SX1276 Shield based Applications
Dependencies: X_NUCLEO_IKS01A1 LoRaWAN-lib SX1276Lib mbed
LoRaWAN-SX1276-Application Demo uses SX1276MB1LAS mbed component shield on a nucleo board platform to demonstrate a Class-A LoRaWAN device in the 915MHz ISM band for North American region. It uses the LoRaWAN-lib and SX1276Lib libraries.
Comissioning.h (LoRaWAN Network Configuration)
The end-device can be activated in one of the two ways:
Over the Air (OTA) activation can be enabled as shown in the figure below.
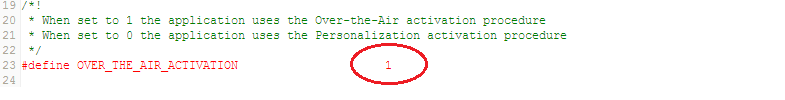
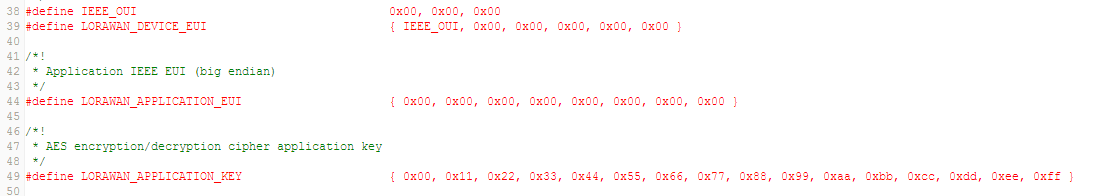
The end-device must be configured with the following parameters:
LORAWAN_DEVICE_EUI(8 Bytes) : Fist 3 Bytes is the Organizationally Unique Identifier (OUI) followed by 5 bytes of unique ID. If not defined by user, then the firmware automatically assigns one to the end-deviceLORAWAN_APPLICATION_EUI(8 Bytes)LORAWAN_APPLICATION_KEY(or DEVKEY) (16 Bytes)
Activation by Personalization (ABP) can be enabled as shown in the figure below.
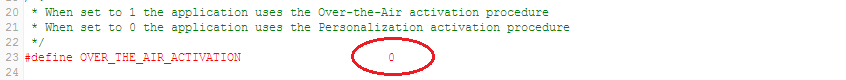
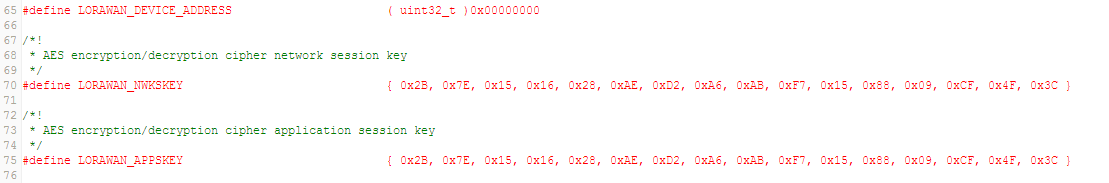
The end-device must be configured with the following parameters:
LORAWAN_DEVICE_ADDRESS(4 Bytes) : If not defined by user, then the firmware automatically assigns one to the end-deviceLORAWAN_NWKSKEY(16 Bytes)LORAWAN_APPSKEY(16 Bytes)
Config.h (LoRaWAN Communication Parameters)
- Mode of Operation : Hybrid
If the end-device needs to be configured to operate over 8-channels, then
Hybrid Modeneeds to be enabled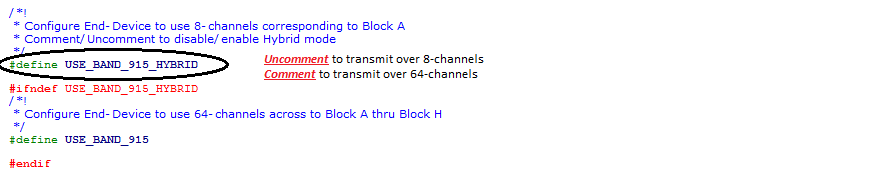
- Mode of Operation : Frequency Hop
If the end-device needs to be configured to operate over 64-channels, then
Hybrid Modeneeds to be disabled
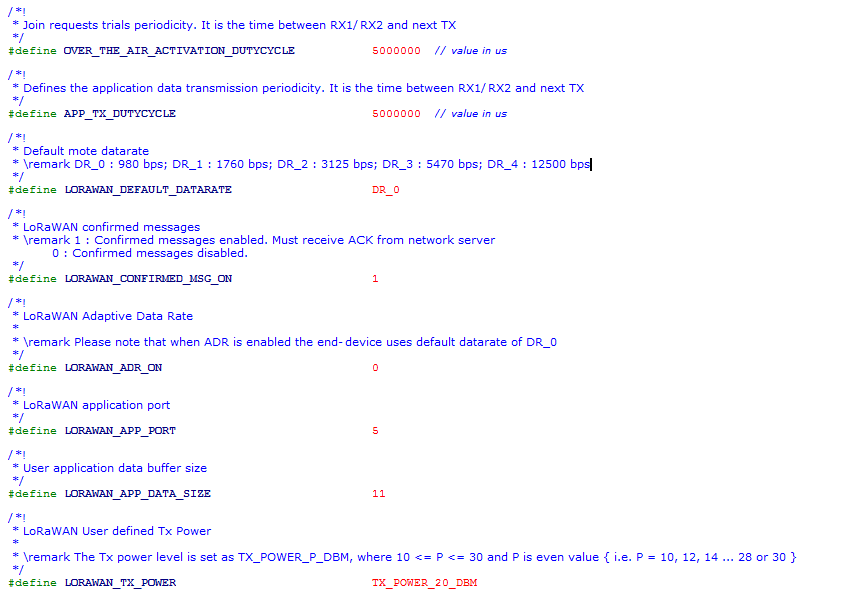
