Small Internet Protocol Stack using a standard serial port.
PPP-Blinky - TCP/IP Networking Over a Serial Port
Note: The source code is at the bottom of this page.

A Windows desktop showing PPP-Blinky in the network connections list.
Describe PPP-Blinky in Three Sentences
PPP-Blinky is a tiny library that enables Internet protocols (IPv4) to any mbed target hardware by using only a serial port.
The code runs on processors with as little as 8k RAM, for example the Nucleo-L053R8 board.
PPP-Blinky uses the industry-standard PPP (Point-to-Point) Protocol and a tiny "stateless" TCP/IP stack.
No Ethernet Port Required
No ethernet port is required - PPP-Blinky uses a serial port to send IP packets to your PC.
PPP-Blinky emulates a standard dial-up modem and therefore connects to Windows, Linux or Adroid machines.
The code runs on most ARM mbed platforms such as the LPC11U24 shown in the picture below:
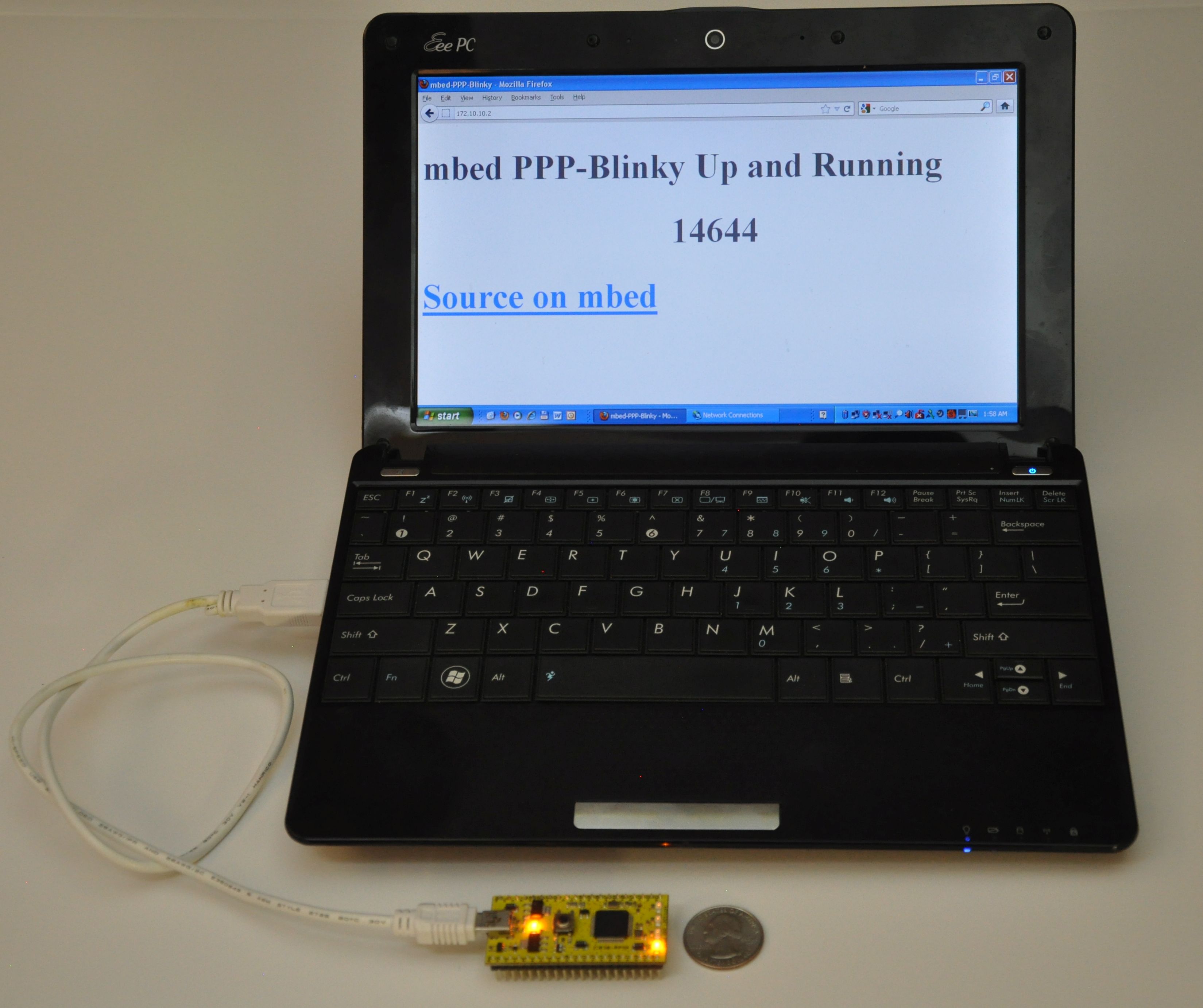 mbed LPC11u24 acting as a webserver to a Windows laptop.
mbed LPC11u24 acting as a webserver to a Windows laptop.
Webserver
The Webserver and WebSocket functions are ideal for building browser-based GUIs on mbed-enabled hardware.
PPP-Blinky's HTTP webserver works with most web clients such as Internet Explorer, Mozilla Firefox, Google Chrome, Safari, Curl, wget and Lynx as well as Microsoft Powershell Invoke-Webrequest command.
