 496 | dt[ 8] = is_box(gfm_e(st[ 8]) ^ gfm_b(st[ 9]) ^ gfm_d(st[10]) ^ gfm_9(st[11])); |
| ubhat | 2:d119a85c793c | 497 | dt[13] = is_box(gfm_9(st[ 8]) ^ gfm_e(st[ 9]) ^ gfm_b(st[10]) ^ gfm_d(st[11])); |
| ubhat | 2:d119a85c793c | 498 | dt[ 2] = is_box(gfm_d(st[ 8]) ^ gfm_9(st[ 9]) ^ gfm_e(st[10]) ^ gfm_b(st[11])); |
| ubhat | 2:d119a85c793c | 499 | dt[ 7] = is_box(gfm_b(st[ 8]) ^ gfm_d(st[ 9]) ^ gfm_9(st[10]) ^ gfm_e(st[11])); |
| ubhat | 2:d119a85c793c | 500 | |
| ubhat | 2:d119a85c793c | 501 | dt[12] = is_box(gfm_e(st[12]) ^ gfm_b(st[13]) ^ gfm_d(st[14]) ^ gfm_9(st[15])); |
| ubhat | 2:d119a85c793c | 502 | dt[ 1] = is_box(gfm_9(st[12]) ^ gfm_e(st[13]) ^ gfm_b(st[14]) ^ gfm_d(st[15])); |
| ubhat | 2:d119a85c793c | 503 | dt[ 6] = is_box(gfm_d(st[12]) ^ gfm_9(st[13]) ^ gfm_e(st[14]) ^ gfm_b(st[15])); |
| ubhat | 2:d119a85c793c | 504 | dt[11] = is_box(gfm_b(st[12]) ^ gfm_d(st[13]) ^ gfm_9(st[14]) ^ gfm_e(st[15])); |
| ubhat | 2:d119a85c793c | 505 | } |
| ubhat | 2:d119a85c793c | 506 | |
| ubhat | 2:d119a85c793c | 507 | #endif |
| ubhat | 2:d119a85c793c | 508 | |
| ubhat | 2:d119a85c793c | 509 | #if defined( AES_ENC_PREKEYED ) || defined( AES_DEC_PREKEYED ) |
| ubhat | 2:d119a85c793c | 510 | |
| ubhat | 2:d119a85c793c | 511 | /* Set the cipher key for the pre-keyed version */ |
| ubhat | 2:d119a85c793c | 512 | |
| ubhat | 2:d119a85c793c | 513 | return_type aes_set_key( const uint8_t key[], length_type keylen, aes_context ctx[1] ) |
| ubhat | 2:d119a85c793c | 514 | { |
| ubhat | 2:d119a85c793c | 515 | uint8_t cc, rc, hi; |
| ubhat | 2:d119a85c793c | 516 | |
| ubhat | 2:d119a85c793c | 517 | switch( keylen ) |
| ubhat | 2:d119a85c793c | 518 | { |
| ubhat | 2:d119a85c793c | 519 | case 16: |
| ubhat | 2:d119a85c793c | 520 | case 24: |
| ubhat | 2:d119a85c793c | 521 | case 32: |
| ubhat | 2:d119a85c793c | 522 | break; |
| ubhat | 2:d119a85c793c | 523 | default: |
| ubhat | 2:d119a85c793c | 524 | ctx->rnd = 0; |
| ubhat | 2:d119a85c793c | 525 | return ( uint8_t )-1; |
| ubhat | 2:d119a85c793c | 526 | } |
| ubhat | 2:d119a85c793c | 527 | block_copy_nn(ctx->ksch, key, keylen); |
| ubhat | 2:d119a85c793c | 528 | hi = (keylen + 28) << 2; |
| ubhat | 2:d119a85c793c | 529 | ctx->rnd = (hi >> 4) - 1; |
| ubhat | 2:d119a85c793c | 530 | for( cc = keylen, rc = 1; cc < hi; cc += 4 ) |
| ubhat | 2:d119a85c793c | 531 | { uint8_t tt, t0, t1, t2, t3; |
| ubhat | 2:d119a85c793c | 532 | |
| ubhat | 2:d119a85c793c | 533 | t0 = ctx->ksch[cc - 4]; |
| ubhat | 2:d119a85c793c | 534 | t1 = ctx->ksch[cc - 3]; |
| ubhat | 2:d119a85c793c | 535 | t2 = ctx->ksch[cc - 2]; |
| ubhat | 2:d119a85c793c | 536 | t3 = ctx->ksch[cc - 1]; |
| ubhat | 2:d119a85c793c | 537 | if( cc % keylen == 0 ) |
| ubhat | 2:d119a85c793c | 538 | { |
| ubhat | 2:d119a85c793c | 539 | tt = t0; |
| ubhat | 2:d119a85c793c | 540 | t0 = s_box(t1) ^ rc; |
| ubhat | 2:d119a85c793c | 541 | t1 = s_box(t2); |
| ubhat | 2:d119a85c793c | 542 | t2 = s_box(t3); |
| ubhat | 2:d119a85c793c | 543 | t3 = s_box(tt); |
| ubhat | 2:d119a85c793c | 544 | rc = f2(rc); |
