BG96_K6xF_pelion-example-frdm_Temp
Dependencies: FXAS21002 FXOS8700Q
Overview
This document is based on https://os.mbed.com/teams/NXP/code/pelion-example-frdm/ and the code forked Daniel_Lee's(https://os.mbed.com/users/Daniel_Lee/code/BG96_K6xF_pelion-example-frdm/)BG96_K6xF_pelion-example-frdm repository and added some features. Need a WIZnet IoT Shield BG96 board and development board.
This example is known to work great on the following platforms:
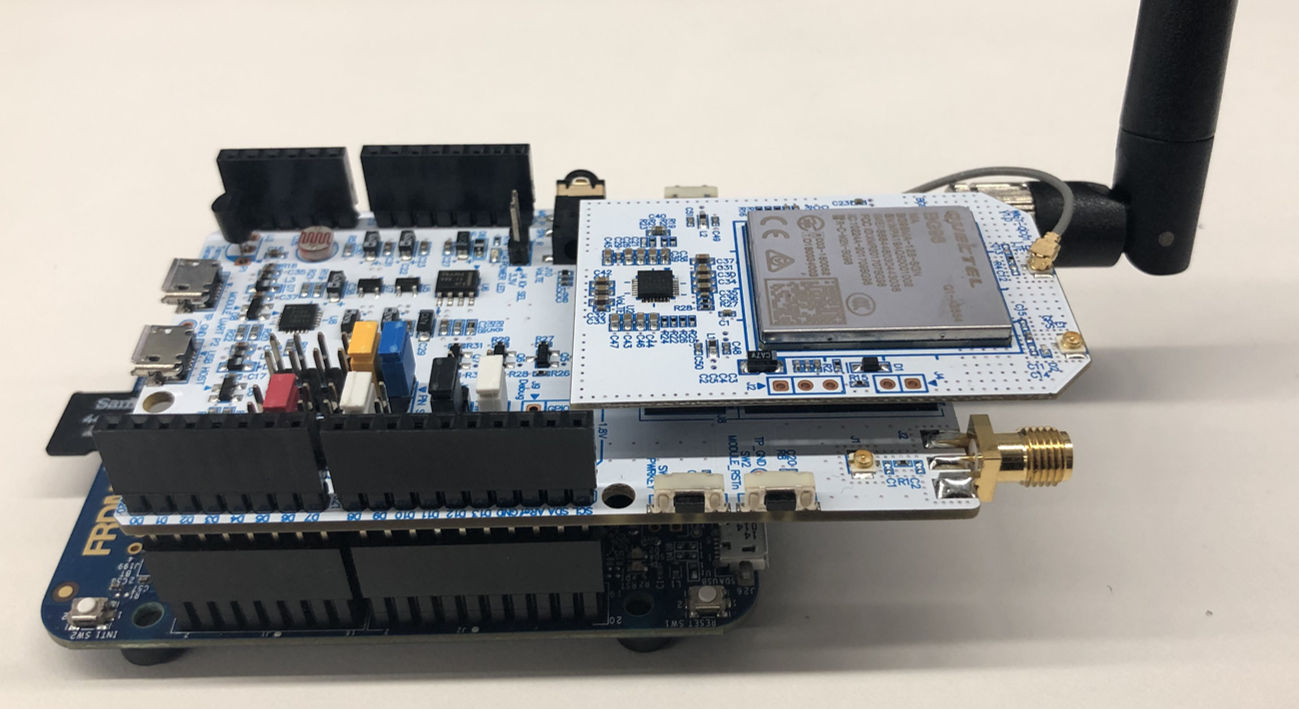
Requirement
- FRDM-K64F or FRDM-K66F
- WIZnet IoT Shield BG96 board
- USIM card
Example functionality
This example showcases the following device functionality:
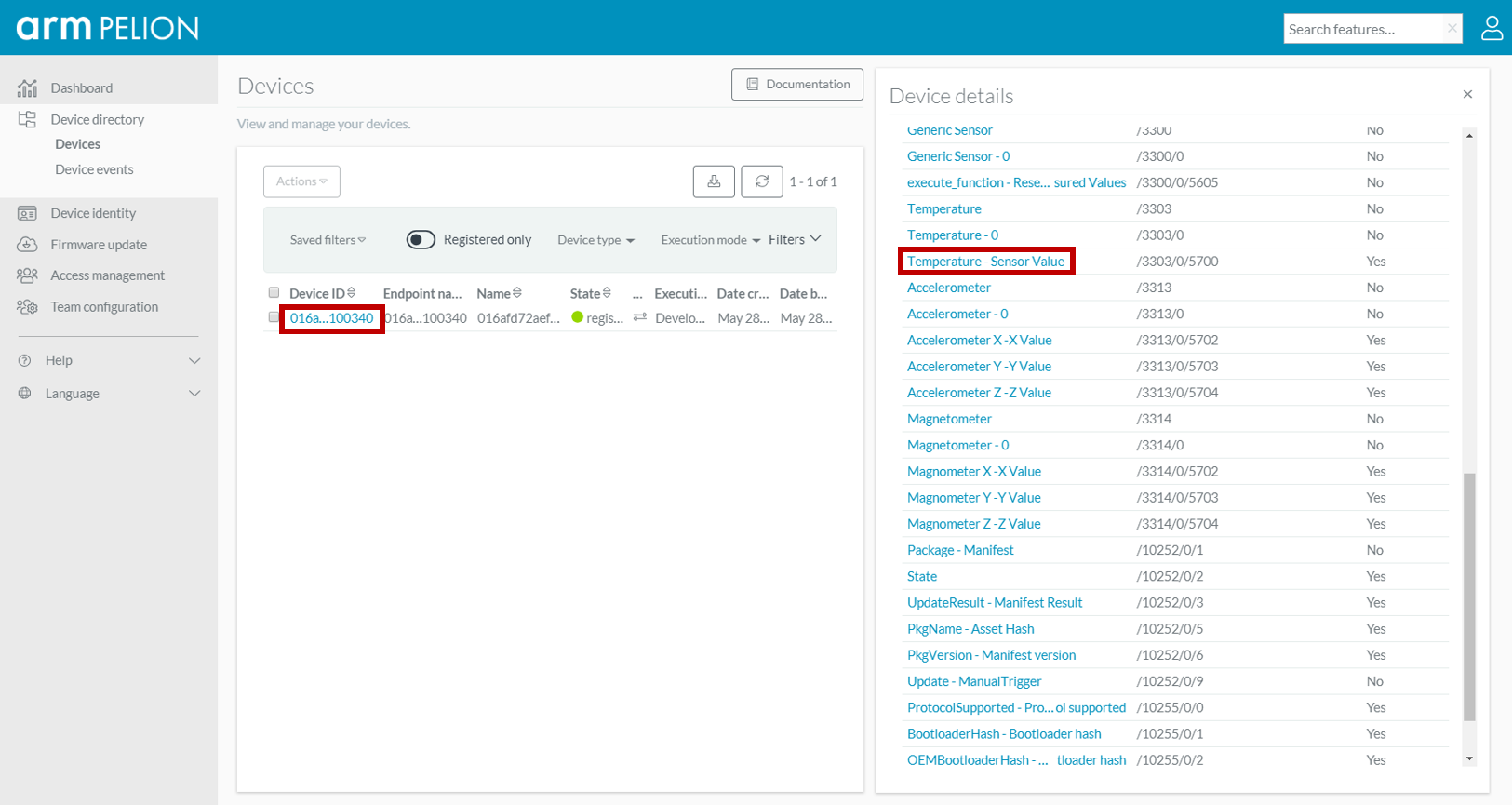