In the image below Firefox web browser displays the main web page embedded into PPP-Blinky's code:
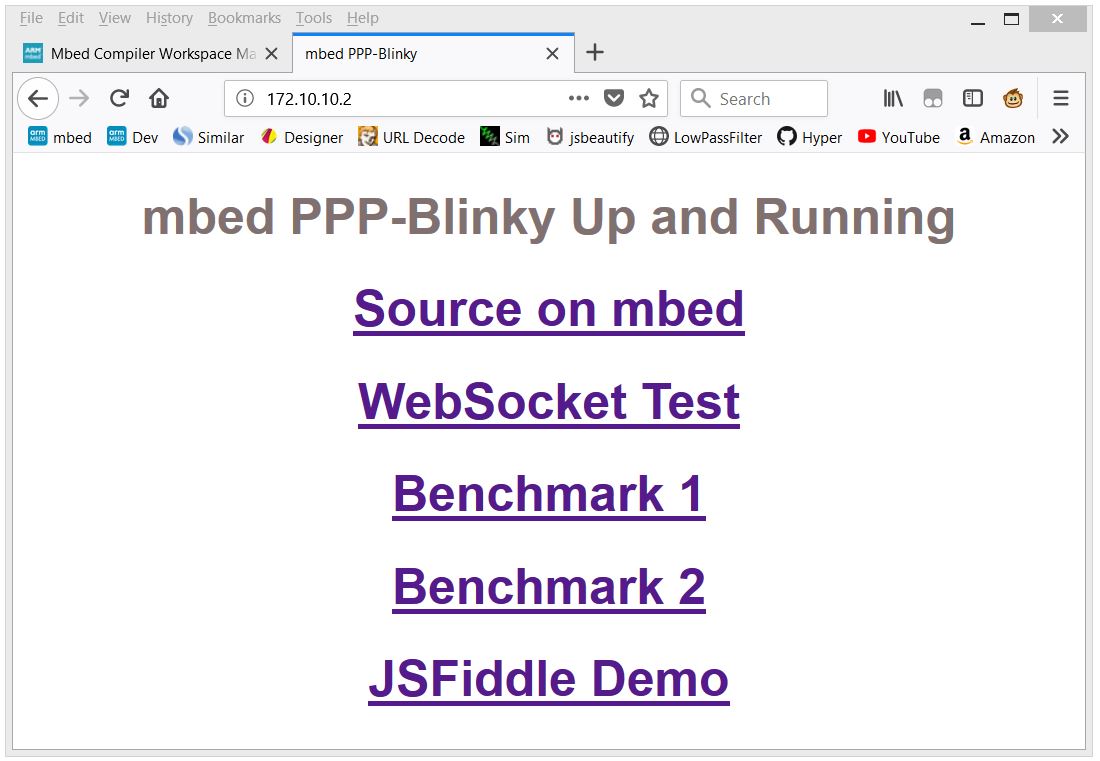 Firefox web browser displays a web page embedded into PPP-Blinky's code
Firefox web browser displays a web page embedded into PPP-Blinky's code
WebSocket Service
WebSocket is the most popular protocol standard for real-time bidirectional TCP/IP communication between clients and servers.
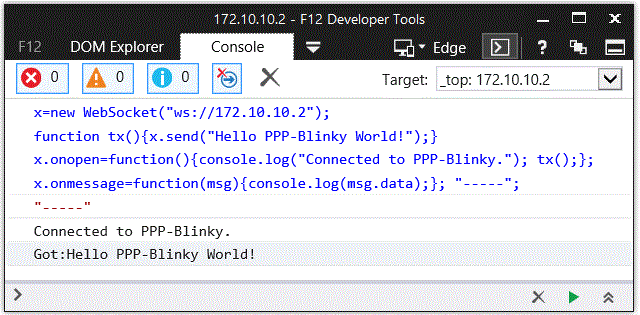
In the image below a small Internet Explorer script has connected to PPP-Blinky's WebSocket Service.
A websocket message was then sent by the browser and was echoed back by the WebSocket, triggering the onmessage event in the script.
The WebSocket service enables bidirectional real-time interaction between PPP-Blinky and any element in the browser DOM via JavaScript.
If you already have PPP-Blinky up and running you can test your WebSocket service using this: http://jsfiddle.net/d26cyuh2/112/embedded/result
Websockets are ideal for building browser-based GUIs for mbed hardware.
Trying PPP-Blinky on your mbed board
You will need an mbed-enabled hardware board: https://developer.mbed.org/platforms/
Establish a serial port connection between your host PC and your mbed board.
The easiest way is to use mbed hardware with a USB serial debug port. I've tried the ST-Micro Nucleo-L476RG, Nucleo-L152RE, Nucleo-F401RE, Nucleo-L432KC, Nucleo-L053R8, mbed-LPC11U24 and mbed-LPC1768 boards and they all work out of the box. Use the mbed online compiler to compile the software for your target board. Save the compiled binary to your hardware.
Before establishing a network connection, you can verify the operation of the code by opening a terminal program such as Tera Term, and setting the baud rate of the COM port on your mbed board to 115200 baud. LED1 should toggle for every two 0x7E (~) (i.e. tilde) characters you type, as 0x7E is the PPP frame start/end marker. Don't forget to close the port when your'e done testing, or else Windows Dial-up Networking will report that the COM port is in use by another program when you try to connect.
Once you are certain that the serial port and firmware is working, proceed to creating a new network connection on your PC -see below.
Creating a Dial-up Connection in Windows
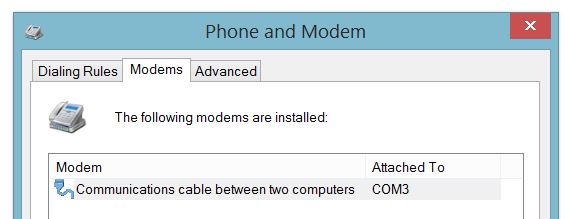
Setting up Dial-Up Networking (DUN) on your Windows 7 or 8 PC is essentially a two-step process: First, you create a new modem device, because PPP-blinky partially emulates a standard Windows serial port modem device. Second, you create a new Internet connection (in practice, a new network adapter) which is associated with your new "modem".
Step-by-step description of how to configure Windows for PPP-Blinky here:
/users/nixnax/code/PPP-Blinky/wiki/Configuring-Windows-Dial-Up-Networking
There is also a screen on how to set up Linux dial-up networking near the bottom of this page.
Connecting to PPP-Blinky from your PC
Once Windows networking is configured you can establish a dial-up connection to your mbed board over the USB virtual com port.