| ubhat | 2:d119a85c793c | 545 | } |
| ubhat | 2:d119a85c793c | 546 | else if( keylen > 24 && cc % keylen == 16 ) |
| ubhat | 2:d119a85c793c | 547 | { |
| ubhat | 2:d119a85c793c | 548 | t0 = s_box(t0); |
| ubhat | 2:d119a85c793c | 549 | t1 = s_box(t1); |
| ubhat | 2:d119a85c793c | 550 | t2 = s_box(t2); |
| ubhat | 2:d119a85c793c | 551 | t3 = s_box(t3); |
| ubhat | 2:d119a85c793c | 552 | } |
| ubhat | 2:d119a85c793c | 553 | tt = cc - keylen; |
| ubhat | 2:d119a85c793c | 554 | ctx->ksch[cc + 0] = ctx->ksch[tt + 0] ^ t0; |
| ubhat | 2:d119a85c793c | 555 | ctx->ksch[cc + 1] = ctx->ksch[tt + 1] ^ t1; |
| ubhat | 2:d119a85c793c | 556 | ctx->ksch[cc + 2] = ctx->ksch[tt + 2] ^ t2; |
| ubhat | 2:d119a85c793c | 557 | ctx->ksch[cc + 3] = ctx->ksch[tt + 3] ^ t3; |
| ubhat | 2:d119a85c793c | 558 | } |
| ubhat | 2:d119a85c793c | 559 | return 0; |
| ubhat | 2:d119a85c793c | 560 | } |
| ubhat | 2:d119a85c793c | 561 | |
| ubhat | 2:d119a85c793c | 562 | #endif |
| ubhat | 2:d119a85c793c | 563 | |
| ubhat | 2:d119a85c793c | 564 | #if defined( AES_ENC_PREKEYED ) |
| ubhat | 2:d119a85c793c | 565 | |
| ubhat | 2:d119a85c793c | 566 | /* Encrypt a single block of 16 bytes */ |
| ubhat | 2:d119a85c793c | 567 | |
| ubhat | 2:d119a85c793c | 568 | return_type aes_encrypt( const uint8_t in[N_BLOCK], uint8_t out[N_BLOCK], const aes_context ctx[1] ) |
| ubhat | 2:d119a85c793c | 569 | { |
| ubhat | 2:d119a85c793c | 570 | if( ctx->rnd ) |
| ubhat | 2:d119a85c793c | 571 | { |
| ubhat | 2:d119a85c793c | 572 | uint8_t s1[N_BLOCK], r; |
| ubhat | 2:d119a85c793c | 573 | copy_and_key( s1, in, ctx->ksch ); |
| ubhat | 2:d119a85c793c | 574 | |
| ubhat | 2:d119a85c793c | 575 | for( r = 1 ; r < ctx->rnd ; ++r ) |
| ubhat | 2:d119a85c793c | 576 | #if defined( VERSION_1 ) |
| ubhat | 2:d119a85c793c | 577 | { |
| ubhat | 2:d119a85c793c | 578 | mix_sub_columns( s1 ); |
| ubhat | 2:d119a85c793c | 579 | add_round_key( s1, ctx->ksch + r * N_BLOCK); |
| ubhat | 2:d119a85c793c | 580 | } |
| ubhat | 2:d119a85c793c | 581 | #else |
| ubhat | 2:d119a85c793c | 582 | { uint8_t s2[N_BLOCK]; |
| ubhat | 2:d119a85c793c | 583 | mix_sub_columns( s2, s1 ); |
| ubhat | 2:d119a85c793c | 584 | copy_and_key( s1, s2, ctx->ksch + r * N_BLOCK); |
| ubhat | 2:d119a85c793c | 585 | } |
| ubhat | 2:d119a85c793c | 586 | #endif |
| ubhat | 2:d119a85c793c | 587 | shift_sub_rows( s1 ); |
| ubhat | 2:d119a85c793c | 588 | copy_and_key( out, s1, ctx->ksch + r * N_BLOCK ); |
| ubhat | 2:d119a85c793c | 589 | } |
| ubhat | 2:d119a85c793c | 590 | else |
| ubhat | 2:d119a85c793c | 591 | return ( uint8_t )-1; |
| ubhat | 2:d119a85c793c | 592 | return 0; |
| ubhat | 2:d119a85c793c | 593 | } |
| ubhat | 2:d119a85c793c | 594 | |
| ubhat | 2:d119a85c793c | 595 | /* CBC encrypt a number of blocks (input and return an IV) */ |
| ubhat | 2:d119a85c793c | 596 | |
| ubhat | 2:d119a85c793c | 597 | return_type aes_cbc_encrypt( const uint8_t *in, uint8_t *out, |
| ubhat | 2:d119a85c793c | 598 | int32_t n_block, uint8_t iv[N_BLOCK], const aes_context ctx[1] ) |
| ubhat | 2:d119a85c793c | 599 | { |