Read onboard FXOS8700Q accelerometer, magnetometer and temperature(on shield). And report the values as Pelion LWM2M resources (see image below). (FRDM-K66F only) Read onboard FXAS21002 gyroscope and report the values as Pelion LWM2M resources. On user button click, increment Pelion LWM2M button resource. Allow the user to change the state of the board LED from Pelion LWM2M led_state resource and PUT request.
1. Import into Compiler
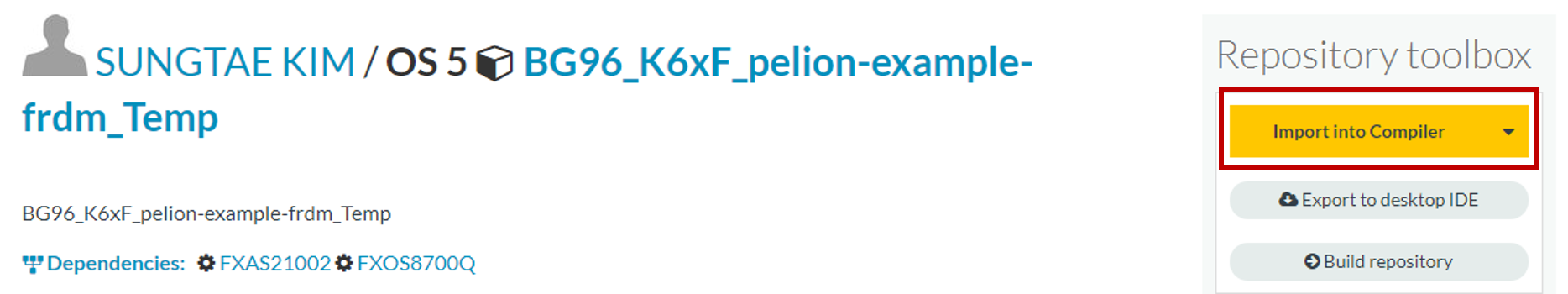
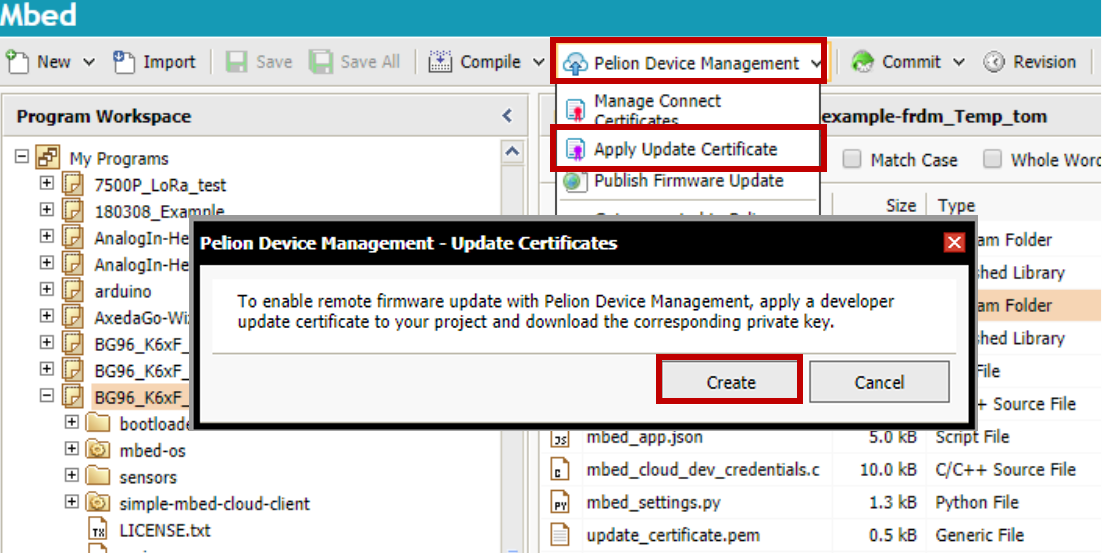
2. Apply Update Certificate
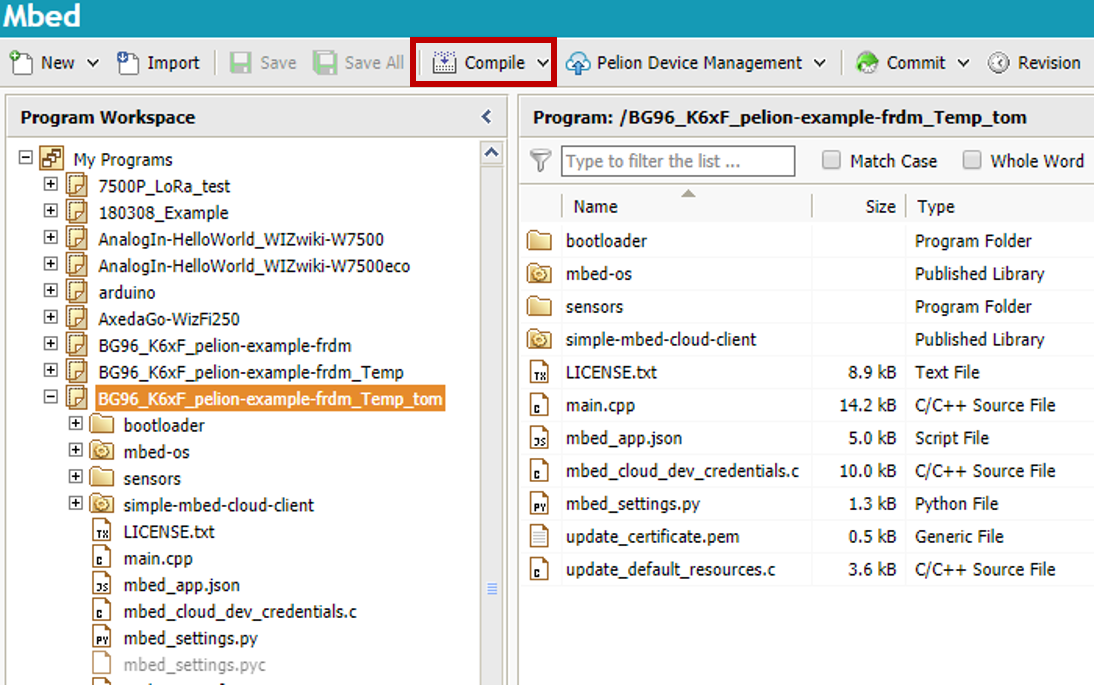
3. Compile and Program
4. If successfully connect to cellular networks(SKTelecom) then you can get below message
Device's Result
include the mbed library with this snippet