The IP address you manually assigned to the new dial-up network adapter (172.10.10.1) functions as a gateway to any valid IP address on that subnet. In the screen capture below, I'm sending pings from the Windows 8 command line to my ST-Micro Nucleo-L476RG board over the USB virtual serial Port. I'm also using a second serial port and Tera Term to capture the debug output from a second serial port on the hardware. The optional debug output from the board prints out the IP source and destination address and the first few bytes of the data payload. Note that the source is the adapter IP address, (172.10.10.1 in this case) and the destination is some other address on that subnet - all packets to the subnet are sent to our mbed hardware. For example, you could also ping 172.10.10.123 or, if your PPP-Blinky is running, simply click on this link: http://172.10.10.123
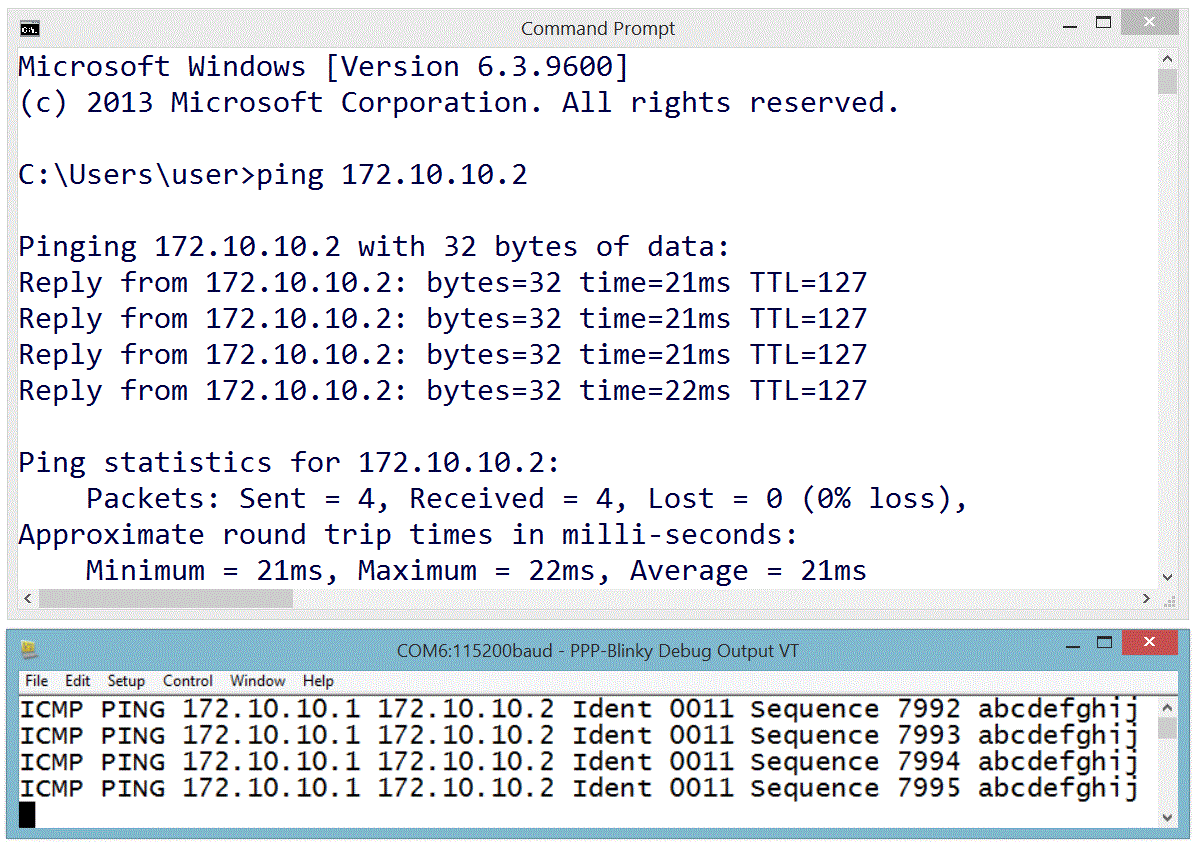
One Million Pings!
In the image below the ICMP ("ping") echo reply service was tested by sending one million pings to ppp-Blinky. This took over two hours.
The ping tool used on the Windows 8 PC was psping.exe from PsTools by Mark Russinovich - http://bit.ly/PingFast
The average reply time for a short ping (1 byte of payload data) was 11 milliseconds at 115200 baud on the $10 Nucleo-L053R8 board - barely enough time for 130 bytes to be sent over the port!
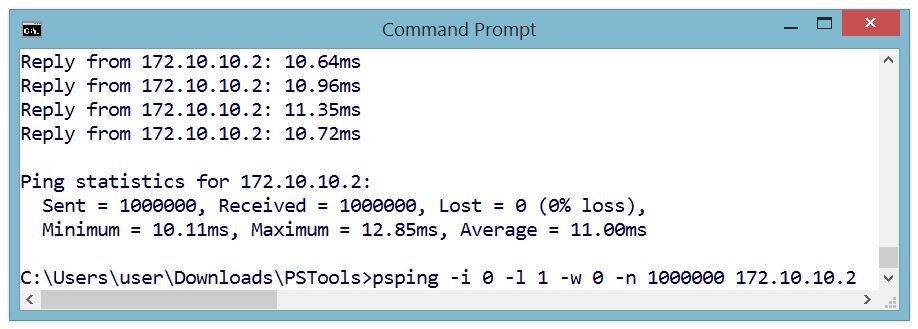
Monitoring PPP-Blinky Packets
The image below is from a Microsoft Network Monitor 3.4 capture session.
Responses from PPP-Blinky are shown in blue.
Frame 2 - Internet Explorer at IP 172.10.10.1 (the Dial-Up Adapter IP) requests a TCP connection by sending an S (SYN) flag.
Frame 3 - PPP-Blinky at IP 172.10.10.2 responds with an ACK in frame 3. One direction of the link is now established.
Frame 4 - The PC acknowledges the SYN sent by PPP-Blinky in frame 3. The TCP link is now fully established.
Frame 5 - The browser "pushes" (P flag is set) an HTTP GET request to PPP-Blinky.
Frame 6 - PPP-Blinky responds with a standard HTTP response "pushes" (P flag set) back a small web page. It also sets the A (ACK) flag to acknowledge the message sent in frame 6.
Frame 7 - The PC acknowledges reception of the HTTP payload.
Frame 8 - The PC starts to shut down the TCP connection by sending a FIN flag.
Frame 9 - PPP-Blinky acknowledges the FIN request - the connection is now closed in one direction. It also sets a FIN flag in the response to request closure of the opposite direction of the connection.
Frame 10 - The PC acknowledges the FIN request. The closing of the TCP connection is now confirmed in both directions.
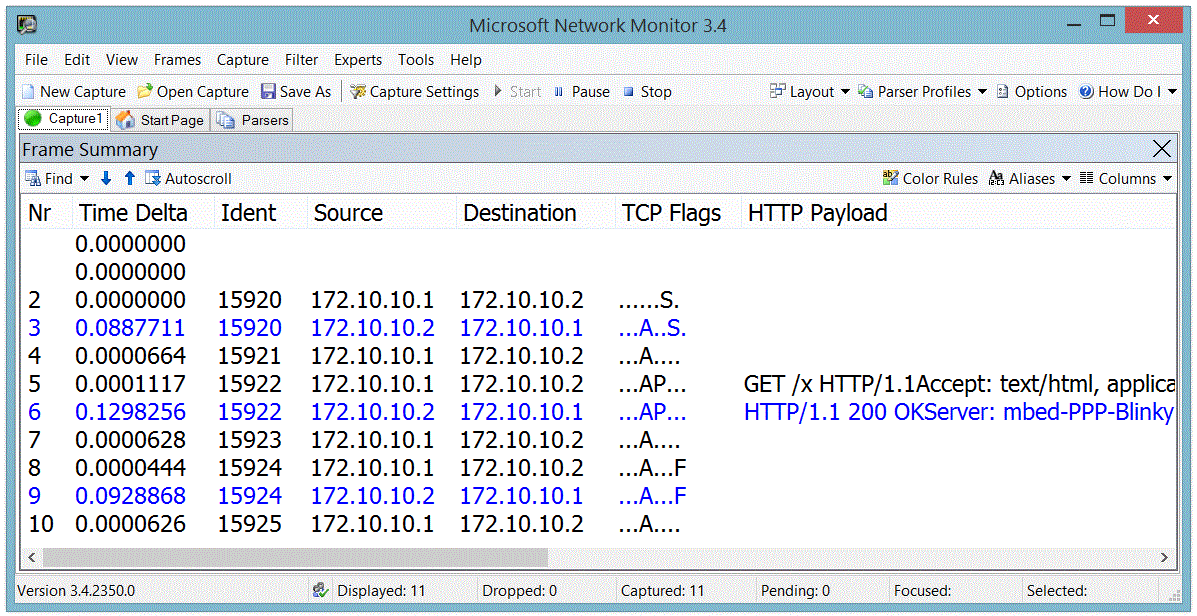
Debug Output
PPP-Blinky can output handy debug information to an optional second serial port.