| ubhat | 2:d119a85c793c | 600 | |
| ubhat | 2:d119a85c793c | 601 | while(n_block--) |
| ubhat | 2:d119a85c793c | 602 | { |
| ubhat | 2:d119a85c793c | 603 | xor_block(iv, in); |
| ubhat | 2:d119a85c793c | 604 | if(aes_encrypt(iv, iv, ctx) != EXIT_SUCCESS) |
| ubhat | 2:d119a85c793c | 605 | return EXIT_FAILURE; |
| ubhat | 2:d119a85c793c | 606 | //memcpy(out, iv, N_BLOCK); |
| ubhat | 2:d119a85c793c | 607 | block_copy(out, iv); |
| ubhat | 2:d119a85c793c | 608 | in += N_BLOCK; |
| ubhat | 2:d119a85c793c | 609 | out += N_BLOCK; |
| ubhat | 2:d119a85c793c | 610 | } |
| ubhat | 2:d119a85c793c | 611 | return EXIT_SUCCESS; |
| ubhat | 2:d119a85c793c | 612 | } |
| ubhat | 2:d119a85c793c | 613 | |
| ubhat | 2:d119a85c793c | 614 | #endif |
| ubhat | 2:d119a85c793c | 615 | |
| ubhat | 2:d119a85c793c | 616 | #if defined( AES_DEC_PREKEYED ) |
| ubhat | 2:d119a85c793c | 617 | |
| ubhat | 2:d119a85c793c | 618 | /* Decrypt a single block of 16 bytes */ |
| ubhat | 2:d119a85c793c | 619 | |
| ubhat | 2:d119a85c793c | 620 | return_type aes_decrypt( const uint8_t in[N_BLOCK], uint8_t out[N_BLOCK], const aes_context ctx[1] ) |
| ubhat | 2:d119a85c793c | 621 | { |
| ubhat | 2:d119a85c793c | 622 | if( ctx->rnd ) |
| ubhat | 2:d119a85c793c | 623 | { |
| ubhat | 2:d119a85c793c | 624 | uint8_t s1[N_BLOCK], r; |
| ubhat | 2:d119a85c793c | 625 | copy_and_key( s1, in, ctx->ksch + ctx->rnd * N_BLOCK ); |
| ubhat | 2:d119a85c793c | 626 | inv_shift_sub_rows( s1 ); |
| ubhat | 2:d119a85c793c | 627 | |
| ubhat | 2:d119a85c793c | 628 | for( r = ctx->rnd ; --r ; ) |
| ubhat | 2:d119a85c793c | 629 | #if defined( VERSION_1 ) |
| ubhat | 2:d119a85c793c | 630 | { |
| ubhat | 2:d119a85c793c | 631 | add_round_key( s1, ctx->ksch + r * N_BLOCK ); |
| ubhat | 2:d119a85c793c | 632 | inv_mix_sub_columns( s1 ); |
| ubhat | 2:d119a85c793c | 633 | } |
| ubhat | 2:d119a85c793c | 634 | #else |
| ubhat | 2:d119a85c793c | 635 | { uint8_t s2[N_BLOCK]; |
| ubhat | 2:d119a85c793c | 636 | copy_and_key( s2, s1, ctx->ksch + r * N_BLOCK ); |
| ubhat | 2:d119a85c793c | 637 | inv_mix_sub_columns( s1, s2 ); |
| ubhat | 2:d119a85c793c | 638 | } |
| ubhat | 2:d119a85c793c | 639 | #endif |
| ubhat | 2:d119a85c793c | 640 | copy_and_key( out, s1, ctx->ksch ); |
| ubhat | 2:d119a85c793c | 641 | } |
| ubhat | 2:d119a85c793c | 642 | else |
| ubhat | 2:d119a85c793c | 643 | return -1; |
| ubhat | 2:d119a85c793c | 644 | return 0; |
| ubhat | 2:d119a85c793c | 645 | } |
| ubhat | 2:d119a85c793c | 646 | |
| ubhat | 2:d119a85c793c | 647 | /* CBC decrypt a number of blocks (input and return an IV) */ |
| ubhat | 2:d119a85c793c | 648 | |
| ubhat | 2:d119a85c793c | 649 | return_type aes_cbc_decrypt( const uint8_t *in, uint8_t *out, |
| ubhat | 2:d119a85c793c | 650 | int32_t n_block, uint8_t iv[N_BLOCK], const aes_context ctx[1] ) |
| ubhat | 2:d119a85c793c | 651 | { |
| ubhat | 2:d119a85c793c | 652 | while(n_block--) |
| ubhat | 2:d119a85c793c | 653 | { uint8_t tmp[N_BLOCK]; |
| ubhat | 2:d119a85c793c | 654 | |
| ubhat | 2:d119a85c793c | 655 | //memcpy(tmp, in, N_BLOCK); |