You can hold the user button during boot to format the storage and change the device identity. M2Mnet(BG96) Power ON Sensors configuration: FXOS8700Q accelerometer = 0xC7 FXOS8700Q magnetometer = 0xC7 Connecting to the network using the default network interface... Connected to the network successfully. IP address: 2001:2D8:65 Initializing Pelion Device Management Client... Initialized Pelion Device Management Client. Registering... Press the user button to increment the LwM2M resource value... Celsius temp : 26.10 C FXOS8700Q mag: 0.217 x, 0.420 y, 0.288 z [gauss]
Pelion Cloud Result (1)
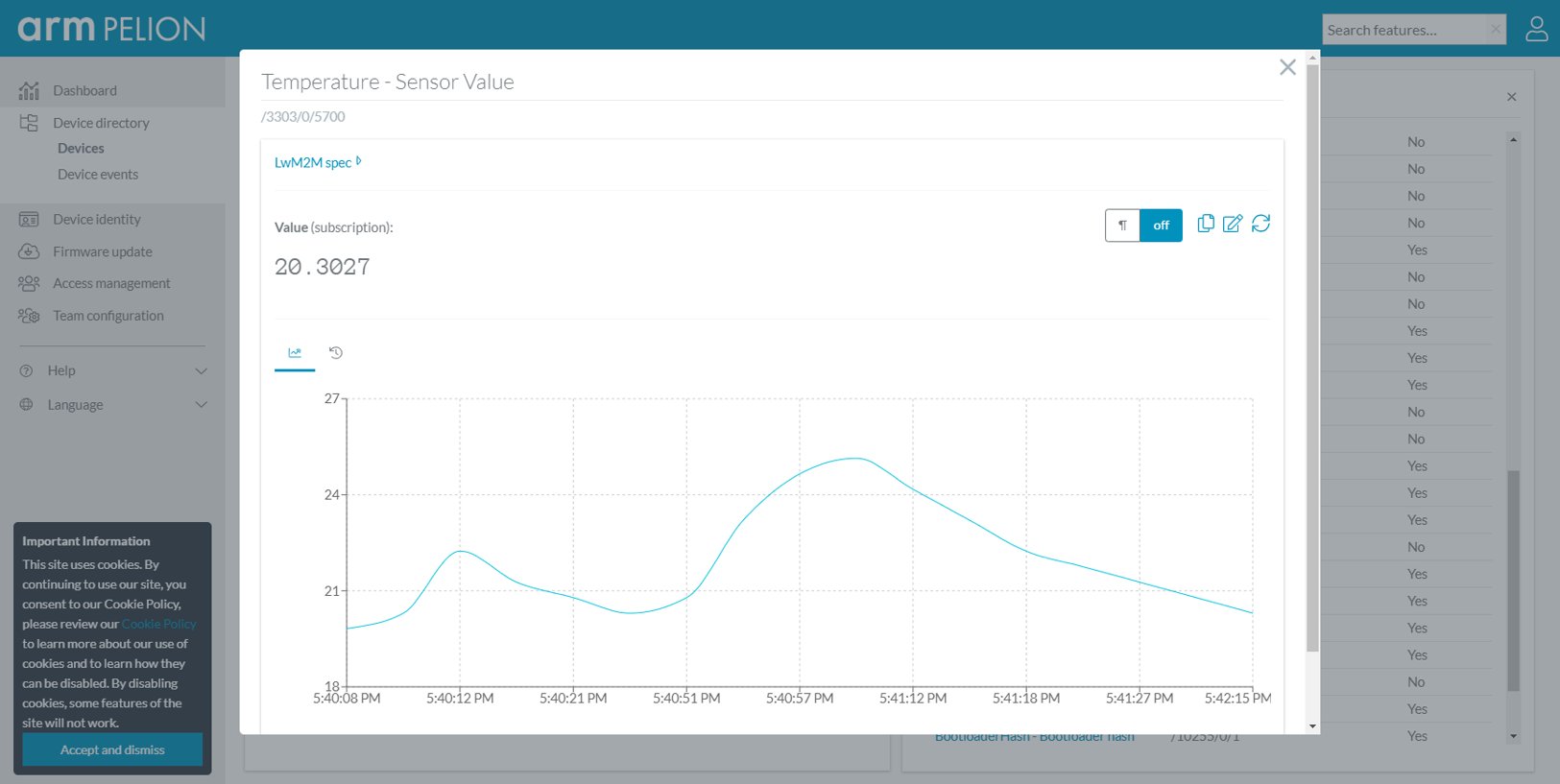
Pelion Cloud Result (2)
mbed_cloud_dev_credentials.c
- Committer:
- stkim92
- Date:
- 2019-08-06
- Revision:
- 14:bd420de18a97
- Parent:
- 0:a9d53048f0b6
File content as of revision 14:bd420de18a97:
/*
* Copyright (c) 2018 ARM Limited. All rights reserved.
* SPDX-License-Identifier: Apache-2.0
* Licensed under the Apache License, Version 2.0 (the License); you may
* not use this file except in compliance with the License.
* You may obtain a copy of the License at
*
* http://www.apache.org/licenses/LICENSE-2.0
*
* Unless required by applicable law or agreed to in writing, software
* distributed under the License is distributed on an AS IS BASIS, WITHOUT
* WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
* See the License for the specific language governing permissions and
* limitations under the License.