The image below shows the debug output (Ident, Source, Destination, TCP Flags) for a complete HTTP conversation.
The PC messages are displayed in black. PPP-Blinky messages are blue.
Notice how PPP-blinky automatically inserts a blank line after each full HTTP conversation.
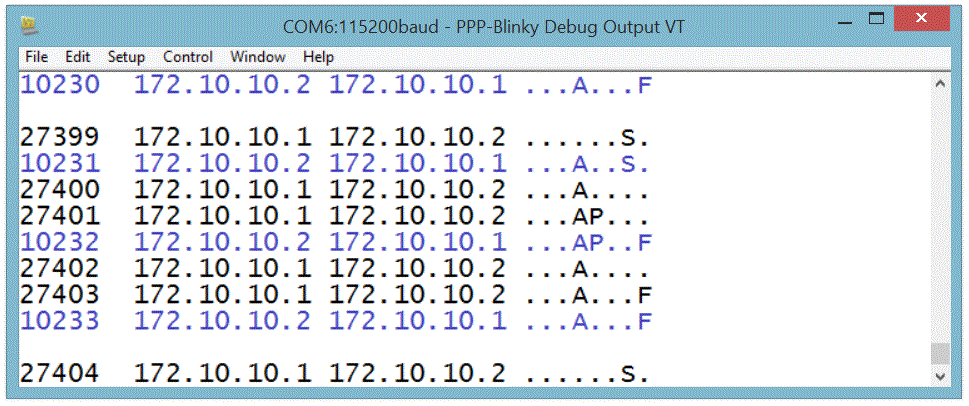
Creating a Dial-Up Connection in Linux
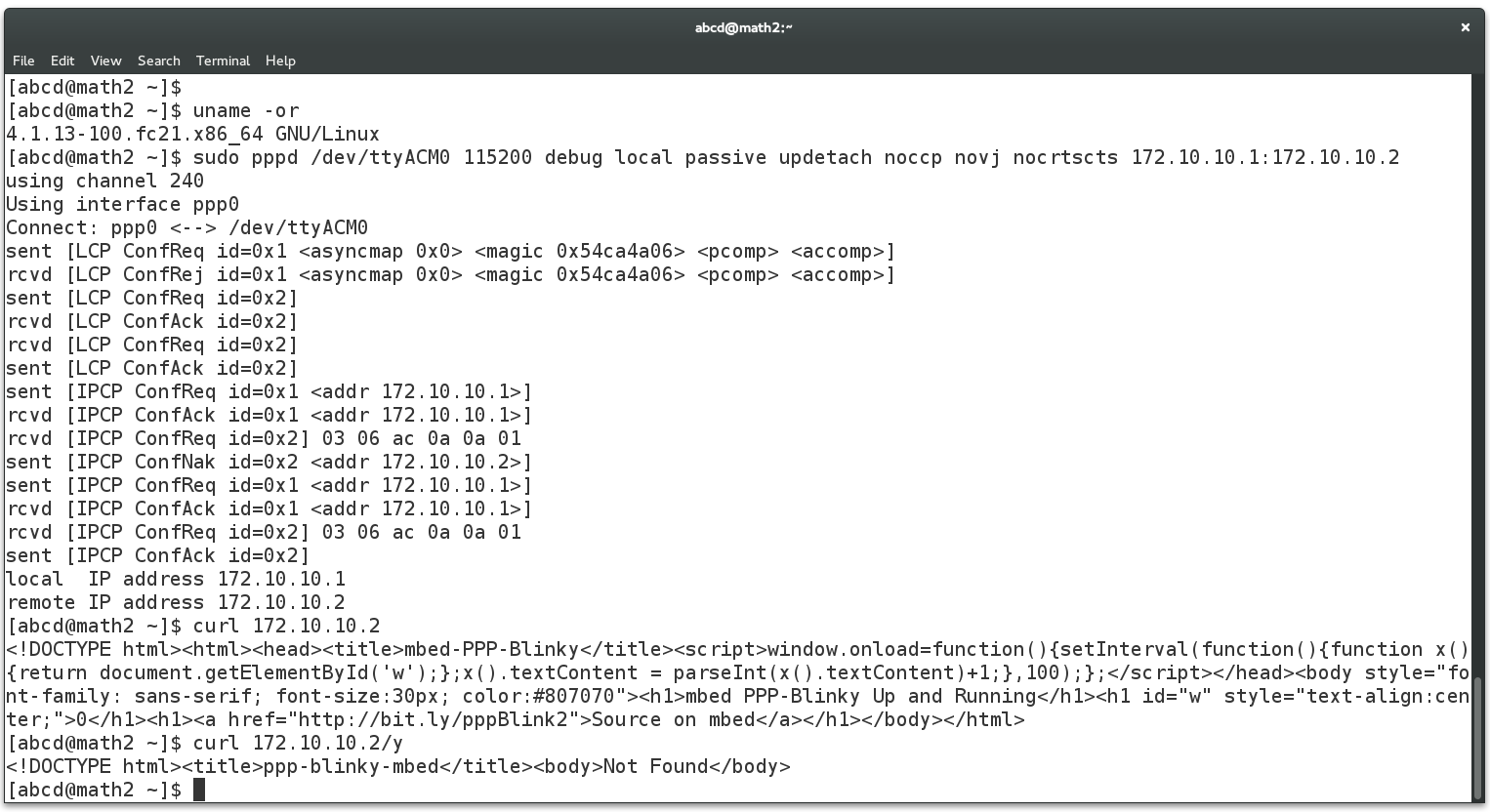
The screen below shows the required pppd command to connect to PPP-Blinky from a Linux machine. This was much simpler than Windows! The USB serial port of the mbed LPC1768 board registered as /dev/ttyACM0 on my Linux box. Do a websearch on pppd if you want to learn more about pppd, the Linux PPP handler. Near the bottom of the screen below, two webpages are fetched (/ and /y) by using the curl command on the command line. Gnome Webkit and Firefox work fine, too. Also try echo GET / HTTP/1.1 | nc 172.10.10.2 which uses netcat, the "Swiss army knife" of networking tools. PPP-Blinky was also tested with ApacheBench, the Apache server benchmark software. After 100000 fetches, the mean page fetch rate was reported as 6 page fetches per second for a small page.