| ubhat | 2:d119a85c793c | 656 | block_copy(tmp, in); |
| ubhat | 2:d119a85c793c | 657 | if(aes_decrypt(in, out, ctx) != EXIT_SUCCESS) |
| ubhat | 2:d119a85c793c | 658 | return EXIT_FAILURE; |
| ubhat | 2:d119a85c793c | 659 | xor_block(out, iv); |
| ubhat | 2:d119a85c793c | 660 | //memcpy(iv, tmp, N_BLOCK); |
| ubhat | 2:d119a85c793c | 661 | block_copy(iv, tmp); |
| ubhat | 2:d119a85c793c | 662 | in += N_BLOCK; |
| ubhat | 2:d119a85c793c | 663 | out += N_BLOCK; |
| ubhat | 2:d119a85c793c | 664 | } |
| ubhat | 2:d119a85c793c | 665 | return EXIT_SUCCESS; |
| ubhat | 2:d119a85c793c | 666 | } |
| ubhat | 2:d119a85c793c | 667 | |
| ubhat | 2:d119a85c793c | 668 | #endif |
| ubhat | 2:d119a85c793c | 669 | |
| ubhat | 2:d119a85c793c | 670 | #if defined( AES_ENC_128_OTFK ) |
| ubhat | 2:d119a85c793c | 671 | |
| ubhat | 2:d119a85c793c | 672 | /* The 'on the fly' encryption key update for for 128 bit keys */ |
| ubhat | 2:d119a85c793c | 673 | |
| ubhat | 2:d119a85c793c | 674 | static void update_encrypt_key_128( uint8_t k[N_BLOCK], uint8_t *rc ) |
| ubhat | 2:d119a85c793c | 675 | { uint8_t cc; |
| ubhat | 2:d119a85c793c | 676 | |
| ubhat | 2:d119a85c793c | 677 | k[0] ^= s_box(k[13]) ^ *rc; |
| ubhat | 2:d119a85c793c | 678 | k[1] ^= s_box(k[14]); |
| ubhat | 2:d119a85c793c | 679 | k[2] ^= s_box(k[15]); |
| ubhat | 2:d119a85c793c | 680 | k[3] ^= s_box(k[12]); |
| ubhat | 2:d119a85c793c | 681 | *rc = f2( *rc ); |
| ubhat | 2:d119a85c793c | 682 | |
| ubhat | 2:d119a85c793c | 683 | for(cc = 4; cc < 16; cc += 4 ) |
| ubhat | 2:d119a85c793c | 684 | { |
| ubhat | 2:d119a85c793c | 685 | k[cc + 0] ^= k[cc - 4]; |
| ubhat | 2:d119a85c793c | 686 | k[cc + 1] ^= k[cc - 3]; |
| ubhat | 2:d119a85c793c | 687 | k[cc + 2] ^= k[cc - 2]; |
| ubhat | 2:d119a85c793c | 688 | k[cc + 3] ^= k[cc - 1]; |
| ubhat | 2:d119a85c793c | 689 | } |
| ubhat | 2:d119a85c793c | 690 | } |
| ubhat | 2:d119a85c793c | 691 | |
| ubhat | 2:d119a85c793c | 692 | /* Encrypt a single block of 16 bytes with 'on the fly' 128 bit keying */ |
| ubhat | 2:d119a85c793c | 693 | |
| ubhat | 2:d119a85c793c | 694 | void aes_encrypt_128( const uint8_t in[N_BLOCK], uint8_t out[N_BLOCK], |
| ubhat | 2:d119a85c793c | 695 | const uint8_t key[N_BLOCK], uint8_t o_key[N_BLOCK] ) |
| ubhat | 2:d119a85c793c | 696 | { uint8_t s1[N_BLOCK], r, rc = 1; |
| ubhat | 2:d119a85c793c | 697 | |
| ubhat | 2:d119a85c793c | 698 | if(o_key != key) |
| ubhat | 2:d119a85c793c | 699 | block_copy( o_key, key ); |
| ubhat | 2:d119a85c793c | 700 | copy_and_key( s1, in, o_key ); |
| ubhat | 2:d119a85c793c | 701 | |
| ubhat | 2:d119a85c793c | 702 | for( r = 1 ; r < 10 ; ++r ) |
| ubhat | 2:d119a85c793c | 703 | #if defined( VERSION_1 ) |
| ubhat | 2:d119a85c793c | 704 | { |
| ubhat | 2:d119a85c793c | 705 | mix_sub_columns( s1 ); |
| ubhat | 2:d119a85c793c | 706 | update_encrypt_key_128( o_key, &rc ); |
| ubhat | 2:d119a85c793c | 707 | add_round_key( s1, o_key ); |
| ubhat | 2:d119a85c793c | 708 | } |
| ubhat | 2:d119a85c793c | 709 | #else |
| ubhat | 2:d119a85c793c | 710 | { uint8_t s2[N_BLOCK]; |