*/
#ifndef __MBED_CLOUD_DEV_CREDENTIALS_H__
#define __MBED_CLOUD_DEV_CREDENTIALS_H__
#include <inttypes.h>
const char MBED_CLOUD_DEV_BOOTSTRAP_ENDPOINT_NAME[] = "016c22e3835236edb65b18b303c00000";
const char MBED_CLOUD_DEV_ACCOUNT_ID[] = "016c22e26fecaab1b96ba5c000000000";
const char MBED_CLOUD_DEV_BOOTSTRAP_SERVER_URI[] = "coaps://bootstrap.us-east-1.mbedcloud.com:5684?aid=016c22e26fecaab1b96ba5c000000000";
const uint8_t MBED_CLOUD_DEV_BOOTSTRAP_DEVICE_CERTIFICATE[] =
{ 0x30, 0x82, 0x02, 0x82, 0x30, 0x82, 0x02, 0x29,
0xa0, 0x03, 0x02, 0x01, 0x02, 0x02, 0x10, 0x1c,
0xe7, 0x8e, 0xb4, 0xd0, 0x26, 0x4c, 0x17, 0xb1,
0xfd, 0x4a, 0x68, 0x8e, 0x89, 0xb7, 0xc5, 0x30,
0x0a, 0x06, 0x08, 0x2a, 0x86, 0x48, 0xce, 0x3d,
0x04, 0x03, 0x02, 0x30, 0x81, 0xa2, 0x31, 0x0b,
0x30, 0x09, 0x06, 0x03, 0x55, 0x04, 0x06, 0x13,
0x02, 0x47, 0x42, 0x31, 0x17, 0x30, 0x15, 0x06,
0x03, 0x55, 0x04, 0x08, 0x0c, 0x0e, 0x43, 0x61,
0x6d, 0x62, 0x72, 0x69, 0x64, 0x67, 0x65, 0x73,
0x68, 0x69, 0x72, 0x65, 0x31, 0x12, 0x30, 0x10,
0x06, 0x03, 0x55, 0x04, 0x07, 0x0c, 0x09, 0x43,
0x61, 0x6d, 0x62, 0x72, 0x69, 0x64, 0x67, 0x65,
0x31, 0x10, 0x30, 0x0e, 0x06, 0x03, 0x55, 0x04,
0x0a, 0x0c, 0x07, 0x41, 0x52, 0x4d, 0x20, 0x4c,
0x74, 0x64, 0x31, 0x29, 0x30, 0x27, 0x06, 0x03,
0x55, 0x04, 0x0b, 0x0c, 0x20, 0x30, 0x31, 0x36,
0x63, 0x32, 0x32, 0x65, 0x32, 0x36, 0x66, 0x65,
0x63, 0x61, 0x61, 0x62, 0x31, 0x62, 0x39, 0x36,
0x62, 0x61, 0x35, 0x63, 0x30, 0x30, 0x30, 0x30,
0x30, 0x30, 0x30, 0x30, 0x30, 0x31, 0x29, 0x30,
0x27, 0x06, 0x03, 0x55, 0x04, 0x03, 0x0c, 0x20,
0x30, 0x31, 0x36, 0x63, 0x32, 0x32, 0x65, 0x33,
0x38, 0x33, 0x35, 0x32, 0x33, 0x36, 0x65, 0x64,
0x62, 0x36, 0x35, 0x62, 0x31, 0x38, 0x62, 0x33,
0x30, 0x33, 0x63, 0x30, 0x30, 0x30, 0x30, 0x30,
0x30, 0x1e, 0x17, 0x0d, 0x31, 0x39, 0x30, 0x37,
0x32, 0x34, 0x30, 0x37, 0x33, 0x30, 0x33, 0x31,
0x5a, 0x17, 0x0d, 0x32, 0x39, 0x30, 0x37, 0x32,
0x34, 0x30, 0x37, 0x33, 0x30, 0x33, 0x31, 0x5a,
0x30, 0x81, 0xa2, 0x31, 0x0b, 0x30, 0x09, 0x06,
0x03, 0x55, 0x04, 0x06, 0x13, 0x02, 0x47, 0x42,
0x31, 0x17, 0x30, 0x15, 0x06, 0x03, 0x55, 0x04,
0x08, 0x0c, 0x0e, 0x43, 0x61, 0x6d, 0x62, 0x72,
0x69, 0x64, 0x67, 0x65, 0x73, 0x68, 0x69, 0x72,
0x65, 0x31, 0x12, 0x30, 0x10, 0x06, 0x03, 0x55,
0x04, 0x07, 0x0c, 0x09, 0x43, 0x61, 0x6d, 0x62,
0x72, 0x69, 0x64, 0x67, 0x65, 0x31, 0x10, 0x30,
0x0e, 0x06, 0x03, 0x55, 0x04, 0x0a, 0x0c, 0x07,