- Delay between successive JOIN REQUESTs :
The delay between successive Join Requests (until the end-device joins the network) can be configured using the parameter
OVER_THE_AIR_ACTIVATION_DUTYCYCLE
- Inter-Frame Delay :
One can change the delay between each frame transmission using
APP_TX_DUTYCYCLEIt is advisable thatAPP_TX_DUTYCYCLEis greater than or equal to 3sec.
- Data Rate :
The data rate can be configured as per LoRaWAN specification using the paramter
LORAWAN_DEFAULT_DATARATE. The range of values are DR_0, DR_1, DR_2, DR_3 and DR_4
- Confirmed/Unconfirmed Messages :
The uplink message or payload can be chosen to be confirmed or unconfirmed using the parameter
LORAWAN_CONFIRMED_MSG_ON. When set to 1, the transmitted messages need to be confirmed with anACKby the network server in the subsequent RX window. When set to 0, noACKis requested.
- ADR ON/OFF :
The ADR can be enabled or disabled using the parameter
LORAWAN_ADR_ON. When set to 1, ADR is enabled and disabled when set to 0.
- Application Port :
The application port can be set using parameter
LORAWAN_APP_PORT. A few examples are associated to specific Application Port, and are defined in Config.h
- Payload Length :
The lenght of the payload (in bytes) to be transmitted can be configured using
LORAWAN_APP_DATA_SIZE
- Transmit Power :
The transmit power can be configured using
LORAWAN_TX_POWER(LoRaMAC verifies if the set power is compliant with the LoRaWAN spec and FCC guidelines)
The baud-rate for serial terminal display is 115200
system/crypto/aes.h@0:42863a11464a, 2016-08-26 (annotated)
- Committer:
- ubhat
- Date:
- Fri Aug 26 19:36:35 2016 +0000
- Revision:
- 0:42863a11464a
SX1276 Shield based Applications
Who changed what in which revision?