| ubhat | 2:d119a85c793c | 711 | mix_sub_columns( s2, s1 ); |
| ubhat | 2:d119a85c793c | 712 | update_encrypt_key_128( o_key, &rc ); |
| ubhat | 2:d119a85c793c | 713 | copy_and_key( s1, s2, o_key ); |
| ubhat | 2:d119a85c793c | 714 | } |
| ubhat | 2:d119a85c793c | 715 | #endif |
| ubhat | 2:d119a85c793c | 716 | |
| ubhat | 2:d119a85c793c | 717 | shift_sub_rows( s1 ); |
| ubhat | 2:d119a85c793c | 718 | update_encrypt_key_128( o_key, &rc ); |
| ubhat | 2:d119a85c793c | 719 | copy_and_key( out, s1, o_key ); |
| ubhat | 2:d119a85c793c | 720 | } |
| ubhat | 2:d119a85c793c | 721 | |
| ubhat | 2:d119a85c793c | 722 | #endif |
| ubhat | 2:d119a85c793c | 723 | |
| ubhat | 2:d119a85c793c | 724 | #if defined( AES_DEC_128_OTFK ) |
| ubhat | 2:d119a85c793c | 725 | |
| ubhat | 2:d119a85c793c | 726 | /* The 'on the fly' decryption key update for for 128 bit keys */ |
| ubhat | 2:d119a85c793c | 727 | |
| ubhat | 2:d119a85c793c | 728 | static void update_decrypt_key_128( uint8_t k[N_BLOCK], uint8_t *rc ) |
| ubhat | 2:d119a85c793c | 729 | { uint8_t cc; |
| ubhat | 2:d119a85c793c | 730 | |
| ubhat | 2:d119a85c793c | 731 | for( cc = 12; cc > 0; cc -= 4 ) |
| ubhat | 2:d119a85c793c | 732 | { |
| ubhat | 2:d119a85c793c | 733 | k[cc + 0] ^= k[cc - 4]; |
| ubhat | 2:d119a85c793c | 734 | k[cc + 1] ^= k[cc - 3]; |
| ubhat | 2:d119a85c793c | 735 | k[cc + 2] ^= k[cc - 2]; |
| ubhat | 2:d119a85c793c | 736 | k[cc + 3] ^= k[cc - 1]; |
| ubhat | 2:d119a85c793c | 737 | } |
| ubhat | 2:d119a85c793c | 738 | *rc = d2(*rc); |
| ubhat | 2:d119a85c793c | 739 | k[0] ^= s_box(k[13]) ^ *rc; |
| ubhat | 2:d119a85c793c | 740 | k[1] ^= s_box(k[14]); |
| ubhat | 2:d119a85c793c | 741 | k[2] ^= s_box(k[15]); |
| ubhat | 2:d119a85c793c | 742 | k[3] ^= s_box(k[12]); |
| ubhat | 2:d119a85c793c | 743 | } |
| ubhat | 2:d119a85c793c | 744 | |
| ubhat | 2:d119a85c793c | 745 | /* Decrypt a single block of 16 bytes with 'on the fly' 128 bit keying */ |
| ubhat | 2:d119a85c793c | 746 | |
| ubhat | 2:d119a85c793c | 747 | void aes_decrypt_128( const uint8_t in[N_BLOCK], uint8_t out[N_BLOCK], |
| ubhat | 2:d119a85c793c | 748 | const uint8_t key[N_BLOCK], uint8_t o_key[N_BLOCK] ) |
| ubhat | 2:d119a85c793c | 749 | { |
| ubhat | 2:d119a85c793c | 750 | uint8_t s1[N_BLOCK], r, rc = 0x6c; |
| ubhat | 2:d119a85c793c | 751 | if(o_key != key) |
| ubhat | 2:d119a85c793c | 752 | block_copy( o_key, key ); |
| ubhat | 2:d119a85c793c | 753 | |
| ubhat | 2:d119a85c793c | 754 | copy_and_key( s1, in, o_key ); |
| ubhat | 2:d119a85c793c | 755 | inv_shift_sub_rows( s1 ); |
| ubhat | 2:d119a85c793c | 756 | |
| ubhat | 2:d119a85c793c | 757 | for( r = 10 ; --r ; ) |
| ubhat | 2:d119a85c793c | 758 | #if defined( VERSION_1 ) |
| ubhat | 2:d119a85c793c | 759 | { |
| ubhat | 2:d119a85c793c | 760 | update_decrypt_key_128( o_key, &rc ); |
| ubhat | 2:d119a85c793c | 761 | add_round_key( s1, o_key ); |
| ubhat | 2:d119a85c793c | 762 | inv_mix_sub_columns( s1 ); |
| ubhat | 2:d119a85c793c | 763 | } |
| ubhat | 2:d119a85c793c | 764 | #else |
| ubhat | 2:d119a85c793c | 765 | { uint8_t s2[N_BLOCK]; |