0x41, 0x52, 0x4d, 0x20, 0x4c, 0x74, 0x64, 0x31,
0x29, 0x30, 0x27, 0x06, 0x03, 0x55, 0x04, 0x0b,
0x0c, 0x20, 0x30, 0x31, 0x36, 0x63, 0x32, 0x32,
0x65, 0x32, 0x36, 0x66, 0x65, 0x63, 0x61, 0x61,
0x62, 0x31, 0x62, 0x39, 0x36, 0x62, 0x61, 0x35,
0x63, 0x30, 0x30, 0x30, 0x30, 0x30, 0x30, 0x30,
0x30, 0x30, 0x31, 0x29, 0x30, 0x27, 0x06, 0x03,
0x55, 0x04, 0x03, 0x0c, 0x20, 0x30, 0x31, 0x36,
0x63, 0x32, 0x32, 0x65, 0x33, 0x38, 0x33, 0x35,
0x32, 0x33, 0x36, 0x65, 0x64, 0x62, 0x36, 0x35,
0x62, 0x31, 0x38, 0x62, 0x33, 0x30, 0x33, 0x63,
0x30, 0x30, 0x30, 0x30, 0x30, 0x30, 0x59, 0x30,
0x13, 0x06, 0x07, 0x2a, 0x86, 0x48, 0xce, 0x3d,
0x02, 0x01, 0x06, 0x08, 0x2a, 0x86, 0x48, 0xce,
0x3d, 0x03, 0x01, 0x07, 0x03, 0x42, 0x00, 0x04,
0x9c, 0x97, 0x23, 0xe8, 0x34, 0x40, 0x3b, 0x67,
0x0e, 0x75, 0xd7, 0x4a, 0xf7, 0xc6, 0x3e, 0x87,
0x97, 0x86, 0xad, 0xb8, 0x29, 0x08, 0x92, 0x60,
0xcb, 0x10, 0x6f, 0x11, 0x22, 0x5b, 0x21, 0x38,
0xa8, 0x58, 0xad, 0xf8, 0x51, 0xc1, 0xb1, 0x60,
0x3c, 0x67, 0xe9, 0xb0, 0x13, 0x01, 0x61, 0x62,
0x55, 0x35, 0x60, 0x1d, 0x85, 0x3b, 0xed, 0x8f,
0x9b, 0x5b, 0x3b, 0x8a, 0x24, 0x89, 0x88, 0x87,
0xa3, 0x3f, 0x30, 0x3d, 0x30, 0x12, 0x06, 0x09,
0x2b, 0x06, 0x01, 0x04, 0x01, 0xa0, 0x20, 0x81,
0x49, 0x04, 0x05, 0x02, 0x03, 0x40, 0x00, 0x91,
0x30, 0x12, 0x06, 0x03, 0x55, 0x1d, 0x13, 0x01,
0x01, 0xff, 0x04, 0x08, 0x30, 0x06, 0x01, 0x01,
0xff, 0x02, 0x01, 0x00, 0x30, 0x13, 0x06, 0x03,
0x55, 0x1d, 0x25, 0x04, 0x0c, 0x30, 0x0a, 0x06,
0x08, 0x2b, 0x06, 0x01, 0x05, 0x05, 0x07, 0x03,
0x02, 0x30, 0x0a, 0x06, 0x08, 0x2a, 0x86, 0x48,
0xce, 0x3d, 0x04, 0x03, 0x02, 0x03, 0x47, 0x00,
0x30, 0x44, 0x02, 0x20, 0x08, 0xa7, 0x2f, 0xdf,
0x41, 0x6a, 0xc5, 0x97, 0xe9, 0xa3, 0x45, 0x96,
0x50, 0x09, 0xf9, 0x24, 0x6f, 0xf1, 0x9a, 0x5a,
0xe3, 0xa1, 0x82, 0xf0, 0x8b, 0x1b, 0x04, 0x03,
0x62, 0xdd, 0xc1, 0x8a, 0x02, 0x20, 0x5b, 0x33,
0x71, 0x3f, 0x23, 0x2e, 0x88, 0xd4, 0x4c, 0xcb,
0x22, 0xf0, 0x7b, 0x6c, 0xc3, 0x35, 0xbe, 0x78,
0xff, 0xe1, 0x69, 0x14, 0x70, 0x8e, 0x5b, 0x47,
0x7d, 0x30, 0xf3, 0x96, 0x3e, 0x73 };
const uint8_t MBED_CLOUD_DEV_BOOTSTRAP_SERVER_ROOT_CA_CERTIFICATE[] =
{ 0x30, 0x82, 0x02, 0x1f, 0x30, 0x82, 0x01, 0xc5,
0xa0, 0x03, 0x02, 0x01, 0x02, 0x02, 0x10, 0x3c,
0x63, 0x38, 0x70, 0x08, 0xd3, 0xc9, 0x8a, 0x4c,
0x72, 0x1f, 0x8f, 0x45, 0xeb, 0xd8, 0xf3, 0x30,
0x0a, 0x06, 0x08, 0x2a, 0x86, 0x48, 0xce, 0x3d,
0x04, 0x03, 0x02, 0x30, 0x67, 0x31, 0x0b, 0x30,