Caveats
PPP Blinky is an extremely sparse implementation (1.5k lines) of HTTP,WebSocket,TCP, UDP, ICMP, IPCP and LCP over PPP, requiring around 8kB of RAM. The minimum functionality required to establish connectivity is implemented. These are often acceptable tradeoffs for embedded projects as well as a handy tool to learn the practical details of everyday networking implementations.
SHA1/sha1.cpp@228:7fb878500862, 2018-09-17 (annotated)
- Committer:
- nixnax
- Date:
- Mon Sep 17 03:38:27 2018 +0000
- Revision:
- 228:7fb878500862
- Parent:
- 132:09b66cc5cf4a
removed LCPConfigurationRequest()
Who changed what in which revision?
| User | Revision | Line number | New contents of line |
|---|---|---|---|
| nixnax | 128:e5958d143e9d | 1 | /* |
| nixnax | 128:e5958d143e9d | 2 | SHA-1 in C |
| nixnax | 128:e5958d143e9d | 3 | By Steve Reid <steve@edmweb.com> |
| nixnax | 128:e5958d143e9d | 4 | 100% Public Domain |
| nixnax | 128:e5958d143e9d | 5 | */ |
| nixnax | 128:e5958d143e9d | 6 | |
| nixnax | 128:e5958d143e9d | 7 | #define SHA1HANDSOFF |
| nixnax | 128:e5958d143e9d | 8 | |
| nixnax | 128:e5958d143e9d | 9 | #include <stdio.h> |
| nixnax | 128:e5958d143e9d | 10 | #include <string.h> |
| nixnax | 128:e5958d143e9d | 11 | |
| nixnax | 128:e5958d143e9d | 12 | /* for uint32_t */ |
| nixnax | 128:e5958d143e9d | 13 | #include <stdint.h> |
| nixnax | 128:e5958d143e9d | 14 | |
| nixnax | 128:e5958d143e9d | 15 | #include "sha1.h" |
| nixnax | 128:e5958d143e9d | 16 | |
| nixnax | 128:e5958d143e9d | 17 | |
| nixnax | 128:e5958d143e9d | 18 | #define rol(value, bits) (((value) << (bits)) | ((value) >> (32 - (bits)))) |
| nixnax | 128:e5958d143e9d | 19 | |
| nixnax | 128:e5958d143e9d | 20 | /* blk0() and blk() perform the initial expand. */ |
| nixnax | 128:e5958d143e9d | 21 | /* I got the idea of expanding during the round function from SSLeay */ |
| nixnax | 128:e5958d143e9d | 22 | #if BYTE_ORDER == LITTLE_ENDIAN |
| nixnax | 128:e5958d143e9d | 23 | #define blk0(i) (block->l[i] = (rol(block->l[i],24)&0xFF00FF00) \ |
| nixnax | 128:e5958d143e9d | 24 | |(rol(block->l[i],8)&0x00FF00FF)) |
| nixnax | 128:e5958d143e9d | 25 | #elif BYTE_ORDER == BIG_ENDIAN |
| nixnax | 128:e5958d143e9d | 26 | #define blk0(i) block->l[i] |
| nixnax | 128:e5958d143e9d | 27 | #else |
| nixnax | 128:e5958d143e9d | 28 | #error "Endianness not defined!" |
| nixnax | 128:e5958d143e9d | 29 | #endif |
| nixnax | 128:e5958d143e9d | 30 | #define blk(i) (block->l[i&15] = rol(block->l[(i+13)&15]^block->l[(i+8)&15] \ |
| nixnax | 128:e5958d143e9d | 31 | ^block->l[(i+2)&15]^block->l[i&15],1)) |
| nixnax | 128:e5958d143e9d | 32 | |
| nixnax | 128:e5958d143e9d | 33 | /* (R0+R1), R2, R3, R4 are the different operations used in SHA1 */ |
| nixnax | 128:e5958d143e9d | 34 | #define R0(v,w,x,y,z,i) z+=((w&(x^y))^y)+blk0(i)+0x5A827999+rol(v,5);w=rol(w,30); |
| nixnax | 128:e5958d143e9d | 35 | #define R1(v,w,x,y,z,i) z+=((w&(x^y))^y)+blk(i)+0x5A827999+rol(v,5);w=rol(w,30); |
| nixnax | 128:e5958d143e9d | 36 | #define R2(v,w,x,y,z,i) z+=(w^x^y)+blk(i)+0x6ED9EBA1+rol(v,5);w=rol(w,30); |
| nixnax | 128:e5958d143e9d | 37 | #define R3(v,w,x,y,z,i) z+=(((w|x)&y)|(w&x))+blk(i)+0x8F1BBCDC+rol(v,5);w=rol(w,30); |
| nixnax | 128:e5958d143e9d | 38 | #define R4(v,w,x,y,z,i) z+=(w^x^y)+blk(i)+0xCA62C1D6+rol(v,5);w=rol(w,30); |
| nixnax | 128:e5958d143e9d | 39 | |
| nixnax | 128:e5958d143e9d | 40 | |
| nixnax | 128:e5958d143e9d | 41 | /* Hash a single 512-bit block. This is the core of the algorithm. */ |
| nixnax | 128:e5958d143e9d | 42 | |
| nixnax | 128:e5958d143e9d | 43 | void SHA1Transform( |
| nixnax | 128:e5958d143e9d | 44 | uint32_t state[5], |
| nixnax | 128:e5958d143e9d | 45 | const unsigned char buffer[64] |
| nixnax | 128:e5958d143e9d | 46 | ) |
| nixnax | 128:e5958d143e9d | 47 | { |
| nixnax | 128:e5958d143e9d | 48 | uint32_t a, b, c, d, e; |
| nixnax | 128:e5958d143e9d | 49 | |
| nixnax | 128:e5958d143e9d | 50 | typedef union |
| nixnax | 128:e5958d143e9d | 51 | { |
| nixnax | 128:e5958d143e9d | 52 | unsigned char c[64]; |
| nixnax | 128:e5958d143e9d | 53 | uint32_t l[16]; |
| nixnax | 128:e5958d143e9d | 54 | } CHAR64LONG16; |
| nixnax | 128:e5958d143e9d | 55 | |
| nixnax | 128:e5958d143e9d | 56 | #ifdef SHA1HANDSOFF |
| nixnax | 128:e5958d143e9d | 57 | CHAR64LONG16 block[1]; /* use array to appear as a pointer */ |
| nixnax | 128:e5958d143e9d | 58 | |
| nixnax | 128:e5958d143e9d | 59 | memcpy(block, buffer, 64); |