| ubhat | 2:d119a85c793c | 766 | update_decrypt_key_128( o_key, &rc ); |
| ubhat | 2:d119a85c793c | 767 | copy_and_key( s2, s1, o_key ); |
| ubhat | 2:d119a85c793c | 768 | inv_mix_sub_columns( s1, s2 ); |
| ubhat | 2:d119a85c793c | 769 | } |
| ubhat | 2:d119a85c793c | 770 | #endif |
| ubhat | 2:d119a85c793c | 771 | update_decrypt_key_128( o_key, &rc ); |
| ubhat | 2:d119a85c793c | 772 | copy_and_key( out, s1, o_key ); |
| ubhat | 2:d119a85c793c | 773 | } |
| ubhat | 2:d119a85c793c | 774 | |
| ubhat | 2:d119a85c793c | 775 | #endif |
| ubhat | 2:d119a85c793c | 776 | |
| ubhat | 2:d119a85c793c | 777 | #if defined( AES_ENC_256_OTFK ) |
| ubhat | 2:d119a85c793c | 778 | |
| ubhat | 2:d119a85c793c | 779 | /* The 'on the fly' encryption key update for for 256 bit keys */ |
| ubhat | 2:d119a85c793c | 780 | |
| ubhat | 2:d119a85c793c | 781 | static void update_encrypt_key_256( uint8_t k[2 * N_BLOCK], uint8_t *rc ) |
| ubhat | 2:d119a85c793c | 782 | { uint8_t cc; |
| ubhat | 2:d119a85c793c | 783 | |
| ubhat | 2:d119a85c793c | 784 | k[0] ^= s_box(k[29]) ^ *rc; |
| ubhat | 2:d119a85c793c | 785 | k[1] ^= s_box(k[30]); |
| ubhat | 2:d119a85c793c | 786 | k[2] ^= s_box(k[31]); |
| ubhat | 2:d119a85c793c | 787 | k[3] ^= s_box(k[28]); |
| ubhat | 2:d119a85c793c | 788 | *rc = f2( *rc ); |
| ubhat | 2:d119a85c793c | 789 | |
| ubhat | 2:d119a85c793c | 790 | for(cc = 4; cc < 16; cc += 4) |
| ubhat | 2:d119a85c793c | 791 | { |
| ubhat | 2:d119a85c793c | 792 | k[cc + 0] ^= k[cc - 4]; |
| ubhat | 2:d119a85c793c | 793 | k[cc + 1] ^= k[cc - 3]; |
| ubhat | 2:d119a85c793c | 794 | k[cc + 2] ^= k[cc - 2]; |
| ubhat | 2:d119a85c793c | 795 | k[cc + 3] ^= k[cc - 1]; |
| ubhat | 2:d119a85c793c | 796 | } |
| ubhat | 2:d119a85c793c | 797 | |
| ubhat | 2:d119a85c793c | 798 | k[16] ^= s_box(k[12]); |
| ubhat | 2:d119a85c793c | 799 | k[17] ^= s_box(k[13]); |
| ubhat | 2:d119a85c793c | 800 | k[18] ^= s_box(k[14]); |
| ubhat | 2:d119a85c793c | 801 | k[19] ^= s_box(k[15]); |
| ubhat | 2:d119a85c793c | 802 | |
| ubhat | 2:d119a85c793c | 803 | for( cc = 20; cc < 32; cc += 4 ) |
| ubhat | 2:d119a85c793c | 804 | { |
| ubhat | 2:d119a85c793c | 805 | k[cc + 0] ^= k[cc - 4]; |
| ubhat | 2:d119a85c793c | 806 | k[cc + 1] ^= k[cc - 3]; |
| ubhat | 2:d119a85c793c | 807 | k[cc + 2] ^= k[cc - 2]; |
| ubhat | 2:d119a85c793c | 808 | k[cc + 3] ^= k[cc - 1]; |
| ubhat | 2:d119a85c793c | 809 | } |
| ubhat | 2:d119a85c793c | 810 | } |
| ubhat | 2:d119a85c793c | 811 | |
| ubhat | 2:d119a85c793c | 812 | /* Encrypt a single block of 16 bytes with 'on the fly' 256 bit keying */ |
| ubhat | 2:d119a85c793c | 813 | |
| ubhat | 2:d119a85c793c | 814 | void aes_encrypt_256( const uint8_t in[N_BLOCK], uint8_t out[N_BLOCK], |
| ubhat | 2:d119a85c793c | 815 | const uint8_t key[2 * N_BLOCK], uint8_t o_key[2 * N_BLOCK] ) |
| ubhat | 2:d119a85c793c | 816 | { |
| ubhat | 2:d119a85c793c | 817 | uint8_t s1[N_BLOCK], r, rc = 1; |
| ubhat | 2:d119a85c793c | 818 | if(o_key != key) |
| ubhat | 2:d119a85c793c | 819 | { |
| ubhat | 2:d119a85c793c | 820 | block_copy( o_key, key ); |