| User | Revision | Line number | New contents of line |
|---|---|---|---|
| ubhat | 0:42863a11464a | 1 | /* |
| ubhat | 0:42863a11464a | 2 | --------------------------------------------------------------------------- |
| ubhat | 0:42863a11464a | 3 | Copyright (c) 1998-2008, Brian Gladman, Worcester, UK. All rights reserved. |
| ubhat | 0:42863a11464a | 4 | |
| ubhat | 0:42863a11464a | 5 | LICENSE TERMS |
| ubhat | 0:42863a11464a | 6 | |
| ubhat | 0:42863a11464a | 7 | The redistribution and use of this software (with or without changes) |
| ubhat | 0:42863a11464a | 8 | is allowed without the payment of fees or royalties provided that: |
| ubhat | 0:42863a11464a | 9 | |
| ubhat | 0:42863a11464a | 10 | 1. source code distributions include the above copyright notice, this |
| ubhat | 0:42863a11464a | 11 | list of conditions and the following disclaimer; |
| ubhat | 0:42863a11464a | 12 | |
| ubhat | 0:42863a11464a | 13 | 2. binary distributions include the above copyright notice, this list |
| ubhat | 0:42863a11464a | 14 | of conditions and the following disclaimer in their documentation; |
| ubhat | 0:42863a11464a | 15 | |
| ubhat | 0:42863a11464a | 16 | 3. the name of the copyright holder is not used to endorse products |
| ubhat | 0:42863a11464a | 17 | built using this software without specific written permission. |
| ubhat | 0:42863a11464a | 18 | |
| ubhat | 0:42863a11464a | 19 | DISCLAIMER |
| ubhat | 0:42863a11464a | 20 | |
| ubhat | 0:42863a11464a | 21 | This software is provided 'as is' with no explicit or implied warranties |
| ubhat | 0:42863a11464a | 22 | in respect of its properties, including, but not limited to, correctness |
| ubhat | 0:42863a11464a | 23 | and/or fitness for purpose. |
| ubhat | 0:42863a11464a | 24 | --------------------------------------------------------------------------- |
| ubhat | 0:42863a11464a | 25 | Issue 09/09/2006 |
| ubhat | 0:42863a11464a | 26 | |
| ubhat | 0:42863a11464a | 27 | This is an AES implementation that uses only 8-bit byte operations on the |
| ubhat | 0:42863a11464a | 28 | cipher state. |
| ubhat | 0:42863a11464a | 29 | */ |
| ubhat | 0:42863a11464a | 30 | |
| ubhat | 0:42863a11464a | 31 | #ifndef AES_H |
| ubhat | 0:42863a11464a | 32 | #define AES_H |
| ubhat | 0:42863a11464a | 33 | |
| ubhat | 0:42863a11464a | 34 | #if 1 |
| ubhat | 0:42863a11464a | 35 | # define AES_ENC_PREKEYED /* AES encryption with a precomputed key schedule */ |
| ubhat | 0:42863a11464a | 36 | #endif |
| ubhat | 0:42863a11464a | 37 | #if 0 |
| ubhat | 0:42863a11464a | 38 | # define AES_DEC_PREKEYED /* AES decryption with a precomputed key schedule */ |
| ubhat | 0:42863a11464a | 39 | #endif |
| ubhat | 0:42863a11464a | 40 | #if 0 |
| ubhat | 0:42863a11464a | 41 | # define AES_ENC_128_OTFK /* AES encryption with 'on the fly' 128 bit keying */ |
| ubhat | 0:42863a11464a | 42 | #endif |
| ubhat | 0:42863a11464a | 43 | #if 0 |
| ubhat | 0:42863a11464a | 44 | # define AES_DEC_128_OTFK /* AES decryption with 'on the fly' 128 bit keying */ |
| ubhat | 0:42863a11464a | 45 | #endif |
| ubhat | 0:42863a11464a | 46 | #if 0 |
| ubhat | 0:42863a11464a | 47 | # define AES_ENC_256_OTFK /* AES encryption with 'on the fly' 256 bit keying */ |
| ubhat | 0:42863a11464a | 48 | #endif |
| ubhat | 0:42863a11464a | 49 | #if 0 |