0x09, 0x06, 0x03, 0x55, 0x04, 0x06, 0x13, 0x02,
0x47, 0x42, 0x31, 0x17, 0x30, 0x15, 0x06, 0x03,
0x55, 0x04, 0x08, 0x13, 0x0e, 0x43, 0x61, 0x6d,
0x62, 0x72, 0x69, 0x64, 0x67, 0x65, 0x73, 0x68,
0x69, 0x72, 0x65, 0x31, 0x12, 0x30, 0x10, 0x06,
0x03, 0x55, 0x04, 0x07, 0x13, 0x09, 0x43, 0x61,
0x6d, 0x62, 0x72, 0x69, 0x64, 0x67, 0x65, 0x31,
0x10, 0x30, 0x0e, 0x06, 0x03, 0x55, 0x04, 0x0a,
0x13, 0x07, 0x41, 0x52, 0x4d, 0x20, 0x4c, 0x74,
0x64, 0x31, 0x19, 0x30, 0x17, 0x06, 0x03, 0x55,
0x04, 0x03, 0x13, 0x10, 0x41, 0x52, 0x4d, 0x20,
0x42, 0x6f, 0x6f, 0x74, 0x73, 0x74, 0x72, 0x61,
0x70, 0x20, 0x43, 0x41, 0x30, 0x20, 0x17, 0x0d,
0x31, 0x37, 0x30, 0x34, 0x30, 0x33, 0x31, 0x34,
0x30, 0x33, 0x33, 0x36, 0x5a, 0x18, 0x0f, 0x32,
0x30, 0x35, 0x32, 0x30, 0x34, 0x30, 0x33, 0x31,
0x34, 0x31, 0x33, 0x33, 0x36, 0x5a, 0x30, 0x67,
0x31, 0x0b, 0x30, 0x09, 0x06, 0x03, 0x55, 0x04,
0x06, 0x13, 0x02, 0x47, 0x42, 0x31, 0x17, 0x30,
0x15, 0x06, 0x03, 0x55, 0x04, 0x08, 0x13, 0x0e,
0x43, 0x61, 0x6d, 0x62, 0x72, 0x69, 0x64, 0x67,
0x65, 0x73, 0x68, 0x69, 0x72, 0x65, 0x31, 0x12,
0x30, 0x10, 0x06, 0x03, 0x55, 0x04, 0x07, 0x13,
0x09, 0x43, 0x61, 0x6d, 0x62, 0x72, 0x69, 0x64,
0x67, 0x65, 0x31, 0x10, 0x30, 0x0e, 0x06, 0x03,
0x55, 0x04, 0x0a, 0x13, 0x07, 0x41, 0x52, 0x4d,
0x20, 0x4c, 0x74, 0x64, 0x31, 0x19, 0x30, 0x17,
0x06, 0x03, 0x55, 0x04, 0x03, 0x13, 0x10, 0x41,
0x52, 0x4d, 0x20, 0x42, 0x6f, 0x6f, 0x74, 0x73,
0x74, 0x72, 0x61, 0x70, 0x20, 0x43, 0x41, 0x30,
0x59, 0x30, 0x13, 0x06, 0x07, 0x2a, 0x86, 0x48,
0xce, 0x3d, 0x02, 0x01, 0x06, 0x08, 0x2a, 0x86,
0x48, 0xce, 0x3d, 0x03, 0x01, 0x07, 0x03, 0x42,
0x00, 0x04, 0x3b, 0xd3, 0xfe, 0xb0, 0xd9, 0xa4,
0x72, 0xe1, 0x11, 0x11, 0x59, 0xba, 0x06, 0x2d,
0xf8, 0x26, 0xd5, 0x65, 0x98, 0xaa, 0xcf, 0x2a,
0x5f, 0xc6, 0x87, 0xa5, 0x6b, 0x0e, 0x30, 0x15,
0xe8, 0x12, 0x16, 0x49, 0x90, 0xe3, 0xf9, 0x3e,
0xf9, 0x3d, 0xde, 0xf5, 0x5a, 0x1f, 0x03, 0x44,
0xbb, 0x81, 0x7a, 0xc9, 0x71, 0x6d, 0x6c, 0xc2,
0x42, 0x3b, 0x55, 0xdb, 0x86, 0xad, 0x2c, 0xc0,
0xcf, 0xe4, 0xa3, 0x51, 0x30, 0x4f, 0x30, 0x0b,
0x06, 0x03, 0x55, 0x1d, 0x0f, 0x04, 0x04, 0x03,
0x02, 0x01, 0x86, 0x30, 0x0f, 0x06, 0x03, 0x55,
0x1d, 0x13, 0x01, 0x01, 0xff, 0x04, 0x05, 0x30,
0x03, 0x01, 0x01, 0xff, 0x30, 0x1d, 0x06, 0x03,
0x55, 0x1d, 0x0e, 0x04, 0x16, 0x04, 0x14, 0x84,
0xc0, 0xf5, 0x82, 0xe9, 0x5d, 0xa5, 0xe0, 0xaa,
0x74, 0x6f, 0xf7, 0x81, 0x8f, 0x4b, 0xe8, 0x9e,