| ubhat | 2:d119a85c793c | 821 | block_copy( o_key + 16, key + 16 ); |
| ubhat | 2:d119a85c793c | 822 | } |
| ubhat | 2:d119a85c793c | 823 | copy_and_key( s1, in, o_key ); |
| ubhat | 2:d119a85c793c | 824 | |
| ubhat | 2:d119a85c793c | 825 | for( r = 1 ; r < 14 ; ++r ) |
| ubhat | 2:d119a85c793c | 826 | #if defined( VERSION_1 ) |
| ubhat | 2:d119a85c793c | 827 | { |
| ubhat | 2:d119a85c793c | 828 | mix_sub_columns(s1); |
| ubhat | 2:d119a85c793c | 829 | if( r & 1 ) |
| ubhat | 2:d119a85c793c | 830 | add_round_key( s1, o_key + 16 ); |
| ubhat | 2:d119a85c793c | 831 | else |
| ubhat | 2:d119a85c793c | 832 | { |
| ubhat | 2:d119a85c793c | 833 | update_encrypt_key_256( o_key, &rc ); |
| ubhat | 2:d119a85c793c | 834 | add_round_key( s1, o_key ); |
| ubhat | 2:d119a85c793c | 835 | } |
| ubhat | 2:d119a85c793c | 836 | } |
| ubhat | 2:d119a85c793c | 837 | #else |
| ubhat | 2:d119a85c793c | 838 | { uint8_t s2[N_BLOCK]; |
| ubhat | 2:d119a85c793c | 839 | mix_sub_columns( s2, s1 ); |
| ubhat | 2:d119a85c793c | 840 | if( r & 1 ) |
| ubhat | 2:d119a85c793c | 841 | copy_and_key( s1, s2, o_key + 16 ); |
| ubhat | 2:d119a85c793c | 842 | else |
| ubhat | 2:d119a85c793c | 843 | { |
| ubhat | 2:d119a85c793c | 844 | update_encrypt_key_256( o_key, &rc ); |
| ubhat | 2:d119a85c793c | 845 | copy_and_key( s1, s2, o_key ); |
| ubhat | 2:d119a85c793c | 846 | } |
| ubhat | 2:d119a85c793c | 847 | } |
| ubhat | 2:d119a85c793c | 848 | #endif |
| ubhat | 2:d119a85c793c | 849 | |
| ubhat | 2:d119a85c793c | 850 | shift_sub_rows( s1 ); |
| ubhat | 2:d119a85c793c | 851 | update_encrypt_key_256( o_key, &rc ); |
| ubhat | 2:d119a85c793c | 852 | copy_and_key( out, s1, o_key ); |
| ubhat | 2:d119a85c793c | 853 | } |
| ubhat | 2:d119a85c793c | 854 | |
| ubhat | 2:d119a85c793c | 855 | #endif |
| ubhat | 2:d119a85c793c | 856 | |
| ubhat | 2:d119a85c793c | 857 | #if defined( AES_DEC_256_OTFK ) |
| ubhat | 2:d119a85c793c | 858 | |
| ubhat | 2:d119a85c793c | 859 | /* The 'on the fly' encryption key update for for 256 bit keys */ |
| ubhat | 2:d119a85c793c | 860 | |
| ubhat | 2:d119a85c793c | 861 | static void update_decrypt_key_256( uint8_t k[2 * N_BLOCK], uint8_t *rc ) |
| ubhat | 2:d119a85c793c | 862 | { uint8_t cc; |
| ubhat | 2:d119a85c793c | 863 | |
| ubhat | 2:d119a85c793c | 864 | for(cc = 28; cc > 16; cc -= 4) |
| ubhat | 2:d119a85c793c | 865 | { |
| ubhat | 2:d119a85c793c | 866 | k[cc + 0] ^= k[cc - 4]; |
| ubhat | 2:d119a85c793c | 867 | k[cc + 1] ^= k[cc - 3]; |
| ubhat | 2:d119a85c793c | 868 | k[cc + 2] ^= k[cc - 2]; |
| ubhat | 2:d119a85c793c | 869 | k[cc + 3] ^= k[cc - 1]; |
| ubhat | 2:d119a85c793c | 870 | } |
| ubhat | 2:d119a85c793c | 871 | |
| ubhat | 2:d119a85c793c | 872 | k[16] ^= s_box(k[12]); |
| ubhat | 2:d119a85c793c | 873 | k[17] ^= s_box(k[13]); |
| ubhat | 2:d119a85c793c | 874 | k[18] ^= s_box(k[14]); |
| ubhat | 2:d119a85c793c | 875 | k[19] ^= s_box(k[15]); |
| ubhat | 2:d119a85c793c | 876 | |
| ubhat | 2:d119a85c793c | 877 | for(cc = 12; cc > 0; cc -= 4) |
| ubhat | 2:d119a85c793c | 878 | { |