| ubhat | 0:42863a11464a | 50 | # define AES_DEC_256_OTFK /* AES decryption with 'on the fly' 256 bit keying */ |
| ubhat | 0:42863a11464a | 51 | #endif |
| ubhat | 0:42863a11464a | 52 | |
| ubhat | 0:42863a11464a | 53 | #define N_ROW 4 |
| ubhat | 0:42863a11464a | 54 | #define N_COL 4 |
| ubhat | 0:42863a11464a | 55 | #define N_BLOCK (N_ROW * N_COL) |
| ubhat | 0:42863a11464a | 56 | #define N_MAX_ROUNDS 14 |
| ubhat | 0:42863a11464a | 57 | |
| ubhat | 0:42863a11464a | 58 | typedef uint8_t return_type; |
| ubhat | 0:42863a11464a | 59 | |
| ubhat | 0:42863a11464a | 60 | /* Warning: The key length for 256 bit keys overflows a byte |
| ubhat | 0:42863a11464a | 61 | (see comment below) |
| ubhat | 0:42863a11464a | 62 | */ |
| ubhat | 0:42863a11464a | 63 | |
| ubhat | 0:42863a11464a | 64 | typedef uint8_t length_type; |
| ubhat | 0:42863a11464a | 65 | |
| ubhat | 0:42863a11464a | 66 | typedef struct |
| ubhat | 0:42863a11464a | 67 | { uint8_t ksch[(N_MAX_ROUNDS + 1) * N_BLOCK]; |
| ubhat | 0:42863a11464a | 68 | uint8_t rnd; |
| ubhat | 0:42863a11464a | 69 | } aes_context; |
| ubhat | 0:42863a11464a | 70 | |
| ubhat | 0:42863a11464a | 71 | /* The following calls are for a precomputed key schedule |
| ubhat | 0:42863a11464a | 72 | |
| ubhat | 0:42863a11464a | 73 | NOTE: If the length_type used for the key length is an |
| ubhat | 0:42863a11464a | 74 | unsigned 8-bit character, a key length of 256 bits must |
| ubhat | 0:42863a11464a | 75 | be entered as a length in bytes (valid inputs are hence |
| ubhat | 0:42863a11464a | 76 | 128, 192, 16, 24 and 32). |
| ubhat | 0:42863a11464a | 77 | */ |
| ubhat | 0:42863a11464a | 78 | |
| ubhat | 0:42863a11464a | 79 | #if defined( AES_ENC_PREKEYED ) || defined( AES_DEC_PREKEYED ) |
| ubhat | 0:42863a11464a | 80 | |
| ubhat | 0:42863a11464a | 81 | return_type aes_set_key( const uint8_t key[], |
| ubhat | 0:42863a11464a | 82 | length_type keylen, |
| ubhat | 0:42863a11464a | 83 | aes_context ctx[1] ); |
| ubhat | 0:42863a11464a | 84 | #endif |
| ubhat | 0:42863a11464a | 85 | |
| ubhat | 0:42863a11464a | 86 | #if defined( AES_ENC_PREKEYED ) |
| ubhat | 0:42863a11464a | 87 | |
| ubhat | 0:42863a11464a | 88 | return_type aes_encrypt( const uint8_t in[N_BLOCK], |
| ubhat | 0:42863a11464a | 89 | uint8_t out[N_BLOCK], |
| ubhat | 0:42863a11464a | 90 | const aes_context ctx[1] ); |
| ubhat | 0:42863a11464a | 91 | |
| ubhat | 0:42863a11464a | 92 | return_type aes_cbc_encrypt( const uint8_t *in, |
| ubhat | 0:42863a11464a | 93 | uint8_t *out, |
| ubhat | 0:42863a11464a | 94 | int32_t n_block, |
| ubhat | 0:42863a11464a | 95 | uint8_t iv[N_BLOCK], |
| ubhat | 0:42863a11464a | 96 | const aes_context ctx[1] ); |
| ubhat | 0:42863a11464a | 97 | #endif |
| ubhat | 0:42863a11464a | 98 | |
| ubhat | 0:42863a11464a | 99 | #if defined( AES_DEC_PREKEYED ) |
| ubhat | 0:42863a11464a | 100 | |
| ubhat | 0:42863a11464a | 101 | return_type aes_decrypt( const uint8_t in[N_BLOCK], |
| ubhat | 0:42863a11464a | 102 | uint8_t out[N_BLOCK], |
| ubhat | 0:42863a11464a | 103 | const aes_context ctx[1] ); |
| ubhat | 0:42863a11464a | 104 | |
| ubhat | 0:42863a11464a | 105 | return_type aes_cbc_decrypt( const uint8_t *in, |
| ubhat | 0:42863a11464a | 106 | uint8_t *out, |
| ubhat | 0:42863a11464a | 107 | int32_t n_block, |
| ubhat | 0:42863a11464a | 108 | uint8_t iv[N_BLOCK], |