| nixnax | 128:e5958d143e9d | 60 | #else |
| nixnax | 128:e5958d143e9d | 61 | /* The following had better never be used because it causes the |
| nixnax | 128:e5958d143e9d | 62 | * pointer-to-const buffer to be cast into a pointer to non-const. |
| nixnax | 128:e5958d143e9d | 63 | * And the result is written through. I threw a "const" in, hoping |
| nixnax | 128:e5958d143e9d | 64 | * this will cause a diagnostic. |
| nixnax | 128:e5958d143e9d | 65 | */ |
| nixnax | 128:e5958d143e9d | 66 | CHAR64LONG16 *block = (const CHAR64LONG16 *) buffer; |
| nixnax | 128:e5958d143e9d | 67 | #endif |
| nixnax | 128:e5958d143e9d | 68 | /* Copy context->state[] to working vars */ |
| nixnax | 128:e5958d143e9d | 69 | a = state[0]; |
| nixnax | 128:e5958d143e9d | 70 | b = state[1]; |
| nixnax | 128:e5958d143e9d | 71 | c = state[2]; |
| nixnax | 128:e5958d143e9d | 72 | d = state[3]; |
| nixnax | 128:e5958d143e9d | 73 | e = state[4]; |
| nixnax | 128:e5958d143e9d | 74 | /* 4 rounds of 20 operations each. Loop unrolled. */ |
| nixnax | 128:e5958d143e9d | 75 | R0(a, b, c, d, e, 0); |
| nixnax | 128:e5958d143e9d | 76 | R0(e, a, b, c, d, 1); |
| nixnax | 128:e5958d143e9d | 77 | R0(d, e, a, b, c, 2); |
| nixnax | 128:e5958d143e9d | 78 | R0(c, d, e, a, b, 3); |
| nixnax | 128:e5958d143e9d | 79 | R0(b, c, d, e, a, 4); |
| nixnax | 128:e5958d143e9d | 80 | R0(a, b, c, d, e, 5); |
| nixnax | 128:e5958d143e9d | 81 | R0(e, a, b, c, d, 6); |
| nixnax | 128:e5958d143e9d | 82 | R0(d, e, a, b, c, 7); |
| nixnax | 128:e5958d143e9d | 83 | R0(c, d, e, a, b, 8); |
| nixnax | 128:e5958d143e9d | 84 | R0(b, c, d, e, a, 9); |
| nixnax | 128:e5958d143e9d | 85 | R0(a, b, c, d, e, 10); |
| nixnax | 128:e5958d143e9d | 86 | R0(e, a, b, c, d, 11); |
| nixnax | 128:e5958d143e9d | 87 | R0(d, e, a, b, c, 12); |
| nixnax | 128:e5958d143e9d | 88 | R0(c, d, e, a, b, 13); |
| nixnax | 128:e5958d143e9d | 89 | R0(b, c, d, e, a, 14); |
| nixnax | 128:e5958d143e9d | 90 | R0(a, b, c, d, e, 15); |
| nixnax | 128:e5958d143e9d | 91 | R1(e, a, b, c, d, 16); |
| nixnax | 128:e5958d143e9d | 92 | R1(d, e, a, b, c, 17); |
| nixnax | 128:e5958d143e9d | 93 | R1(c, d, e, a, b, 18); |
| nixnax | 128:e5958d143e9d | 94 | R1(b, c, d, e, a, 19); |
| nixnax | 128:e5958d143e9d | 95 | R2(a, b, c, d, e, 20); |
| nixnax | 128:e5958d143e9d | 96 | R2(e, a, b, c, d, 21); |
| nixnax | 128:e5958d143e9d | 97 | R2(d, e, a, b, c, 22); |
| nixnax | 128:e5958d143e9d | 98 | R2(c, d, e, a, b, 23); |
| nixnax | 128:e5958d143e9d | 99 | R2(b, c, d, e, a, 24); |
| nixnax | 128:e5958d143e9d | 100 | R2(a, b, c, d, e, 25); |
| nixnax | 128:e5958d143e9d | 101 | R2(e, a, b, c, d, 26); |
| nixnax | 128:e5958d143e9d | 102 | R2(d, e, a, b, c, 27); |
| nixnax | 128:e5958d143e9d | 103 | R2(c, d, e, a, b, 28); |
| nixnax | 128:e5958d143e9d | 104 | R2(b, c, d, e, a, 29); |
| nixnax | 128:e5958d143e9d | 105 | R2(a, b, c, d, e, 30); |
| nixnax | 128:e5958d143e9d | 106 | R2(e, a, b, c, d, 31); |
| nixnax | 128:e5958d143e9d | 107 | R2(d, e, a, b, c, 32); |
| nixnax | 128:e5958d143e9d | 108 | R2(c, d, e, a, b, 33); |
| nixnax | 128:e5958d143e9d | 109 | R2(b, c, d, e, a, 34); |
| nixnax | 128:e5958d143e9d | 110 | R2(a, b, c, d, e, 35); |
| nixnax | 128:e5958d143e9d | 111 | R2(e, a, b, c, d, 36); |
| nixnax | 128:e5958d143e9d | 112 | R2(d, e, a, b, c, 37); |
| nixnax | 128:e5958d143e9d | 113 | R2(c, d, e, a, b, 38); |
| nixnax | 128:e5958d143e9d | 114 | R2(b, c, d, e, a, 39); |
| nixnax | 128:e5958d143e9d | 115 | R3(a, b, c, d, e, 40); |
| nixnax | 128:e5958d143e9d | 116 | R3(e, a, b, c, d, 41); |
| nixnax | 128:e5958d143e9d | 117 | R3(d, e, a, b, c, 42); |
| nixnax | 128:e5958d143e9d | 118 | R3(c, d, e, a, b, 43); |
| nixnax | 128:e5958d143e9d | 119 | R3(b, c, d, e, a, 44); |
| nixnax | 128:e5958d143e9d | 120 | R3(a, b, c, d, e, 45); |
| nixnax | 128:e5958d143e9d | 121 | R3(e, a, b, c, d, 46); |
| nixnax | 128:e5958d143e9d | 122 | R3(d, e, a, b, c, 47); |
| nixnax | 128:e5958d143e9d | 123 | R3(c, d, e, a, b, 48); |
| nixnax | 128:e5958d143e9d | 124 | R3(b, c, d, e, a, 49); |
| nixnax | 128:e5958d143e9d | 125 | R3(a, b, c, d, e, 50); |
| nixnax | 128:e5958d143e9d | 126 | R3(e, a, b, c, d, 51); |
| nixnax | 128:e5958d143e9d | 127 | R3(d, e, a, b, c, 52); |
| nixnax | 128:e5958d143e9d | 128 | R3(c, d, e, a, b, 53); |
| nixnax | 128:e5958d143e9d | 129 | R3(b, c, d, e, a, 54); |
| nixnax | 128:e5958d143e9d | 130 | R3(a, b, c, d, e, 55); |
| nixnax | 128:e5958d143e9d | 131 | R3(e, a, b, c, d, 56); |