0xde, 0x5d, 0x80, 0x30, 0x10, 0x06, 0x09, 0x2b,
0x06, 0x01, 0x04, 0x01, 0x82, 0x37, 0x15, 0x01,
0x04, 0x03, 0x02, 0x01, 0x00, 0x30, 0x0a, 0x06,
0x08, 0x2a, 0x86, 0x48, 0xce, 0x3d, 0x04, 0x03,
0x02, 0x03, 0x48, 0x00, 0x30, 0x45, 0x02, 0x20,
0x19, 0x24, 0x0b, 0xc4, 0xac, 0x9d, 0x2b, 0x15,
0xf8, 0xc3, 0x0c, 0x0b, 0xf6, 0xac, 0xb3, 0xa1,
0xeb, 0x83, 0xfe, 0x1c, 0x4a, 0x96, 0x44, 0xc6,
0xa0, 0xbb, 0x56, 0x5c, 0x84, 0x13, 0xc9, 0x0f,
0x02, 0x21, 0x00, 0xbd, 0x89, 0x1c, 0x54, 0x98,
0xa5, 0xd0, 0x98, 0xc7, 0x0c, 0x08, 0x2f, 0xd9,
0x1b, 0xb8, 0x7e, 0xbf, 0x84, 0x3a, 0xfb, 0x8a,
0x43, 0x1a, 0x8e, 0xac, 0xdc, 0xa8, 0x66, 0x3d,
0xe3, 0xf9, 0xdc };
const uint8_t MBED_CLOUD_DEV_BOOTSTRAP_DEVICE_PRIVATE_KEY[] =
{ 0x30, 0x81, 0x93, 0x02, 0x01, 0x00, 0x30, 0x13,
0x06, 0x07, 0x2a, 0x86, 0x48, 0xce, 0x3d, 0x02,
0x01, 0x06, 0x08, 0x2a, 0x86, 0x48, 0xce, 0x3d,
0x03, 0x01, 0x07, 0x04, 0x79, 0x30, 0x77, 0x02,
0x01, 0x01, 0x04, 0x20, 0x02, 0xb2, 0xbd, 0xc0,
0x87, 0x8e, 0x1d, 0x2a, 0xc5, 0x9f, 0xa1, 0x67,
0xec, 0x1a, 0xbc, 0x9e, 0x93, 0xc4, 0x0b, 0xb7,
0xba, 0xd2, 0x6a, 0xd3, 0xe9, 0x21, 0x5d, 0x61,
0x7a, 0x5b, 0xb9, 0x2d, 0xa0, 0x0a, 0x06, 0x08,
0x2a, 0x86, 0x48, 0xce, 0x3d, 0x03, 0x01, 0x07,
0xa1, 0x44, 0x03, 0x42, 0x00, 0x04, 0x9c, 0x97,
0x23, 0xe8, 0x34, 0x40, 0x3b, 0x67, 0x0e, 0x75,
0xd7, 0x4a, 0xf7, 0xc6, 0x3e, 0x87, 0x97, 0x86,
0xad, 0xb8, 0x29, 0x08, 0x92, 0x60, 0xcb, 0x10,
0x6f, 0x11, 0x22, 0x5b, 0x21, 0x38, 0xa8, 0x58,
0xad, 0xf8, 0x51, 0xc1, 0xb1, 0x60, 0x3c, 0x67,
0xe9, 0xb0, 0x13, 0x01, 0x61, 0x62, 0x55, 0x35,
0x60, 0x1d, 0x85, 0x3b, 0xed, 0x8f, 0x9b, 0x5b,
0x3b, 0x8a, 0x24, 0x89, 0x88, 0x87 };
const char MBED_CLOUD_DEV_MANUFACTURER[] = "dev_manufacturer";
const char MBED_CLOUD_DEV_MODEL_NUMBER[] = "dev_model_num";
const char MBED_CLOUD_DEV_SERIAL_NUMBER[] = "0";
const char MBED_CLOUD_DEV_DEVICE_TYPE[] = "dev_device_type";
const char MBED_CLOUD_DEV_HARDWARE_VERSION[] = "dev_hardware_version";
const uint32_t MBED_CLOUD_DEV_MEMORY_TOTAL_KB = 0;
const uint32_t MBED_CLOUD_DEV_BOOTSTRAP_DEVICE_CERTIFICATE_SIZE = sizeof(MBED_CLOUD_DEV_BOOTSTRAP_DEVICE_CERTIFICATE);
const uint32_t MBED_CLOUD_DEV_BOOTSTRAP_SERVER_ROOT_CA_CERTIFICATE_SIZE = sizeof(MBED_CLOUD_DEV_BOOTSTRAP_SERVER_ROOT_CA_CERTIFICATE);
const uint32_t MBED_CLOUD_DEV_BOOTSTRAP_DEVICE_PRIVATE_KEY_SIZE = sizeof(MBED_CLOUD_DEV_BOOTSTRAP_DEVICE_PRIVATE_KEY);
#endif //__MBED_CLOUD_DEV_CREDENTIALS_H__