| ubhat | 2:d119a85c793c | 879 | k[cc + 0] ^= k[cc - 4]; |
| ubhat | 2:d119a85c793c | 880 | k[cc + 1] ^= k[cc - 3]; |
| ubhat | 2:d119a85c793c | 881 | k[cc + 2] ^= k[cc - 2]; |
| ubhat | 2:d119a85c793c | 882 | k[cc + 3] ^= k[cc - 1]; |
| ubhat | 2:d119a85c793c | 883 | } |
| ubhat | 2:d119a85c793c | 884 | |
| ubhat | 2:d119a85c793c | 885 | *rc = d2(*rc); |
| ubhat | 2:d119a85c793c | 886 | k[0] ^= s_box(k[29]) ^ *rc; |
| ubhat | 2:d119a85c793c | 887 | k[1] ^= s_box(k[30]); |
| ubhat | 2:d119a85c793c | 888 | k[2] ^= s_box(k[31]); |
| ubhat | 2:d119a85c793c | 889 | k[3] ^= s_box(k[28]); |
| ubhat | 2:d119a85c793c | 890 | } |
| ubhat | 2:d119a85c793c | 891 | |
| ubhat | 2:d119a85c793c | 892 | /* Decrypt a single block of 16 bytes with 'on the fly' |
| ubhat | 2:d119a85c793c | 893 | 256 bit keying |
| ubhat | 2:d119a85c793c | 894 | */ |
| ubhat | 2:d119a85c793c | 895 | void aes_decrypt_256( const uint8_t in[N_BLOCK], uint8_t out[N_BLOCK], |
| ubhat | 2:d119a85c793c | 896 | const uint8_t key[2 * N_BLOCK], uint8_t o_key[2 * N_BLOCK] ) |
| ubhat | 2:d119a85c793c | 897 | { |
| ubhat | 2:d119a85c793c | 898 | uint8_t s1[N_BLOCK], r, rc = 0x80; |
| ubhat | 2:d119a85c793c | 899 | |
| ubhat | 2:d119a85c793c | 900 | if(o_key != key) |
| ubhat | 2:d119a85c793c | 901 | { |
| ubhat | 2:d119a85c793c | 902 | block_copy( o_key, key ); |
| ubhat | 2:d119a85c793c | 903 | block_copy( o_key + 16, key + 16 ); |
| ubhat | 2:d119a85c793c | 904 | } |
| ubhat | 2:d119a85c793c | 905 | |
| ubhat | 2:d119a85c793c | 906 | copy_and_key( s1, in, o_key ); |
| ubhat | 2:d119a85c793c | 907 | inv_shift_sub_rows( s1 ); |
| ubhat | 2:d119a85c793c | 908 | |
| ubhat | 2:d119a85c793c | 909 | for( r = 14 ; --r ; ) |
| ubhat | 2:d119a85c793c | 910 | #if defined( VERSION_1 ) |
| ubhat | 2:d119a85c793c | 911 | { |
| ubhat | 2:d119a85c793c | 912 | if( ( r & 1 ) ) |
| ubhat | 2:d119a85c793c | 913 | { |
| ubhat | 2:d119a85c793c | 914 | update_decrypt_key_256( o_key, &rc ); |
| ubhat | 2:d119a85c793c | 915 | add_round_key( s1, o_key + 16 ); |
| ubhat | 2:d119a85c793c | 916 | } |
| ubhat | 2:d119a85c793c | 917 | else |
| ubhat | 2:d119a85c793c | 918 | add_round_key( s1, o_key ); |
| ubhat | 2:d119a85c793c | 919 | inv_mix_sub_columns( s1 ); |
| ubhat | 2:d119a85c793c | 920 | } |
| ubhat | 2:d119a85c793c | 921 | #else |
| ubhat | 2:d119a85c793c | 922 | { uint8_t s2[N_BLOCK]; |
| ubhat | 2:d119a85c793c | 923 | if( ( r & 1 ) ) |
| ubhat | 2:d119a85c793c | 924 | { |
| ubhat | 2:d119a85c793c | 925 | update_decrypt_key_256( o_key, &rc ); |
| ubhat | 2:d119a85c793c | 926 | copy_and_key( s2, s1, o_key + 16 ); |
| ubhat | 2:d119a85c793c | 927 | } |
| ubhat | 2:d119a85c793c | 928 | else |
| ubhat | 2:d119a85c793c | 929 | copy_and_key( s2, s1, o_key ); |
| ubhat | 2:d119a85c793c | 930 | inv_mix_sub_columns( s1, s2 ); |
| ubhat | 2:d119a85c793c | 931 | } |
| ubhat | 2:d119a85c793c | 932 | #endif |
| ubhat | 2:d119a85c793c | 933 | copy_and_key( out, s1, o_key ); |
| ubhat | 2:d119a85c793c | 934 | } |
| ubhat | 2:d119a85c793c | 935 | |
| ubhat | 2:d119a85c793c | 936 | #endif |