| nixnax | 128:e5958d143e9d | 132 | R3(d, e, a, b, c, 57); |
| nixnax | 128:e5958d143e9d | 133 | R3(c, d, e, a, b, 58); |
| nixnax | 128:e5958d143e9d | 134 | R3(b, c, d, e, a, 59); |
| nixnax | 128:e5958d143e9d | 135 | R4(a, b, c, d, e, 60); |
| nixnax | 128:e5958d143e9d | 136 | R4(e, a, b, c, d, 61); |
| nixnax | 128:e5958d143e9d | 137 | R4(d, e, a, b, c, 62); |
| nixnax | 128:e5958d143e9d | 138 | R4(c, d, e, a, b, 63); |
| nixnax | 128:e5958d143e9d | 139 | R4(b, c, d, e, a, 64); |
| nixnax | 128:e5958d143e9d | 140 | R4(a, b, c, d, e, 65); |
| nixnax | 128:e5958d143e9d | 141 | R4(e, a, b, c, d, 66); |
| nixnax | 128:e5958d143e9d | 142 | R4(d, e, a, b, c, 67); |
| nixnax | 128:e5958d143e9d | 143 | R4(c, d, e, a, b, 68); |
| nixnax | 128:e5958d143e9d | 144 | R4(b, c, d, e, a, 69); |
| nixnax | 128:e5958d143e9d | 145 | R4(a, b, c, d, e, 70); |
| nixnax | 128:e5958d143e9d | 146 | R4(e, a, b, c, d, 71); |
| nixnax | 128:e5958d143e9d | 147 | R4(d, e, a, b, c, 72); |
| nixnax | 128:e5958d143e9d | 148 | R4(c, d, e, a, b, 73); |
| nixnax | 128:e5958d143e9d | 149 | R4(b, c, d, e, a, 74); |
| nixnax | 128:e5958d143e9d | 150 | R4(a, b, c, d, e, 75); |
| nixnax | 128:e5958d143e9d | 151 | R4(e, a, b, c, d, 76); |
| nixnax | 128:e5958d143e9d | 152 | R4(d, e, a, b, c, 77); |
| nixnax | 128:e5958d143e9d | 153 | R4(c, d, e, a, b, 78); |
| nixnax | 128:e5958d143e9d | 154 | R4(b, c, d, e, a, 79); |
| nixnax | 128:e5958d143e9d | 155 | /* Add the working vars back into context.state[] */ |
| nixnax | 128:e5958d143e9d | 156 | state[0] += a; |
| nixnax | 128:e5958d143e9d | 157 | state[1] += b; |
| nixnax | 128:e5958d143e9d | 158 | state[2] += c; |
| nixnax | 128:e5958d143e9d | 159 | state[3] += d; |
| nixnax | 128:e5958d143e9d | 160 | state[4] += e; |
| nixnax | 128:e5958d143e9d | 161 | /* Wipe variables */ |
| nixnax | 128:e5958d143e9d | 162 | a = b = c = d = e = 0; |
| nixnax | 128:e5958d143e9d | 163 | #ifdef SHA1HANDSOFF |
| nixnax | 128:e5958d143e9d | 164 | memset(block, '\0', sizeof(block)); |
| nixnax | 128:e5958d143e9d | 165 | #endif |
| nixnax | 128:e5958d143e9d | 166 | } |
| nixnax | 128:e5958d143e9d | 167 | |
| nixnax | 128:e5958d143e9d | 168 | |
| nixnax | 128:e5958d143e9d | 169 | /* SHA1Init - Initialize new context */ |
| nixnax | 128:e5958d143e9d | 170 | |
| nixnax | 128:e5958d143e9d | 171 | void SHA1Init( |
| nixnax | 128:e5958d143e9d | 172 | SHA1_CTX * context |
| nixnax | 128:e5958d143e9d | 173 | ) |
| nixnax | 128:e5958d143e9d | 174 | { |
| nixnax | 128:e5958d143e9d | 175 | /* SHA1 initialization constants */ |
| nixnax | 128:e5958d143e9d | 176 | context->state[0] = 0x67452301; |
| nixnax | 128:e5958d143e9d | 177 | context->state[1] = 0xEFCDAB89; |
| nixnax | 128:e5958d143e9d | 178 | context->state[2] = 0x98BADCFE; |
| nixnax | 128:e5958d143e9d | 179 | context->state[3] = 0x10325476; |
| nixnax | 128:e5958d143e9d | 180 | context->state[4] = 0xC3D2E1F0; |
| nixnax | 128:e5958d143e9d | 181 | context->count[0] = context->count[1] = 0; |
| nixnax | 128:e5958d143e9d | 182 | } |
| nixnax | 128:e5958d143e9d | 183 | |
| nixnax | 128:e5958d143e9d | 184 | |
| nixnax | 128:e5958d143e9d | 185 | /* Run your data through this. */ |
| nixnax | 128:e5958d143e9d | 186 | |
| nixnax | 128:e5958d143e9d | 187 | void SHA1Update( |
| nixnax | 128:e5958d143e9d | 188 | SHA1_CTX * context, |
| nixnax | 128:e5958d143e9d | 189 | const unsigned char *data, |
| nixnax | 128:e5958d143e9d | 190 | uint32_t len |
| nixnax | 128:e5958d143e9d | 191 | ) |
| nixnax | 128:e5958d143e9d | 192 | { |
| nixnax | 128:e5958d143e9d | 193 | uint32_t i; |
| nixnax | 128:e5958d143e9d | 194 | |
| nixnax | 128:e5958d143e9d | 195 | uint32_t j; |
| nixnax | 128:e5958d143e9d | 196 | |
| nixnax | 128:e5958d143e9d | 197 | j = context->count[0]; |
| nixnax | 128:e5958d143e9d | 198 | if ((context->count[0] += len << 3) < j) |
| nixnax | 128:e5958d143e9d | 199 | context->count[1]++; |
| nixnax | 128:e5958d143e9d | 200 | context->count[1] += (len >> 29); |
| nixnax | 128:e5958d143e9d | 201 | j = (j >> 3) & 63; |
| nixnax | 128:e5958d143e9d | 202 | if ((j + len) > 63) |
| nixnax | 128:e5958d143e9d | 203 | { |
| nixnax | 128:e5958d143e9d | 204 | memcpy(&context->buffer[j], data, (i = 64 - j)); |
| nixnax | 128:e5958d143e9d | 205 | SHA1Transform(context->state, context->buffer); |
| nixnax | 128:e5958d143e9d | 206 | for (; i + 63 < len; i += 64) |
| nixnax | 128:e5958d143e9d | 207 | { |