| ubhat | 0:42863a11464a | 109 | const aes_context ctx[1] ); |
| ubhat | 0:42863a11464a | 110 | #endif |
| ubhat | 0:42863a11464a | 111 | |
| ubhat | 0:42863a11464a | 112 | /* The following calls are for 'on the fly' keying. In this case the |
| ubhat | 0:42863a11464a | 113 | encryption and decryption keys are different. |
| ubhat | 0:42863a11464a | 114 | |
| ubhat | 0:42863a11464a | 115 | The encryption subroutines take a key in an array of bytes in |
| ubhat | 0:42863a11464a | 116 | key[L] where L is 16, 24 or 32 bytes for key lengths of 128, |
| ubhat | 0:42863a11464a | 117 | 192, and 256 bits respectively. They then encrypts the input |
| ubhat | 0:42863a11464a | 118 | data, in[] with this key and put the reult in the output array |
| ubhat | 0:42863a11464a | 119 | out[]. In addition, the second key array, o_key[L], is used |
| ubhat | 0:42863a11464a | 120 | to output the key that is needed by the decryption subroutine |
| ubhat | 0:42863a11464a | 121 | to reverse the encryption operation. The two key arrays can |
| ubhat | 0:42863a11464a | 122 | be the same array but in this case the original key will be |
| ubhat | 0:42863a11464a | 123 | overwritten. |
| ubhat | 0:42863a11464a | 124 | |
| ubhat | 0:42863a11464a | 125 | In the same way, the decryption subroutines output keys that |
| ubhat | 0:42863a11464a | 126 | can be used to reverse their effect when used for encryption. |
| ubhat | 0:42863a11464a | 127 | |
| ubhat | 0:42863a11464a | 128 | Only 128 and 256 bit keys are supported in these 'on the fly' |
| ubhat | 0:42863a11464a | 129 | modes. |
| ubhat | 0:42863a11464a | 130 | */ |
| ubhat | 0:42863a11464a | 131 | |
| ubhat | 0:42863a11464a | 132 | #if defined( AES_ENC_128_OTFK ) |
| ubhat | 0:42863a11464a | 133 | void aes_encrypt_128( const uint8_t in[N_BLOCK], |
| ubhat | 0:42863a11464a | 134 | uint8_t out[N_BLOCK], |
| ubhat | 0:42863a11464a | 135 | const uint8_t key[N_BLOCK], |
| ubhat | 0:42863a11464a | 136 | uint8_t o_key[N_BLOCK] ); |
| ubhat | 0:42863a11464a | 137 | #endif |
| ubhat | 0:42863a11464a | 138 | |
| ubhat | 0:42863a11464a | 139 | #if defined( AES_DEC_128_OTFK ) |
| ubhat | 0:42863a11464a | 140 | void aes_decrypt_128( const uint8_t in[N_BLOCK], |
| ubhat | 0:42863a11464a | 141 | uint8_t out[N_BLOCK], |
| ubhat | 0:42863a11464a | 142 | const uint8_t key[N_BLOCK], |
| ubhat | 0:42863a11464a | 143 | uint8_t o_key[N_BLOCK] ); |
| ubhat | 0:42863a11464a | 144 | #endif |
| ubhat | 0:42863a11464a | 145 | |
| ubhat | 0:42863a11464a | 146 | #if defined( AES_ENC_256_OTFK ) |
| ubhat | 0:42863a11464a | 147 | void aes_encrypt_256( const uint8_t in[N_BLOCK], |
| ubhat | 0:42863a11464a | 148 | uint8_t out[N_BLOCK], |
| ubhat | 0:42863a11464a | 149 | const uint8_t key[2 * N_BLOCK], |
| ubhat | 0:42863a11464a | 150 | uint8_t o_key[2 * N_BLOCK] ); |
| ubhat | 0:42863a11464a | 151 | #endif |
| ubhat | 0:42863a11464a | 152 | |
| ubhat | 0:42863a11464a | 153 | #if defined( AES_DEC_256_OTFK ) |
| ubhat | 0:42863a11464a | 154 | void aes_decrypt_256( const uint8_t in[N_BLOCK], |
| ubhat | 0:42863a11464a | 155 | uint8_t out[N_BLOCK], |
| ubhat | 0:42863a11464a | 156 | const uint8_t key[2 * N_BLOCK], |
| ubhat | 0:42863a11464a | 157 | uint8_t o_key[2 * N_BLOCK] ); |
| ubhat | 0:42863a11464a | 158 | #endif |
| ubhat | 0:42863a11464a | 159 | |
| ubhat | 0:42863a11464a | 160 | #endif |