| nixnax | 128:e5958d143e9d | 208 | SHA1Transform(context->state, &data[i]); |
| nixnax | 128:e5958d143e9d | 209 | } |
| nixnax | 128:e5958d143e9d | 210 | j = 0; |
| nixnax | 128:e5958d143e9d | 211 | } |
| nixnax | 128:e5958d143e9d | 212 | else |
| nixnax | 128:e5958d143e9d | 213 | i = 0; |
| nixnax | 128:e5958d143e9d | 214 | memcpy(&context->buffer[j], &data[i], len - i); |
| nixnax | 128:e5958d143e9d | 215 | } |
| nixnax | 128:e5958d143e9d | 216 | |
| nixnax | 128:e5958d143e9d | 217 | |
| nixnax | 128:e5958d143e9d | 218 | /* Add padding and return the message digest. */ |
| nixnax | 128:e5958d143e9d | 219 | |
| nixnax | 128:e5958d143e9d | 220 | void SHA1Final( |
| nixnax | 128:e5958d143e9d | 221 | unsigned char digest[20], |
| nixnax | 128:e5958d143e9d | 222 | SHA1_CTX * context |
| nixnax | 128:e5958d143e9d | 223 | ) |
| nixnax | 128:e5958d143e9d | 224 | { |
| nixnax | 128:e5958d143e9d | 225 | unsigned i; |
| nixnax | 128:e5958d143e9d | 226 | |
| nixnax | 128:e5958d143e9d | 227 | unsigned char finalcount[8]; |
| nixnax | 128:e5958d143e9d | 228 | |
| nixnax | 128:e5958d143e9d | 229 | unsigned char c; |
| nixnax | 128:e5958d143e9d | 230 | |
| nixnax | 128:e5958d143e9d | 231 | #if 0 /* untested "improvement" by DHR */ |
| nixnax | 128:e5958d143e9d | 232 | /* Convert context->count to a sequence of bytes |
| nixnax | 128:e5958d143e9d | 233 | * in finalcount. Second element first, but |
| nixnax | 128:e5958d143e9d | 234 | * big-endian order within element. |
| nixnax | 128:e5958d143e9d | 235 | * But we do it all backwards. |
| nixnax | 128:e5958d143e9d | 236 | */ |
| nixnax | 128:e5958d143e9d | 237 | unsigned char *fcp = &finalcount[8]; |
| nixnax | 128:e5958d143e9d | 238 | |
| nixnax | 128:e5958d143e9d | 239 | for (i = 0; i < 2; i++) |
| nixnax | 128:e5958d143e9d | 240 | { |
| nixnax | 128:e5958d143e9d | 241 | uint32_t t = context->count[i]; |
| nixnax | 128:e5958d143e9d | 242 | |
| nixnax | 128:e5958d143e9d | 243 | int j; |
| nixnax | 128:e5958d143e9d | 244 | |
| nixnax | 128:e5958d143e9d | 245 | for (j = 0; j < 4; t >>= 8, j++) |
| nixnax | 128:e5958d143e9d | 246 | *--fcp = (unsigned char) t} |
| nixnax | 128:e5958d143e9d | 247 | #else |
| nixnax | 128:e5958d143e9d | 248 | for (i = 0; i < 8; i++) |
| nixnax | 128:e5958d143e9d | 249 | { |
| nixnax | 128:e5958d143e9d | 250 | finalcount[i] = (unsigned char) ((context->count[(i >= 4 ? 0 : 1)] >> ((3 - (i & 3)) * 8)) & 255); /* Endian independent */ |
| nixnax | 128:e5958d143e9d | 251 | } |
| nixnax | 128:e5958d143e9d | 252 | #endif |
| nixnax | 128:e5958d143e9d | 253 | c = 0200; |
| nixnax | 128:e5958d143e9d | 254 | SHA1Update(context, &c, 1); |
| nixnax | 128:e5958d143e9d | 255 | while ((context->count[0] & 504) != 448) |
| nixnax | 128:e5958d143e9d | 256 | { |
| nixnax | 128:e5958d143e9d | 257 | c = 0000; |
| nixnax | 128:e5958d143e9d | 258 | SHA1Update(context, &c, 1); |
| nixnax | 128:e5958d143e9d | 259 | } |
| nixnax | 128:e5958d143e9d | 260 | SHA1Update(context, finalcount, 8); /* Should cause a SHA1Transform() */ |
| nixnax | 128:e5958d143e9d | 261 | for (i = 0; i < 20; i++) |
| nixnax | 128:e5958d143e9d | 262 | { |
| nixnax | 128:e5958d143e9d | 263 | digest[i] = (unsigned char) |
| nixnax | 128:e5958d143e9d | 264 | ((context->state[i >> 2] >> ((3 - (i & 3)) * 8)) & 255); |
| nixnax | 128:e5958d143e9d | 265 | } |
| nixnax | 128:e5958d143e9d | 266 | /* Wipe variables */ |
| nixnax | 128:e5958d143e9d | 267 | memset(context, '\0', sizeof(*context)); |
| nixnax | 128:e5958d143e9d | 268 | memset(&finalcount, '\0', sizeof(finalcount)); |
| nixnax | 128:e5958d143e9d | 269 | } |
| nixnax | 128:e5958d143e9d | 270 | |
| nixnax | 128:e5958d143e9d | 271 | void sha1( |
| nixnax | 128:e5958d143e9d | 272 | char *hash_out, |
| nixnax | 128:e5958d143e9d | 273 | const char *str, |
| nixnax | 128:e5958d143e9d | 274 | int len) |
| nixnax | 128:e5958d143e9d | 275 | { |
| nixnax | 128:e5958d143e9d | 276 | SHA1_CTX ctx; |
| nixnax | 128:e5958d143e9d | 277 | unsigned int ii; |
| nixnax | 128:e5958d143e9d | 278 | |
| nixnax | 128:e5958d143e9d | 279 | SHA1Init(&ctx); |
| nixnax | 128:e5958d143e9d | 280 | for (ii=0; ii<len; ii+=1) |
| nixnax | 128:e5958d143e9d | 281 | SHA1Update(&ctx, (const unsigned char*)str + ii, 1); |
| nixnax | 128:e5958d143e9d | 282 | SHA1Final((unsigned char *)hash_out, &ctx); |
| nixnax | 128:e5958d143e9d | 283 | // hash_out[20] = '\0'; |
| nixnax | 128:e5958d143e9d | 284 | } |
| nixnax | 128:e5958d143e9d | 285 |
 Nicolas Nackel
Nicolas Nackel